Howto Setup Cisco Router Auxiliary,Console and Telnet Passwords
Monday, April 13, 2009There are five passwords used to secure your Cisco routers: console, auxiliary, telnet (VTY),enable password, and enable secret. Just as you learned earlier in the chapter, the first two passwords are used to set your enable password that’s used to secure privileged mode. This will prompt a user for a password when the enable command is used. The other three are used to configure a password when user mode is accessed either through the console port, through the auxiliary port, or via Telnet.
Cisco Router Auxiliary Password Setup
To configure the auxiliary password, go into global configuration mode and type line aux ?.You can see here that you only get a choice of 0–0 (that’s because there’s only one port)
Router#config t
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#line aux ?
<0-0> First Line number
Router(config)#line aux 0
Router(config-line)#login
Router(config-line)#password admin
It’s important to remember the login command, or the auxiliary port won’t prompt for authentication.Now watch what happens when you try to set the Aux on the “newer” IOS that Cisco has released
2600A#config t
Enter configuration commands, one per line. End with CNTL/Z.
2600A(config)#line aux 0
2600A(config-line)#login
% Login disabled on line 65, until ‘password’ is set
2600A(config-line)#
Cisco has begun this process of not letting you set the “login” command before a password is set on a line because if you set the login command under a line, and then don’t set a password, the line won’t be usable. And it will prompt for a password that doesn’t exist. So this is a good thing—a feature, not a hassle!
Cisco Router Console Password Setup
To set the console password, use the line console 0 command. But look at what happened when I tried to type line console 0 ? from the aux line configuration—you should received an error.You can still type line console 0 and it will accept it, but the help screens just don’t work from that prompt. Type exit to get back one level and you’ll find that your help screens now work. This is a “feature.” Really.
Example
Router(config-line)#line console ?
% Unrecognized command
Router(config-line)#exit
Router(config)#line console ?
<0-0> First Line number
Router(config)#line console 0
Router(config-line)# password admin1
Router(config-line)# login
Since there’s only one console port, you can only choose line console 0. You can set all your line passwords to the same password, but for security reasons, I’d recommend that you make them different.
There are a few other important commands to know for the console port.
For one, the exec-timeout 0 0 command sets the timeout for the console EXEC session to zero, which basically means to never time out. The default timeout is 10 minutes. (If you’re feeling mischievous, try this on people at work: Set it to 0 1. That will make the console time out in 1 second! And to fix it, you have to continually press the Down arrow key while changing the timeout time with your free hand!)
logging synchronous is a very cool command, and it should be a default command, but it’s not. It stops annoying console messages from popping up and disrupting the input you’re trying to type. The messages still pop up, but you are returned to your router prompt without your input interrupted. This makes your input messages oh-so-much easier to read.
Here’s an example of how to configure both commands
Router(config)#line con 0
Router(config-line)#exec-timeout ?
<0-35791> Timeout in minutes
Router(config-line)#exec-timeout 0 ?
<0-2147483> Timeout in seconds
Router(config-line)#exec-timeout 0 0
Router(config-line)#logging synchronous
Cisco Router Telnet Password Setup
To set the user-mode password for Telnet access into the router, use the line vty command. Routers that aren’t running the Enterprise edition of the Cisco IOS default to five VTY lines, 0 through 4. But if you have the Enterprise edition, you’ll have significantly more. The best way to find out how many lines you have is to use that question mark
Router(config-line)#line vty 0 ?
<1-4> Last Line Number
Router(config-line)#line vty 0 4
Router(config-line)# password admin2
Router(config-line)# login
You may or may not have to set the login command before the password on the VTY lines—depends on the IOS version. The result is the same either way.
So what will happen if you try to telnet into a router that doesn’t have a VTY password set? You’ll receive an error stating that the connection is refused because, well, the password isn’t set. So, if you telnet into a router and receive this message
Router#telnet SFRouter
Trying SFRouter (10.0.0.1)…Open
Password required, but none set
[Connection to SFRouter closed by foreign host]
Router#
then the remote router (SFRouter in this example) does not have the VTY (telnet) password set. But you can get around this and tell the router to allow Telnet connections without a password by using the no login command
Router(config-line)#line vty 0 4
Router(config-line)#no login
After your routers are configured with an IP address, you can use the Telnet program to configure and check your routers instead of having to use a console cable. You can use the Telnet program by typing telnet from any command prompt (DOS or Cisco).
Mikrotik HTB Concept
Theory
From wiki.mikrotik.com
Structure
Hierarchical Token Bucket (HTB) allows to create a hierarchical queue structure and determine relations between queues, like “parent-child” or “child-child”.
As soon as queue has at least one child it becomes a inner queue, all queues without children - leaf queues. Leaf queues make actual traffic consumption, Inner queues are responsible only for traffic distribution. All leaf queues are treated on equal basis.
In RouterOS it is necessary to specify parent option to assign queue as a child to other queue
Dual Limitation
Each queue in HTB has two rate limits:
- CIR (Committed Information Rate) – (limit-at in RouterOS) worst case scenario, flow will get this amount of traffic no matter what (assuming we can actually send so much data)
- MIR (Maximal Information Rate) – (max-limit in RouterOS) best case scenario, rate that flow can get up to, if there queue’s parent has spare bandwidth
In another words, at first limit-at (CIR) of the all queues will be satisfied, only then child queues will try to borrow the necessary data rate from their parents in order to reach their max-limit (MIR).
Note: CIR will be assigned to the corresponding queue no matter what. (even if max-limit of the parent is exceeded)
That is why, to ensure optimal (as designed) usage of dual limitation feature, we suggest to stick to these rules:
- Sum of committed rates of all children must be less or equal to amount of traffic that is available to parent.
-
- CIR(parent)* ≥ CIR(child1) +…+ CIR(childN)
- *in case if parent is main parent CIR(parent)=MIR(parent)
- CIR(parent)* ≥ CIR(child1) +…+ CIR(childN)
- Maximal rate of any child must be less or equal to maximal rate of the parent
-
- MIR (parent) ≥ MIR(child1) & MIR (parent) ≥ MIR(child2) & … & MIR (parent) ≥ MIR(childN)
Queue colors in Winbox:
- 0% - 50% available traffic used - green
- 51% - 75% available traffic used - yellow
- 76% - 100% available traffic used - red
Priority
We already know that limit-at (CIR) to all queues will be given out no matter what.
Priority is responsible for distribution of remaining parent queues traffic to child queues so that they are able to reach max-limit
Queue with higher priority will reach its max-limit before the queue with lower priority. 8 is the lowest priority, 1 is the highest.
Make a note that priority only works:
- for leaf queues - priority in inner queue have no meaning.
- if max-limit is specified (not 0)
Examples
In this section we will analyze HTB in action. To do that we will take one HTB structure and will try to cover all the possible situations and features, by changing the amount of incoming traffic that HTB have to recycle. and changing some options.
Structure
Our HTB structure will consist of 5 queues:
- Queue01 inner queue with two children - Queue02 and Queue03
- Queue02 inner queue with two children - Queue04 and Queue05
- Queue03 leaf queue
- Queue04 leaf queue
- Queue05 leaf queue
Queue03, Queue04 and Queue05 are clients who require 10Mbps all the time Outgoing interface is able to handle 10Mbps of traffic.
Example 1 : Usual case
- Queue01 limit-at=0Mbps max-limit=10Mbps
- Queue02 limit-at=4Mbps max-limit=10Mbps
- Queue03 limit-at=6Mbps max-limit=10Mbps priority=1
- Queue04 limit-at=2Mbps max-limit=10Mbps priority=3
- Queue05 limit-at=2Mbps max-limit=10Mbps priority=5
Result of Example 1
- Queue03 will receive 6Mbps
- Queue04 will receive 2Mbps
- Queue05 will receive 2Mbps
- Clarification: HTB was build in a way, that, by satisfying all limit-ats, main queue no longer have throughput to distribute
Example 2 : Usual case with max-limit
- Queue01 limit-at=0Mbps max-limit=10Mbps
- Queue02 limit-at=4Mbps max-limit=10Mbps
- Queue03 limit-at=2Mbps max-limit=10Mbps priority=3
- Queue04 limit-at=2Mbps max-limit=10Mbps priority=1
- Queue05 limit-at=2Mbps max-limit=10Mbps priority=5
Result of Example 2
- Queue03 will receive 2Mbps
- Queue04 will receive 6Mbps
- Queue05 will receive 2Mbps
- Clarification: After satisfying all limit-ats HTB will give throughput to queue with highest priority.
Example 3 : Inner queue limit-at
- Queue01 limit-at=0Mbps max-limit=10Mbps
- Queue02 limit-at=8Mbps max-limit=10Mbps
- Queue03 limit-at=2Mbps max-limit=10Mbps priority=1
- Queue04 limit-at=2Mbps max-limit=10Mbps priority=3
- Queue05 limit-at=2Mbps max-limit=10Mbps priority=5
Result of Example 3
- Queue03 will receive 2Mbps
- Queue04 will receive 6Mbps
- Queue05 will receive 2Mbps
- Clarification: After satisfying all limit-ats HTB will give throughput to queue with highest priority. But in this case inner queue Queue02 had limit-at specified, by doing so, it reserved 8Mbps of throughput for queues Queue04 and Queue05. From these two Queue04 have highest priority, that is why it gets additional throughput.
Example 4 : Leaf queue limit-at
- Queue01 limit-at=0Mbps max-limit=10Mbps
- Queue02 limit-at=4Mbps max-limit=10Mbps
- Queue03 limit-at=6Mbps max-limit=10Mbps priority=1
- Queue04 limit-at=2Mbps max-limit=10Mbps priority=3
- Queue05 limit-at=12Mbps max-limit=15Mbps priority=5
Result of Example 4
- Queue03 will receive ~3Mbps
- Queue04 will receive ~1Mbps
- Queue05 will receive ~6Mbps
- Clarification: Only by satisfying all limit-ats HTB was forced to allocate 20Mbps - 6Mbps to Queue03, 2Mbps to Queue04, 12Mbps to Queue05, but our output interface is able to handle 10Mbps. As output interface queue is usually FIFO throughput allocation will keep ratio 6:2:12 or 3:1:6
SSH BruteForce Attack
This capture ip Brute Force otentikasi service SSH on Port 22, using Broadband ADSL, with PortForwarding on Modem ADSLnya to Router Mikrotik. port 22 we move to 222
Firewall pada mikrotik diproses berurutan dari Atas ke Bawah, biasanya bagi yang baru memakai Mikrotik, dengan settingan Firewall Filternya kopi pastean, sering tidak urut. Membuat proses filter ini tidak berhasil.
add chain=input protocol=tcp dst-port=22 src-address-list=ssh_blacklist \
action=drop comment="Drop SSH brute forcers" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage3 action=add-src-to-address-list \
address-list=ssh_blacklist address-list-timeout=1w3d comment="" \
disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage2 action=add-src-to-address-list \
address-list=ssh_stage3 address-list-timeout=1m comment="" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage1 action=add-src-to-address-list \
address-list=ssh_stage2 address-list-timeout=1m comment="" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new \
action=add-src-to-address-list address-list=ssh_stage1 \
address-list-timeout=1m comment="" disabled=no
Speedy Error Message
Saturday, April 11, 2009Error 678
Follow this steps :
Step 1: Turn On Modem ADSL
1.See adsl modem ON (Not blinking) before you dial
Step 2 : Reset winsock TCP/IP
1.Click start -> Click Run -> tipe netsh winsock reset and than enter
2.When command prompt window up again, restart computer
3.Try ping to Modem and Try connection diaol again.
Step 3: setting Modem adsl
1.Login to Gateway Modem via Browser exp: 192.168.1.1
Pic : VPI : 8 / VCI : 81 (for Bandung)
- Encapsulation : LLC
- Type Koneksi : Bridge
2 . If Not Work try to Reset you Modem and setting adsl Ruter again.
ERROR 769
Chek LAN computer:
1. Click start menu
2. Click Control Panel
3. Click Network Connection
- Click Local Area Connection
- - -> Click Right and than ENABLE.
Error 619/691 Dial Broadband
remplaza_fecha(’8:41 AM’);
ERROR 619/691
Try Create New Connection at computer :
1.Click start menu
2.Click Control Panel
3.Click Network Connection

5. Clcik connect to the internet àNEXT

7. Click connect using a broadband connection that requires a username and password -> NEXT
8.ISP Name:speedy -> NEXT
9.Username:1311XXXXXX@telkom.net
10.Check list Add a shortcut to this connection to my dekstop.
11.Click Finish.
12.Click icon speedy at dekstop
This can be resolved by following these steps:
· Restart your computer and wait until all applications have completely loaded before trying to reconnect.
· If your problem has still not been resolved uninstall and reinstall your Broadband modem. For information on how to do this please refer to the ADSL modem setup instructions or the installation cd that was provided with your modem
Usually this is a one-off glitch which happens when the Connection Progress is interrupted by the user or another program on the PC. In order to resolve this:
· Restart your computer and wait until all applications have completely loaded before trying to reconnect.
Error 633 -The port is already in use / not configured for Remote Access Dialout
remplaza_fecha(’3:11 PM’);
This error can be best remedied by: · A restart of your computer tends to resolve 50% of cases with this error message · Disable any Firewall Software and try to connect again… · Try uninstalling and reinstalling the Modem. For information on how to do this please refer to the ADSL modem setup instructions or the installation cd that was provided with your modem.
Error 645 - Internal Authentication Error
This problem tends to occur when using Windows 98 or Windows ME. This can be resolved by following these steps:
· Try uninstalling and reinstalling the Modem. For information on how to do this please refer to the ADSL modem setup instructions or the installation cd that was provided with your modem.
· Windows 95/98 - This error can occur if the ‘Require encrypted password’ option is enabled on the ‘Server Types’ tab in the connection’s properties, or an incorrect user name or password have been entered. See MS KB Article Q199780
· All versions of Windows - This error can occur if you are attempting to connect to a Windows 2000 domain that has had a RRAS (Routing and Remote Access Services) server log on without administrative privileges. See MS KB Article 227747
Error 651 - Your modem has reported an error
remplaza_fecha(’3:15 PM’);
This error usually occurs with Windows 2000 when the Internet connection has become corrupted. This can be resolved by following these steps:
· Try uninstalling and reinstalling the Modem. For information on how to do this please refer to the ADSL modem setup instructions or the installation cd that was provided with your modem.
Error 680 - No dial tone
remplaza_fecha(’3:19 PM’);
This error usually means there is a problem receiving the Broadband signal at your modem. An error 680 / 619 would usually also mean you do not have a solid green ADSL light on the modem. This can be resolved by following these steps:
Ensure you have checked the following:
· Does your telephone Work? (if not you may have a fault with your telephone line)
· Is the cable from the modem to the filter secure at each end?
· Are you using a home-made extension line? Broadband requires a solid copper (round) extension.
Error 680 and both modem lights are solid green
If the modem installation seems successful and you have two solid green lights on your modem but are still receiving the error message- 680: No dial tone, then:
· If you have an internal 56k modem please disable the modem as follows
o Right click on the My Computer Icon on your desktop and then select Properties
o If you have a Device Manager tab along the top select this, otherwise select the Hardware tab along the top and then click on the Device Manager button
o In the Device Manager click on the + sign on the Modem selection and then…
o Identify and right click your modem icon and select Disable / Properties and then Disable in this Hardware Profile
o After you have completed this, close down the Device Manager and then restart your computer and try to reconnect to the Broadband connection.
Error 797 - The connection failed because the modem or other connecting device failed
remplaza_fecha(’3:21 PM’);
This can be resolved by following these steps: · Restart your computer and wait until all applications have completely loaded before trying to reconnect. If your problem has still not been resolved uninstall and reinstall your Broadband modem. For information on how to do this please refer to the ADSL modem setup instructions or the installation cd that was provided with your modem
PC / Computer / Laptop Harus selalu di update antivirsu dan di scan • Cek computer from virus and spyware (with installing at computer).• example Antivirus software :– Avg free antivirus : http://free.grisoft.com– Avira antivirus : http://www.avira.com– Avast Antivirus : http://www.avast.com• Example AntiSpyware Software :– Microsoft Antispyware : http://www.Microsoft.com/OneCare– Spyware Doctor : http://www.pctools.com/spyware-doctor– Ad-aware : http://www.lavasoftusa.com• Diatas adalah beberapa Link antivirus yang bisa anda gunakan
ROUTER COMMANDS
Sunday, February 1, 2009ROUTER COMMANDS
TERMINAL CONTROLS:
· Config# terminal editing - allows for enhanced editing commands
· Config# terminal monitor - shows output on telnet session
· Config# terminal ip netmask-format hexadecimal|bit-count|decimal - changes the format of subnet masks
HOST NAME:
· Config# hostname ROUTER_NAME
BANNER:
· Config# banner motd # TYPE MESSAGE HERE # - # can be substituted for any character, must start and finish the message
VPN [Cisco Router - PPTP Server] from oprekan.wordpress.com
Monday, November 3, 20081. Configure VPDN untuk dial in VPN dari Microsoft VPN Client
RO-PPTP(config)# vpdn enable
RO-PPTP(config)# vpdn-group PPTP-DIALIN
RO-PPTP(config-vpdn)# accept-dialin
RO-PPTP(config-vpdn)# protocol pptp
RO-PPTP(config-vpdn)# virtual-template 1
RO-PPTP(config-vpdn)# exit
2. Aktifkan interface untuk IP Dial In di Microsoft VPN Client dan LAN yang
akan kita akses dari luar leat VPN ini.
RO-PPTP(config)# interface Ethernet5/0
RO-PPTP(config-if)# description DIAL-IN IP INTERFACE FROM OUTSIDE
RO-PPTP(config-if)# ip address 202.150.64.81 255.255.255.240
RO-PPTP(config-if)# no shutdown
RO-PPTP(config)# interface Ethernet5/1
RO-PPTP(config-if)# description SECURED-LAN
RO-PPTP(config-if)# ip address 192.168.0.254 255.255.255.0
RO-PPTP(config-if)# no shutdown
3. Create Virtual-template untuk sebagai virtual interface untuk diapply ke inbound VPN connections.
IP menggunakan unnunmbered E5/1 agar nantinya IP yang didapat oleh
Microsoft VPN client dalam satu subnet dengan IP Secured-LAN.
IP client diperoleh dari DHCP dari Pool Address pptp-pool (misalnya)
RO-PPTP(config)# interface Virtual-Template1
RO-PPTP(config-if)# ip unnumbered ethernet5/1
RO-PPTP(config-if)# peer default ip address pool pptp-pool
RO-PPTP(config-if)# ppp encrypt mppe auto required
(Bila Router Anda tidak support, lewatkan saja & di Micorosoft VPN client dibagian security, Require Data Encryptionnya tidak usah di check-list / centang).
RO-PPTP(config-if)# ppp authentication ms-chap ms-chap-v2 chap pap
(enable semua bila perlu chap/pap selain Microsoft)
4. Create Pool IP Address untuk VPN ‘pptp-pool’ (misal untuk 20 user / ip) & pastikan IP pool tersebut tidak dipakai di Secured-LAN
RO-PPTP(config)# ip local pool pptp-pool 192.168.0.100 192.168.0.119
5. Create Account untuk login VPN
RO-PPTP(config)# username vpdn password 0 pptp
6. Configure Autentikasi PPP vpn ini ke local (Router) atau selanjutnya ke Radius bila memang sudah available.
RO-PPTP(config)# aaa new-model
RO-PPTP(config)# aaa authentication ppp default local
Berikut Konfigurasi Lengkap (hanya vpdn saja) :
================================================
username vpdn password 0 pptp
!
aaa new-model
aaa authentication ppp default local
!
vpdn enable
!
vpdn-group PPTP-DIALIN
accept-dialin
protocol pptp
virtual-template 1
!
interface Ethernet5/0
description DIAL-IN IP INTERFACE FROM OUTSIDE
ip address 202.150.64.81 255.255.255.240
!
interface Ethernet5/1
description SECURED-LAN
ip address 192.168.0.254 255.255.255.0
!
interface Virtual-Template1
ip unnumbered Ethernet0/1
peer default ip address pool pptp-pool
ppp encrypt mppe auto required
ppp authentication ms-chap ms-chap-v2 chap pap
!
ip local pool defaultpool 192.168.0.100 192.168.0.119
================================================
ACCESS LIST (ACL)
Saturday, November 1, 2008Pengertian
- Jaringan traffic flow dan pengaruh desain keamanan manajemen jaringan computer.
- Access lists mengijinkan atau menolak pernyataan bahwa filter traffic dapat ke segmen jaringan dan dari segmen jaringan berdasarkan pada:
- Alamat sumber
- Alamat tujuan
- Tipe protocol
- Dan nomor port dari paket.
Access list adalah pengelompokan paket berdasarkan kategori. Access list bisa sangat membantu ketika membutuhkan pengontrolan dalam lalu lintas network. access list menjadi tool pilihan untuk pengambilan keputusan pada situasi ini.
Penggunaan access list yang paling umum dan paling mudah untuk dimengerti adalah penyaringan paket yang tidak diinginkan ketika mengimplementasikan kebijakan keamanan.
Sebagai contoh kita dapat mengatur access list untuk membuat keputusan yang sangat spesifik tentang peraturan pola lalu lintas sehingga access list hanya memperbolehkan host tertentu mengakses sumber daya WWW sementara yang lainnya ditolak. Dengan kombinasi access list yang benar, network manajer mempunyai kekuasaan untuk memaksa hamper semua kebijakan keamananyang bisa mereka ciptakan.
Access list juga bisa digunakan pada situasi lain yang tidak harus meliputi penolakan paket. Sebagai contoh access list digunakan untuk mengontrol network mana yang akan atau tidak dinyatakan oleh protocol dynamic routing. Konfigurasikan access list dengan cara yang sama. Perbedaannya disibni hanyalah bagaimana menerapkannya ke protocol routing dan bukan ke interface. Kita juga bisa menggunakan access list untuk mngkategorikan pakt atau antrian /layanan QOS, dan mengontrol tipe lalu lintas data nama yang akan mengaktifkan link ISDN.
Membuat access list sangat mirip dengan statement pada programming if – then jika sebuah kondisi terpenuhi maka aksi yang diberikan akan dijalankantidak terpenuhi, tidak ada yang terjadi dan statemen berikutnya akan dievaluasi. Statement ACL pada dasarnaya dalah paket filter dimana paket dibandingkan, dimana paket dikategorikan dan dimana suatu tindakan terhadap paket dilakukan.
List(daftar) yang telah dibuat bisa diterpakan baik kepada lalulintas inbound maupun outbound pada interface mana saja. Menerapkan ACL menyebabkan router menganalisa setiap paket arah spesifik yang melalui interface tersebut dan mengmbil tindakan yang sesuai.
Ketika paket dibandingkan dengan ACL, terdapat beberapa peraturan (rule) penting yang diikuti:
- Paket selalu dibandingkan dengan setiap baris dari ACL secara berurutan, sebagai contoh paket dibandingkan dengan baris pertama dari ACL, kemudian baris kedua, ketiga, dan seterusnya.
- Paket hanya dibandingkan baris-baris ACL sampai terjadi kecocokan. Ketika paket cocok dengan kondisi pada baris ACL, paket akan ditindaklanjuti dan tidak ada lagi kelanjutan perbandingan.
- Terdapat statement “tolak” yang tersembunyi (impilicit deny) pada setiap akhir baris ACL, ini artinya bila suatu paket tidak cocok dengan semua baris kondisi pada ACL, paket tersebut akan ditolak

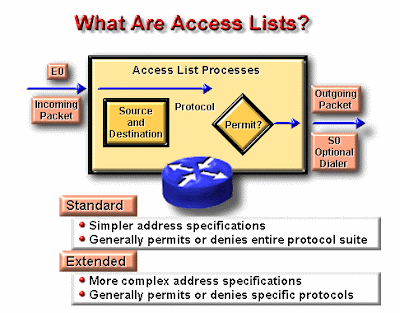
Jenis ACL
- Standard ACL
Standard ACL hanya menggunakan alamat sumber IP di dalam paket IP sebagai kondisi yang ditest. Semua keputusan dibuat berdasarkan alamat IP sumber. Ini artinya, standard ACL pada dasarnya melewatkan atau menolak seluruh paket protocol. ACL ini tidak membedakan tipe dari lalu lintas IP seperti WWW, telnet, UDP, DSP.
- Extended ACL
Extended ACL bisa mengevalusai banyak field lain pada header layer 3 dan layer 4 pada paket IP. ACL ini bisa mengevaluasi alamat IP sumber dan tujuan, field protocol pada header network layer dan nomor port pada header transport layer. Ini memberikan extended ACL kemampuan untuk membuat keputusan-keputusan lebih spesifik ketika mengontrol lalu lintas.
Jenis Lalu Lintas ACL
- Inbound ACL
Ketika sebauah ACL diterapkan pada paket inbound di sebuah interface, paket tersebut diproses melalui ACL sebelum di-route ke outbound interface. Setiap paket yang ditolak tidak bisa di-route karena paket ini diabaikan sebelum proses routing diabaikan.
- Outbond ACL
Ketika sebuah ACL diterapkan pada paket outbound pada sebuah interface, paket tersebut di-route ke outbound interface dan diproses melalui ACL malalui antrian.
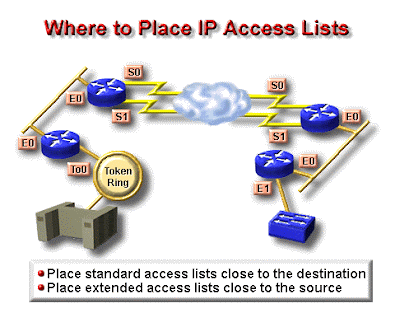
Panduan Umum ACL
Terdapat beberapa panduan umum ACL yang seharusnya diikuti ketika membuat dan mengimplementasikan ACL pada router :
- Hanya bisa menerapkan satu ACL untuk setiap interface, setiap protocol dan setiap arah. Artinya bahwa ketika membuat ACL IP, hanya bisa membuat sebuah inbound ACL dan satu Outbound ACL untuk setiap interface.
- Organisasikan ACL sehingga test yang lebih spesifik diletakkan pada bagian atas ACL
- Setiap kali terjadi penambahan entry baru pada ACL, entry tersebut akan diletakkan pada bagian bawah ACL. Sangat disarankan menggunakan text editor dalam menggunakan ACL
- Tidak bisa membuang satu baris dari ACL. Jika kita mencoba demikian, kita akan membuang seluruh ACL. Sangat baik untuk mengcopy ACL ke text editor sebelum mencoba mengubah list tersebut.
- Wildcard Masking
Wildcard masking digunakan bersama ACL untuk menentukan host tunggal, sebuah jaringan atau range tertentu dari sebuah atau banyak network. Untuk mengerti tentang wildcard, kita perlu mengerti tentang blok size yang digunkan untuk menentukan range alamat. Beberapa blok size yang berbeda adalah 4, 8, 16, 32, 64.
Ketika kita perlu menentukan range alamat, kita memilih blok size selanjutnya yang terbesar sesuai kebutuhan. Sebagai contoh, jika kita perlu menentukan 34 network, kita memerlukan blok size 64. jika kita ingin menentukan 18 host, kita memerlukan blok size 32. jiak kita perlu menunjuk 2 network, maka blok size 4 bisa digunakan. Wildcard digunakan dengan alamat host atau network untuk memberitahukan kepada router untuk difilter.
Untuk menentukan sebuah host, alamat akan tampak seperti berikut 172.16.30.5 0.0.0.0 keempat 0 mewakili setiap oktet pada alamat. Dimanapun terdapat 0, artinya oktet pada alamat tersebut harus persis sama. Untuk menentukan bahwa sebuah oktet bisa bernilai apa saja, angka yang digunakan adalah 255. sebagai contoh, berikut ini adalah subnet /24 dispesifikasikan dengan wildcard: 172.16.30.0 0.0.255 ini memberitahukan pada router untuk menentukan 3 oktet secara tepat, tapi oktet ke-4 bisa bernilai apa saja.
Standard Access List
Standard IP ACL memfilter lalu lintas network dengan menguji alamat sumber IP didalam paket. Kita membuat standard IP ACL dengan menggunakan nomor ACL 1-99 atau 1300-1999(expanded range).Tipe ACL pada ummnya dibedakan berdasarkan nomor yang digunakan ketika ACL dibuat, router akan mengetahui tipe syntax yang diharapkan untuk memesukkan daftar.
Dengan menggunakan nomor 1-99 atau 1300-1999, kita memberitahukan kepada router bahwa kita ingin membuat IPACL, jadi router akan mengharapkan syntax yang hana menspesifikasikan alamat sumber IP pada baris pengujian.
Banyak range nomor ACL pada contoh dibawah ini yang bisa kita gunakan untuk memfilter lalu lintas pada jaringan kita (protocol yang bisa kita terapkan ACL bisa tergantung pada versi IOS kita) :
Contoh Standard ACL
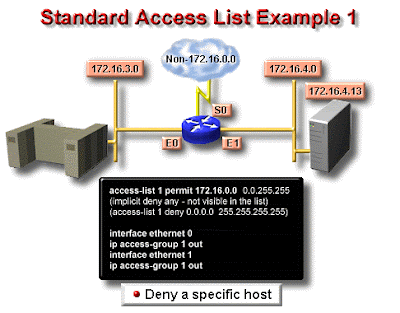
Standard ACL untuk menghentikan user tertentu mendapatkan akses ke LAN Department Finance.
Pada gambar, router mempunyai 3 koneksi LAN dan 1 koneksi WAN ke internet. User pada LAN Sales tidak boleh mempunyai akses ke LAN finance, tapi mereka boleh mengakses internet dan Department Marketing.
LAN Marketing perlu mengakses LAN Finance untuk layanan aplikasi
Pada router yang digambar, standard IP ACL berikut dikonfigurasi :
Lab_A#config t
Lab_A(config)#access -list 10 deny 172.16.40.0 0.0.0.255
Lab_A(config)#access-list 10 permit any
Sangatlah penting untuk diketahui bahwa perintah any sama halnya dengan menggunakan wildcard masking berikut :
Lab_A(config)#access-list 10 permit 0.0.0.0 255.255.255.255
Karena wildcard mask menyatakan bahwa tidak ada oktet yang diperiksa, setiap alamat akan sesuai dengan kondisi test. Jadi fungsi ini sama dengan penggunaan kata any. Saat ini, ACL dikonfigurasi untuk menolak alamat sumber dari LAN sales yang mengakses LAN finance, dan memperbolehkan dari akses yang lain. Tetapi untuk diingat, tidak ada tindakan yang diambil sampai akses list diterapkan pada arah yang spesifik. Tetapi dimana ACL ini seharusnya ditempatkan? Jika kita menempatkannya pada E0, kita mungkin akan mematikan juga interface Ethernet karena semua peralatan LAN Sales akan ditolak akses ke semua network yang terhubung ke router.
Tempat terbaik untuk menerapkan ACL ini adalah pada E1 sebagai outbound list:
Lab_A(config)#Int E1
Lab_A(config-if)#ip access-group 10 out
Ini menghentikan secara tuntas lalu lintas 172.16.40.0 keluar dari Ethernet 1. Ini tidak ada pengarujnya terhadap host dari LAN Sales yang mengakses LAN marketing dan internet, karena lalu lintas ke tujuan tersebut tidak melalui interface E1. Setiap paket yang mencoba keluar dari E1 harus melalui ACL terlebih dahulu. JIka terdapat inbound lit yang ditempatkan pada E0, maka setiap paket yang mancoba masuk ke interface E0 akan harus melalui ACL terlebih dahulu sebelum di route ke interface keluar.
Keistimewaan Standard Access List
Software Cisco IOS dapat memprovide pesan logging tentang paket – paket. Yang diijinkan atau ditolak oleh standard IP access list. Itulah sebabnya beberapa paket dapat cocok dengan access list.yang disebabkan oleh informasi pesan logging.tentang paket yang telah dikirimkan ke console. Level dari pesan logging ke console yang dikendalikan oleh perintah logging console.Kemampuan ini hanya terdapet pada extended IP access lists.
Triggers paket pertama access list menyebabkan logging message yang benar, dan paket – paket berikutnya yang dikunpulkan lebih dari interval 5-menit sebelum ditampilkan. Pesan logging meliputi nomor access list, apakah paket tersebut diterima atau ditolak, alamat IP sumber dari paket dan nomor asal paket yang diterima sumber atau ditolak dalam interval 5 menit.
KEUNTUNGAN
Kita dapat memantau berapa banyak paket yang diijinkan atau ditolak oleh access list khusus termasuk alamat tujuan setiap paket.
Membuat Standard Access List Menggunakan Nomor
Untuk membuat nomor standard access list dan menerima pesan logging, ditampilkan dalam mode global konfigurasi, sebagai berikut :
Membuat Standard Access List Menggunakan Nama
Untuk membuat nama standard access list dan menerima pesan logging, berikut adalah permulaan dalam mode global konfigurasi.
Untuk mendefinisikan standard IP access list dengan nomor, menggunakan standard version dari acess-list ration untuk memindahkan sebuah standard access list, maka digunakan perintah berikut :
access-list access-list-number {deny permit} source [source-wildcard] [log] no access-list access-list-number
Extended ACL
Extended ACL bisa mengevaluasi banyak field lain pada header layer 3 dan layer 4 pada paket IP. ACL ini bisa mengevaluasi IP sumber dan tujuan, field protocol dalam network header Network Layer dan nomor port pada Transport Layer. Ini memberikan extended ACL kemampuan untuk membuat keputusan – keputusan lebih spesifik ketika mengontrol lalu lintas.
Pada contoh Standard ACL, perhatikan bagaimana kita harus memblok semua akses dari LAN Sales ke Department Finance. Bagaimana jika untuk urusan keamanan, kita membutuhkan Sales mendapatkan akses ke server tertentu pada LAN Finance tapi tidak ke layanan network lainnya ? Dengan standard IP ACl, kita tidak memperbolehkan user mendapat satu layanan sementara tidak untuk yang lainnya. Dengan kata lain, ketika kita membutuhkan membuat keputusan berdasarkan alamat sumber dan tujuan, standard ACL tidak memperbolehkan kita melakukannya karena ACL ini hanya mambuta kaputusan berdasrkan alamat sumber. Tetapi extended ACl akan membantu kita karena extended ACL memperbolehkan kita menentukan alamat sumber dan tujuan serta protocol dan nomor port yang mengidentfikasikan protocol upper layer atau aplikasi. Dengan menggunakan extended ACL kita bisa secara efisien memperbolehkan user mengakses ke fisik LAN dan menghentikan host tertentu atau bahkan layanan tertentu pada host tertentu.
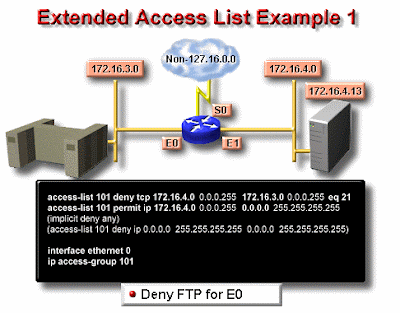
Contoh Extended Access List
Layanan lain pada host ini dan host lainnya bisa diakses oleh departertmen seles dan marketing. Berikut adalah access list yang dibuat:
Lab_A#config t
Lab_A(config)#access-list 110 deny tcp any host 172.16.30.5 eq 21
Lab_A(config)#access-list 110 deny tcp any host 172.16.30.5 eq 23
Lab_A(config)#access-list 110 permit ip any any
Access list 110 memberitahukan ke router bahwa anda membuat Extended IP Access List. TCP adalah field procol pada heather layer network. Jika pada list tidak terdapat TCP disini, anda tidak bisa menyaring berdasarkan nomor port 21 dan 23 seperti yang diperlihatkan pada contoh (yaitu FTP dan Telnet dan keduanya menggunakan TCP untuk layanan conection - oriented). Perintah any disini adalah sumber, yang berarti semua alamat IP dan host adalah alamat IP tujuan. Setelah list dibuat, maka selanjutnya perlu diterapkan pada outbound interface ethernet 1.
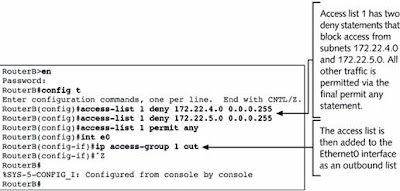
- Hukum Access List
- Daftar aplikasi router secara berurutan menunjukan apa yang ditulis ke daalm router.
- Daftar aplikasi router untuk paket yang berurutan.
- Packet akan diproses jika cocok dan berdasarkan criteria access list termasuk pernyataan access list.
- Implicit deny any
- Semua paket yang tidak memenuhi syarat dari acces list akan di blok oleh perintah permit any yang digunakan pada akhir list.
- Hanya satu list, per protocol, per perintah yang dapat diaplikasikan pada interface.
- Kita tidak dapat memindahkan satu baris dari access list.
- Access list akan efektif segera setelah diaplikasikan.
Deskripsi Syntax
Beberapa bentuk fungsi access Lists dengan cisco router, meliputi
- Implementasi keamanan prosedur access
- Seperti [ada protocol firewall
PPP with CHAP Authentication
PPP with CHAP Authentication
PPP (Point-to-Point Protocol)
PPP (Point-to-Point Protocol) is a protocol for communication between two computers using a serial interface, typically a personal computer connected by phone line to a server. For example, your Internet server provider may provide you with a PPP connection so that the provider's server can respond to your requests, pass them on to the Internet, and forward your requested Internet responses back to you. PPP uses the Internet protocol (IP) (and is designed to handle others). It is sometimes considered a member of the TCP/IP suite of protocols. Relative to the Open Systems Interconnection (OSI) reference model, PPP provides layer 2 (data-link layer) service. Essentially, it packages your computer's TCP/IP packets and forwards them to the server where they can actually be put on the Internet.
PPP is a full-duplex protocol that can be used on various physical media, including twisted pair or fiber optic lines or satellite transmission. It uses a variation of High Speed Data Link Control (HDLC) for packet encapsulation.
PPP is usually preferred over the earlier de facto standard Serial Line Internet Protocol (SLIP) because it can handle synchronous as well as asynchronous communication. PPP can share a line with other users and it has error detection that SLIP lacks. Where a choice is possible, PPP is preferred.
CHAP (Challenge-Handshake Authentication Protocol)
CHAP (Challenge-Handshake Authentication Protocol) is a more secure procedure for connecting to a system than the Password Authentication Procedure (PAP). Here's how CHAP works:
After the link is made, the server sends a challenge message to the connection requestor. The requestor responds with a value obtained by using a one-way hash function.
The server checks the response by comparing it its own calculation of the expected hash value.
If the values match, the authentication is acknowledged; otherwise the connection is usually terminated.
At any time, the server can request the connected party to send a new challenge message. Because CHAP identifiers are changed frequently and because authentication can be requested by the server at any time, CHAP provides more security than PAP. RFC1334 defines both CHAP and PAP.
Configuring PPP w/CHAP on a Cisco Router
The interface command to enable ppp is:
encapsulation ppp
Place this on both ends and that is it. However, to enable authentication, we need to add the interface command
ppp authentication chap
to both routers, the routers will now require authentication over the link. They will attempt to log in with their HOSTNAME as their USERNAME and their ENABLE password as their chap PASSWORD. We must create an entry in the router that matches the remote routers username and password (global config):
username Other_Router password Other_enable_pass
That is all their is to basic PPP.
Our Samples:
(R1)s0----------s0(R2)
PPP Without CHAP
Router 1:
hostname R1
interface serial 0
encapsulation PPP
no shutdown
Router 2:
hostname R2
interface serial 0
encapsulation PPP
no shutdown
PPP With CHAP default names and password
Router 1:
hostname R1
enable secret toast1
username R2 password cool2
interface serial 0
encapsulation PPP
ppp authentication chap
no shutdown
Router 2:
hostname R2
enable secret cool2
username R1 password toast1
interface serial 0
encapsulation PPP
ppp authentication chap
no shutdown
Copyright (c) 2001 Boson Software, Inc. All Rights Reserv
Interior Gateway Routing Protocol (IGRP)
P Addresses: Please set these IP addresses on the interfaces of your routers.
Router1 Router2 Router4
Interface Ethernet 0 10.1.1.1 255.255.255.0 10.1.1.2 255.255.255.0 Not Available
Interface Serial 0 172.16.10.1 255.255.0.0 Not Available 172.16.10.2 255.255.0.0
Lets connect to Router1 and get it configured. We will be using the table above for our IP addresses.
IGRP is classful, meaning it does not include the subnet mask in its routing table updates. So now lets go ahead and start the lab.
1. We first want to configure Router1 for IGRP. To enable IGRP as the routing protocol we only need to type: router IGRP AS. The AS stands for a Autonomous System number. An Autonomous System is defined as a network under a common administration with a common routing policy. You will need to use the SAME autonomous system number on every router that you would like to share its routing table with. We can see this below in the router output. Notice the new mode we have entered
Router1(config)#router IGRP 100
Now that we have IGRP running on our Router we need to tell the router which networks it is connected to. We do this by using the network statement. What this means is every interface of our router that is directly connected to an active network needs a network number. We will have some networks using the same ip addressing schemes with different subnets, and some are using entirely different addressing schemes. Look at the diagram below. In this diagram we have three different kinds of addressing schemes. Lets look at these in more detail. On Router 1 we have an IP address of 10.1.1.1 with a /24 subnet mask. Since IGRP is classful you are only required to enter the class part of the address for the network statement. For example on Router1 we have already issued the command router IGRP, we then need to specify the directly connected networks to Router1 so the router can advertise these routes in its routing table. To do this we would only need to type: network 10.0.0.0 now we have not told the router about the network on his serial interface, to do this we would type: network 172.16.0.0 Lets look at Router 2 what network statement would we need to use on this router ______________________________________(see the answer below the diagram.)
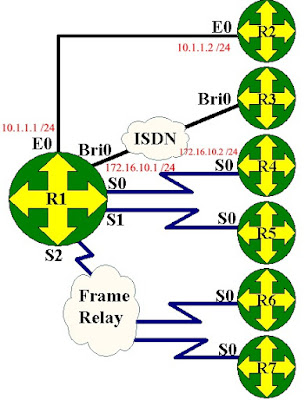
The answer is network 10.0.0.0. The network statement for the ethernet link is the same for Router1 and Router2. On router1 what network statement would you need for the serial link? For this network statement you used the classful portion of the address 172.16.10.1 which would be just network 172.16.0.0.
Now that we understand the network command lets enter it on our Router1.
Router1(config-router)#network 172.16.0.0
If you notice we only needed to enter 10.0.0.0 for our network statement, this is because 10.0.0.0 is a Class B address and IGRP only uses the classful portion of the address. Now we have configured Router1 for IGRP lets connect to Router2 and get it setup.
We need to connect to Router2 and follow the same instructions. Lets select Router2 from the Window pull down menu. When we connect we are going to set a hostname to Router2, then set the ip addresses to the table above and configure IGRP.
Router>en
Now add the IGRP stuff!
Router2(config)#router IGRP 100
We should now have IGRP running on our network between Router1 and Router2. We need to get Router4 setup.
We need to connect to Router4 and follow the same instructions. Lets select Router4 from the Window pull down menu. When we connect we are going to set a hostname to Router4, then set the ip addresses to the table above and configure IGRP.
Router>en
Now add the IGRP stuff!
Router4(config)#router IGRP 100
Now that we have IGRP running on our entire network lets verify that it is receiving routes. To do this we will be using some show commands. The most common one is show ip route. This displays all entries in the routing table. If we do this on our Router B we will see the route to our directly connected Router1. Lets take a look at our routing table, to do this type: show ip route from the privilege mode.
Lets look at the first entry I 10.1.1.0/24 [100/1] via 172.16.10.2, 00:00:21, Serial0. It starts off with I this says it is a IGRP route it then says the destination network with sunbet mask in this case it is 10.1.1.0 with a /24 (255.255.255.0) subnet mask. Next it gives 100/1 the 100 is the administrative distance, IGRP's default administrative distance is 100. Administrative distance is considered the trustworthiness of the route. If you have two routing protocols with the same route the router will pick the route with the lower number. The 1 is the hops required to get to the destination network. The next piece of information is the via 172.16.10.1 that is the next hop address it must go to. The last item is that this information was learned via Serial0.
Another great command is show ip protocols. This displays information about the ip routing protocols you have enabled. Lets type the command : show ip protocols and see what we get.
Router4#show ip protocols
Looking at the output in detail we see we are sending updates every 90 seconds. We know IGRP is a distance vector routing protocol so it exchanges its entire routing table every 90 seconds. We also see our network statements are working by noticing the networks are both under the Routing for Networks area. The last area to notice is the Distance which we said was administrative distance. This tells us the default is 100 and that is what we are using.
Conclusion:
In this lab we have configured our routers for IGRP so that we can exchange information with more than the directly connected neighbor. We have learned that IGRP's metric is hop count and the routers send updates every 30 seconds be default. Now in the next lab we will go into IGRP (Interior Gateway Routing Protocol).
Copyright (c) 2001 Boson Software, Inc. All Rights Reserved.
ROUTING INFORMATION PROTOCOL
IP Addresses: Please set these IP addresses on the interfaces of your routers.
Router1 Router2 Router4
1) Set our hostname and get our interfaces up.
2) Configure Rip routing protocol
3) Select the directly connected networks
4) View our routing table
5) View the Rip protocol information
6) Observe Rip debugging information
--------------------------------------------------------------------------------
Routing Information Protocol (RIP) is a standards-based, distance-vector, interior gateway protocol (IGP) used by routers to exchange routing information. RIP uses hop count to determine the best path between two locations. Hop count is the number of routers the packet must go through till it reaches the destination network. The maximum allowable number of hops a packet can traverse in an IP network implementing RIP is 15 hops. In a RIP network, each router broadcasts its entire RIP table to its neighboring routers every 30 seconds. When a router receives a neighbor's RIP table, it uses the information provided to update its own routing table and then sends the updated table to its neighbors. This procedure is repeated by each router and results in a state referred to as network convergence, in which all routers have an identical view of the internetwork topology.
Lets connect to Router1 and get it configured. We will be using the table above for our IP addresses.
Router>en
RIP version 1 is classful, meaning it does not include the subnet mask in its routing table updates. RIP version 2 is classless and includes the subnet information. Now lets go ahead and start the lab.
1. We first want to configure Router1 for RIP. To enable RIP as the routing protocol we only need to type: router rip We can see this below in the router output. Notice the new mode we have entered
Router1(config)#router rip
Now that we have RIP running on our Router we need to tell the router which networks it is connected to. We do this by using the network statement. What this means is every interface of our router that is directly connected to an active network needs a network number. We will have some networks using the same ip addressing schemes with different subnets, and some are using entirely different addressing schemes. Look at the diagram below. In this diagram we have three different kinds of addressing schemes. Lets look at these in more detail. On Router 1 we have an IP address of 10.1.1.1 with a /24 subnet mask. Since RIP is classful you are only required to enter the class part of the address for the network statement. For example on Router1 we have already issued the command router rip, we then need to specify the directly connected networks to Router1 so the router can advertise these routes in its routing table. To do this we would only need to type: network 10.0.0.0 now we have not told the router about the network on his serial interface, to do this we would type: network 172.16.0.0 Lets look at Router 2 what network statements do you would need to use on this router
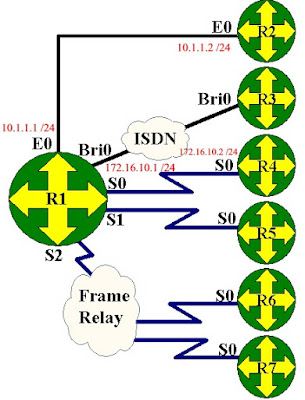
The answers are network 10.0.0.0. The network statement for the serial link is the same for Router1 and Router2. For the network statement for the ethernet link you had to remember that a 192 address was a class C address, for this network statement you used the classful portion of the address 192.168.1.0.
Now that we understand the network command lets enter it on our Router1.
Router1(config-router)#network 172.16.0.0
If you notice we only entered 10.0.0.0 for our network statement, this is because 10.0.0.0 is a Class B address and rip only uses the classful portion of the address. Now we have configured Router1 for RIP lets connect to Router2 and get it setup.
We need to connect to Router2 and follow the same instructions. Lets select Router2 from the Window pull down menu. When we connect we are going to set a hostname to Router2, then set the ip addresses to the table above and configure RIP.
Router>en
Now add the RIP stuff!
Router2(config)#router rip
We need to connect to Router4 and follow the same instructions. Lets select Router4 from the Window pull down menu. When we connect we are going to set a hostname to Router4, then set the ip addresses to the table above and configure RIP.
Router>en
Now add the RIP stuff!
Router4(config)#router rip
Now that we have RIP running on our entire network lets verify that it is receiving routes. To do this we will be using some show commands. The most common one is show ip route. This displays all entries in the routing table. If we do this on our Router 4 we will see the route to our directly connected Router1, we will also see routes to the other routers we have setup on the network. Lets take a look at our routing table, to do this type: show ip route from the privilege mode.
Lets look at the first entry R 10.1.1.0/24 [120/1] via 172.16.10.2, 00:00:21, Serial0. It starts off with R this says it is a Rip route it then says the destination network with sunbet mask in this case it is 10.1.1.0 with a /24 (255.255.255.0) subnet mask. Next it gives 120/1 the 120 is the administrative distance, Rip's default administrative distance is 120. Administrative distance is considered the trustworthiness of the route. If you have two routing protocols with the same route the router will pick the route with the lower number. The 1 is the hops required to get to the destination network. The next piece of information is the via 172.16.10.1 that is the next hop address it must go to. The last item is that this information was learned via Serial0.
Another great command is show ip protocols. This displays information about the ip routing protocols you have enabled. Lets type the command : show ip protocols and see what we get.
Router4#show ip protocols
Router4#
Looking at the output in detail we see we are sending updates every 30 seconds. We know Rip is a distance vector routing protocol so it exchanges its entire routing table every 30 seconds. We also see our network statements are working by noticing the networks are both under the Routing for Networks area. The last area to notice is the Distance which we said was administrative distance. This tells us the default is 120 and that is what we are using.
Conclusion:
In this lab we have configured our routers for RIP so that we can exchange information with more than the directly connected neighbor. We have learned that RIP's metric is hop count and the routers send updates every 30 seconds be default. Now in the next lab we will go into IGRP (Interior Gateway Routing Protocol).
Copyright (c) 2001 Boson Software, Inc. All Rights Reserved.













