Queue with Masquerading and Internal Web-Proxy
Saturday, December 8, 200701. Introduction
This page will tak about how to make QUEUE TREE in RouterOS that also running
Web-Proxy and Masquerading. Several topics in forum say it's impossible to do.
In version 2.9.x, we can not know which traffic is HIT and which traffic is MISS
from web-proxy. Several people want to make a configuration, to let cache data in
proxy (HIT traffic) deliver in maximum possible speed. In other word, if we already
have the requested data, those process will not queued.
In ver 3.0 we can do this, using TOS header modification in web-proxy feature.
We can set any TOS value for the HIT traffic, and make it as parameter in mangle.
02. Basic Setup
First, let's set the basic setting first. I'm using a machine with 2 network
interface:
---------------------------------------------------------------------------------
admin@instaler] > in pr
# NAME TYPE RX-RATE TX-RATE MTU
0 R public ether 0 0 1500
1 R lan wlan 0 0 1500
---------------------------------------------------------------------------------
And this is the IP Address for each interface:
---------------------------------------------------------------------------------
[admin@instaler] > ip ad pr
Flags: X - disabled, I - invalid, D - dynamic
# ADDRESS NETWORK BROADCAST INTERFACE
0 192.168.0.217/24 192.168.0.0 192.168.0.255 public
1 172.21.1.1/24 172.21.1.0 172.21.1.255 lan
---------------------------------------------------------------------------------
Don't forget to set the transparant web-proxy. We set cache-hit-dscp: 4.
---------------------------------------------------------------------------------
[admin@instaler] > ip proxy pr
enabled: yes
src-address: 0.0.0.0
port: 3128
parent-proxy: 0.0.0.0
parent-proxy-port: 0
cache-drive: system
cache-administrator: "webmaster"
max-cache-size: none
cache-on-disk: yes
maximal-client-connections: 600
maximal-server-connections: 600
max-fresh-time: 3d
serialize-connections: yes
cache-hit-dscp: 4
---------------------------------------------------------------------------------
03. Firewall NAT
Make 2 NAT rules, 1 for Masquerading, and the other for redirecting transparant proxy.
---------------------------------------------------------------------------------
[admin@instaler] ip firewall nat> pr
Flags: X - disabled, I - invalid, D - dynamic
0 chain=srcnat out-interface=public
src-address=172.21.1.0/24 action=masquerade
1 chain=dstnat in-interface=lan src-address=172.21.1.0/24
protocol=tcp dst-port=80 action=redirect to-ports=3128
04. Mangle Setup
And now is the most important part in this case.
---------------------------------------------------------------------------------
If we want to make HIT traffic from web proxy not queued, we have to make a mangle
to handle this traffic. Put this rule on the beginning of the mangle, as it will
check first.
---------------------------------------------------------------------------------
[admin@instaler] > ip firewall mangle print
Flags: X - disabled, I - invalid, D - dynamic
0 ;;; HIT TRAFFIC FROM PROXY
chain=output out-interface=lan
dscp=4 action=mark-packet
new-packet-mark=proxy-hit passthrough=no
---------------------------------------------------------------------------------
As we will make Queue for uplink and downlink traffic, we need 2 packet-mark. In this
example, we use "test-up" for uplink traffic, and "test-down" for downlink traffic.
For uplink traffic, it's quite simple. We need only one rule, using SRC-ADDRESS and
IN-INTERFACE parameters, and using PREROUTING chain. Rule number #1. But for downlink,
we have to make sevaral rules. As we use masquerading, we need Connection Mark,
named as "test-conn". Rule no #2. Then we have to make 2 more rules. First rule is
for non-HTTP connection / direct connection. We use chain forward, as the data traveling
through the router. Rule no #3.
The second rule is for data coming from web-proxy to the client (MISS traffic).
We use OUTPUT chain, as the data coming from internal process in the router itself.
Rule no #4.
For both rules (no #3 and #4) we named it "test-down".
Please be aware, we use passthrough only for connection mark (rule no #2).
---------------------------------------------------------------------------------
[admin@instaler] > ip firewall mangle print
Flags: X - disabled, I - invalid, D - dynamic
1 ;;; UP TRAFFIC
chain=prerouting in-interface=lan
src-address=172.21.1.0/24 action=mark-packet
new-packet-mark=test-up passthrough=no
2 ;;; CONN-MARK
chain=forward src-address=172.21.1.0/24
action=mark-connection
new-connection-mark=test-conn passthrough=yes
3 ;;; DOWN-DIRECT CONNECTION
chain=forward in-interface=public
connection-mark=test-conn action=mark-packet
new-packet-mark=test-down passthrough=no
4 ;;; DOWN-VIA PROXY
chain=output out-interface=lan
dst-address=172.21.1.0/24 action=mark-packet
new-packet-mark=test-down passthrough=no
---------------------------------------------------------------------------------
05. Queue Tree Setup
And now, the queue tree setting. We need one rule for downlink and one rule for
uplink. Be careful when choosing the parent. for downlink traffic, we use parent
"lan", the interface name for local network. And for uplink, we are using parent
"global-in".
---------------------------------------------------------------------------------
[admin@instaler] > queue tree pr
Flags: X - disabled, I - invalid
0 name="downstream" parent=lan packet-mark=test-down
limit-at=32000 queue=default priority=8
max-limit=32000 burst-limit=0
burst-threshold=0 burst-time=0s
1 name="upstream" parent=global-in
packet-mark=test-up limit-at=32000
queue=default priority=8
max-limit=32000 burst-limit=0
burst-threshold=0 burst-time=0s
---------------------------------------------------------------------------------
You can use those mangle also with PCQ.
Edited by primadonal
www.primadonal.com
primadonal[at]yahoo.com
Two gateways failover with load balancingwo gateways failover with load balancing
Tuesday, November 27, 2007wo gateways failover with load balancing
First of all, you need a working system based on these examples: Improved Load Balancing over Multiple Gateways with Persistent Sessions or Improved Load Balancing over Multiple Gateways.
[edit] Route
According to the examples above, you have:
/ ip route
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=odd
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=even
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10
Now you have to change these lines to:
/ ip route
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=odd check-gateway=ping
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=even check-gateway=ping
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 distance=2
If ping fails to 10.111.0.1, then all traffic marked odd go's to the gateway 10.112.0.1, the oposite is also true.
All local traffic go's to the 10.112.0.1 as it's distance is smaller, if 10.112.0.1 fails, then 10.111.0.1 takes over.
The router pings gateway every 10 seconds and if to consecutive pings to the gateway fail, the route is considered dead. So, then testing keep in mind, that gateway failure is detected in 20 to 30 seconds.
[edit] NAT
/ ip firewall nat
add chain=srcnat connection-mark=odd action=src-nat to-addresses=10.111.0.2 \
to-ports=0-65535 comment="" disabled=no
add chain=srcnat connection-mark=even action=src-nat to-addresses=10.112.0.2 \
to-ports=0-65535 comment="" disabled=no
change to:
/ip firewall nat
add chain=srcnat src-address=192.168.0.0/24 action=masquerade
Two gateways failover
This example explains how to use multiple gateways with one taking over when first fails. It begins with adding the gateways. Set bigger distance value for the secondary one, and check-gateway for the first one:
/ip route add gateway=192.168.1.1 check-gateway=ping
/ip route add gateway=192.168.2.1 distance=2
That's all, there are no more steps!
The first gateway will begin as it's distance is smaller (default 0); the check-gateway will make sure it's up; when the ping will fail, it will disable the first gateway and the second will take over; when first one comes up, it will return to it's function.
Multi node management
This article, a work in progress, describes how to remotely monitor and manage one or more groups of bridged routers from a central location. The configuration instructions for RouterOS are based on WinBox, and are not intended for copy/paste. Use them as guidelines.
Contents
[hide]
* 1 Network Topology
* 2 Basic Solution - single remote subnet
o 2.1 On the Gateway Router:
o 2.2 On the Windows PC where WinBox or the Dude is run:
* 3 Solution with Hotspot on Gateway Router
* 4 Solution with Firewall/Router between Modem and Gateway Router
* 5 Solution with multiple remote subnets
[edit] Network Topology
At the network monitoring location, you want to use the Dude or WinBox to monitor and manage all of the remote routers.
Each remote bridged network looks like this:
* A cable modem or DSL modem, referred to in this article as The Modem, at a remote location
* A router, referred to in this article as the Gateway Router, connected to the Modem using a public IP address
* A bunch of routers wirelessly connected to the Gateway Router via WDS
* All of the routers having addresses on the same private subnet
* The Gateway Router is using NAT to masquerade the private subnet
You might also have these complications:
* The Gateway Router might be running a Hotspot
* There might be a non-MikroTik firewall or router between the Modem and Gateway Router
* There might be several remote subnets
[edit] Basic Solution - single remote subnet
The following 2 procedures will setup a PPTP server on the gateway router and a PPTP client on the network management PC.
When you activate the connection to the gateway router from your PC, the Dude or WinBox will appear to be on the private side of the gateway router, on the bridged subnet, and WinBox and/or the Dude will be able to connect directly to any router or all of them at once. Port forwarding is not needed.
[edit] On the Gateway Router:
ppp->pptp server->enabled (check all authentication boxes)
ppp->secrets->add
name =
password =
service = pptp
local address =
remote address =
[edit] On the Windows PC where WinBox or the Dude is run:
The following prodedure is for Windows XP SP2.
Start->Control Panel->Network Connections->Create a new connection
Connect to the network at my workplace Next>
Virtual Private Network Connection Next>
Select a name to call this VPN Next>
Do not dial the initial connection Next>
Enter the IP address of the PUBLIC side of the Gateway Router
[edit] Solution with Hotspot on Gateway Router
Since the other routers are behind the hotspot, they will not be able to communicate with the VPN tunnel in the Gateway Router, even though they are all on the same subnet. To permit access through the hotspot to each of the other routers, create an IP Binding entry as shown below for each router that is behind the hotspot. The IP addresses assigned to the routers can be outside the hotspot address pool if you prefer.
For each router, whose private ip address is of the form 192.168.x.y:
ip->hotspot->IP Bindings->Add
Address: 192.168.x.y
To Address: 192.168.x.y
Type: bypassed
[edit] Solution with Firewall/Router between Modem and Gateway Router
Assume the gateway router has IP address 192.168.a.b as viewed by the firewall/router. On the firewall/router between the Modem and the Gateway Router, do the following:
Forward port 1723 (PPTP) to IP address 192.168.a.b
Forward protocol 47 (GRE) to IP address 192.168.a.b
Note that some routers cannot forward protocols, only ports. In this case, you will NOT be able to create a VPN tunnel to the gateway router. Also, some routers can forward protocol 47, but the mechanism to do so is undocumented. There are also routers that will forward protocol 47 automatically when you forward port 1723. Consult the documentation for your router, and if you don't find any mention of PPTP or port 1723, try finding a user forum where this subject is discussed.
[edit] Solution with multiple remote subnets
Create a separate VPN tunnel to each bridged network
SNMP MRTG
1. Introduction
In this text is described how to configure Mikrotik RouterOS and mrtg (FreeBSD). You must be root on nix mashine and ports collection is installed. Web server must be configured and running on BSD mashine. In this example Web server is Apache server. All information about mrtg and apache can be found at homepages: http://www.mrtg.org http://www.apache.org
[edit] 2. RouterOS SNMP Configuration
/ snmp
set enabled=yes contact="your@mail.com" location="SomeCountry"
/ snmp community
set public name="public" address=192.168.0.5/32 read-access=yes
Ip address 192.168.0.5 is address of BSD mashine where mrtg will be installed.
[edit] 2. MRTG Installation and Configuration
Now we install and configure mrtg on BSD mashine.
cd /usr/ports/net-mgmt/
make
make install
Now we need to create configuration file for mrtg. It can be done automatically by cfgmaker program.192.168.0.1 is ip of RouterOS.
cfgmaker public@192.168.0.1 --output=/usr/local/etc/mrtg.cfg
Change WorkDir value in created mrtg file with text editor. WorkDir value specifies where html files will be created.
It must be same as DocumentRoot value in apache configuration.
For example:
### Global Config Options
# for UNIX
WorkDir: /usr/local/www/data/
### Global Defaults
# to get bits instead of bytes and graphs growing to the right
Options[_]: growright, bits
EnableIPv6: no
######################################################################
# System: Mikrotik
# Description: router
# Contact: your@mail.com
# Location: SomeCountry
######################################################################
Execute mrtg with your config to create html files.
mrtg /usr/local/etc/mrtg.cfg
Now in directory /usr/local/www/data are html files for every interface in MT.
Add this string to crontab to update graphs automatically every 5 minutes
*/5 * * * * root mrtg /usr/local/etc/mrtg.cfg
Now we can create 1 html file with graphs for all interfaces
indexmaker /usr/local/etc/mrtg.cfg --output=/usr/local/www/data/index.html
Here is a sample configuration to monitor the power on a RB333 router using MRTG and SNMP
plotting the results with the correct scale and values:
This should be entered into an existing mrtg.conf file replacing IP_Address with your IP address and MT with your community string
### Input Voltage
Target[IP_Address-voltage]:.1.3.6.1.4.1.14988.1.1.3.8.0&.1.3.6.1.4.1.14988.1.1.3.8.0:MT@IP_Address
AbsMax[IP_Address-voltage]: 200
MaxBytes[IP_Address-voltage]: 200
Title[IP_Address-voltage]: Input Voltage for a monitored -333
PageTop[IP_Address-voltage]:
Input Voltage RB333 being monitored
| System: | RB333 being monitored |
| Maintainer: | managee |
| Description: | Voltage for Monitored 333 |
Options[IP_Address-voltage]: gauge,growright,nopercent, noo, expscale
YLegend[IP_Address-voltage]: Volts
YTicsFactor[IP_Address-voltage]: 0.1
Factor[IP_Address-voltage]: 0.1
ShortLegend[IP_Address-voltage]: V
LegendI[IP_Address-voltage]: Input Voltage
[[Category: Monitoring]]
SNMP PHP
This small example is a PHP script, that uses SNMP to read signal strength values from wireless registration table and publish on web page. This example can be quickly transformed to read other values available for SNMP. To use scripts you need Mikrotik RouterOS, tested for version 2.9.xx (not yet for 3.0), PHP version 4 or 5, Web server (Apache, IIS). Configure Apache, and PHP only thing that needs attention is enabled snmp extension for PHP. In Windows in php.ini section Windows Extensions uncomment line
extension=php_snmp.dll .
Enable snmp on Mikrotik, and if needed, unblock UDP port 161. Copy scripts to WEB folder. Open index.php find line
$ip="hostname"; //Change IP to your host names, address
$mask_mac=false; //Use to mask MAC adress (true / false );
Replace hostname with IP address of Mikrotik, if you don’t want to see complete MAC address change false to true and now open the page in browser. You now see MAC address and signal strength. Page is auto refreshed every 10 seconds and reads values from SNMP.
The PHP code, to be saved as a .php file:
| MAC | Signal strenght(dBm) |
|---|---|
| Please check SNMP settings and IP address | |
NTH in RouterOS 3.x
In v3.0 it is a little different implementation of NTH. It has only two parameters 'every' and 'packet'.
How it works in v3.0
Every rule has its own counter. When rule receives packet counter for current rule is increased by one. If counter matches value of 'every' packet will be matched and counter will be set to zero.
If passthrough is not set then packets will be marked as follows:
- first rule nth=2,1 rule will match every first packet of 2, hence, 50% of all the traffic that is matched by the rules
- second rule if passthrough=no will match ONLY 25% of traffic because in 3.0 you need only one rule to catch traffic not like 2.9
Example
how it is possible to match 50% of all traffic only with one rule:
/ip firewall mangle
add action=mark-packet chain=prerouting new-packet-mark=AAA nth=2,1;
If more than one rule is needed, then there are two ways to match packets:
- first rule sees all packets and matches 1/3 of all, second rule sees 2/3 of packets and matches 1/2, third rule sees and matches all packets that passed through first two rules ( 1/3 of all packets ).
/ip firewall mangle
add action=mark-packet chain=prerouting new-packet-mark=AAA nth=3,1 passthrough=no;
add action=mark-packet chain=prerouting new-packet-mark=BBB nth=2,1 passthrough=no;
add action=mark-packet chain=prerouting new-packet-mark=CCC ;
- all rules can see all packets and each rule matches every 3-rd packet.
/ip firewall mangle
add action=mark-packet chain=prerouting new-packet-mark=AAA nth=3,1 passthrough=yes;
add action=mark-packet chain=prerouting new-packet-mark=BBB nth=3,2 passthrough=yes;
add action=mark-packet chain=prerouting new-packet-mark=CCC nth=3,3 passthrough=yes;
L7 security
layer7-protocol is a method of looking for patterns in connections.
First, add Regexp strings to the protocols menu, to define strings you will be looking for.
/ip firewall layer7-protocol add=
Then, use the defined protocols in firewall:
/ip firewall filter add layer7-protocol=
RouterOS will look for these strings in all connections passing the firewall rule where you use this. As this is resource intensive, make sure to filter out all good traffic before it hits this rule.
You can download a script with a list of common programs here (only for RouterOS v3 RC6). Pattern libraries can be found on the layer7 project page and on the protocol wiki.
Calea Mikrotik
CALEA features included in RouterOS
Multiple subject/multiple destination packet interception and streaming in following formats:
- Call Content Connection (CCC) Interface according to PKT-SP-ES-DCI-I01-060914 (PacketCable 2.0 PacketCable Electronic Surveillance Delivery Function to Collection Function Interface Specification)
- Call Content Connection (CCC) Interface according to ANSI/SCTE 24-13 2006 (IPCalblecom Electronic Surveillance Standard) that is approved method for Communication Content delivery to LEA according to ATIS-1000013.2007 (Lawfully Authorized Electronic Surveillance For Internet Access and Services)
- TZSP format - for reception with 'Ethereal', tcpdump, trafr (sniffer stream reader for linux) - http://www.mikrotik.com/download.html
CALEA-server package
- accepts multiple CCC streams (identified by destination port/source address/case id)
- stores communication content according to "IP Network Access Intercept Requirements and Method"(FBI-WISPA draft) specified "full content" intercept requirements (without out-of-band events)
- stores communication content of multiple subjects/cases
- stores communication content in libpcap format
- new libpcap file based on different conditions (interval/size/packet count)
- generates hash for each pcap file (md5/sha1/sha256)
Calea user
Calea provided options are available only for specific RouterOS user, as Calea server configuration as "tap" configuration. Specific user should have 'sniff' policy enabled at RouterOS user configuration,
/ user group set 0 policy=sniff
sniff policy is enabled by default for "full" and "write" user groups.
Intercepting Packet Flow
The IP Firewall and Interface Bridge now have one additional section,
- firewall section to intercept packets that are going trough firewall
/ ip firewall calea
- bridge section to intercept packets that are going trough bridge
/ interface bridge calea
Firewall and Bridge Calea menus contain same actions and matchers as "ip firewall filter" and "interface bridge filter", new avalailble actions:
- sniff - generates a tzsp stream that can be directed to any Wireshark (Ethereal) server
- sniff-pc - generates a Packet Cable stream that can be directed to a MikroTik RouterOS system with the calea package installed
By selecting either action, the following options will be available:
- sniff-id (Packet Cable protocol only) - packet stream case ID, that can be used to differentiate between separate traffic sets (e.g., between different users; or between client traffic and server traffic)
- sniff-target - IP address of the data retention server
- sniff-target-port - UDP port that the data retention server is listening on
Data Retention Server
The calea package provides an additional tool menu - /tool calea, that allows to save certain incoming data streams to a file. The server will create separate files for each packet stream (one data file and one hash file, if configured). The files will not grow indefinitely, but rather util a certain limit, after which a new set of files will be created for that stream. The limit is specified in size and extent of time, whichever is reached first.
Add a rule with the following properties:
- case-id - case ID set by the intercepting router
- case-name - case name is set on server to specify the folder, where intercepted data is stored
- intercept-ip - IP address of the intercepting router (IP address to receive the stream from)
- intercept-port - UDP port to listen on (port to receive the stream on)
- action - storage format (only pcap for now)
- pcap-file-stop-interval - maximal interval between creating new fileset, if size limit is not reached earlier
- pcap-file-stop-size - maximal filesize, in KiB
- pcap-file-stop-count - maximal packet count
- pcap-file-hash-method - hashing algorithm (md5, sha1 or sha256) for the data file (saved once the data file is completed and closed); no file is created if set to none
Calea Server/Client Configuration Example
let's assume the particular network configuration, we need to intercept data from 192.168.0.10 Wireless Client and send it to the Calea Server located on Local Network: 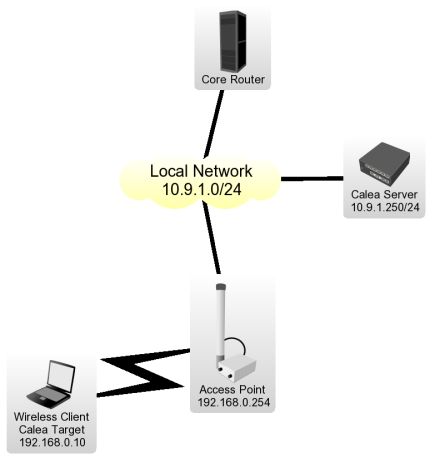
[edit] Client Configuration for the Intercept
Wireless Client is connected to Access Point, data interception has to be performed on Access Point for the particular network design.
- We have requirement to capture all data from the user Wireless Client with IP address of 192.168.0.10 We have to add two rules to make the interception,
/ ip firewall calea add action=sniff-pc chain=forward sniff-id=100 sniff-target=10.9.1.250 sniff-target-port=5555 src-address=192.168.0.10
/ ip firewall calea add action=sniff-pc chain=forward sniff-id=100 sniff-target=10.9.1.250 sniff-target-port=5555 dst-address=192.168.0.10
All traffic going trough the router for specified src/dst addresses is intercepted and sent to Calea Server (sniff-target) with sniff-id=100
- Calea package is not required for intercepting host.
Calea Server Configuration
- Calea package is required for server.
- One rule is required to accept the data from the Access Point to receive all intercepted traffic from the Access Point,
/ tool calea add action=pcap intercept-port=5555 case-id=100 intercept-ip=192.168.0.254
Intercept-port and case-id should be equal on server and client side, intercept-ip is IP address of the intercepting router (Access Point).
- Calea server received information is available under 'file' menu.
Bruteforce login prevention
These are 2 basic scripts I use frequently that are from the forum (written by other users)
Allows only 10 FTP login incorrect answers per minute
in /ip firewall filter
add chain=input protocol=tcp dst-port=21 src-address-list=ftp_blacklist action=drop
add chain=output action=accept protocol=tcp content="530 Login incorrect" dst-limit=1/1m,9,dst-address/1m
add chain=output action=add-dst-to-address-list protocol=tcp content="530 Login incorrect" \
address-list=ftp_blacklist address-list-timeout=3h
This will prevent a SSH brute forcer to be banned for 10 days after repetitive attempts. Change the timeouts as necessary.
in /ip firewall filter
add chain=input protocol=tcp dst-port=22 src-address-list=ssh_blacklist action=drop \
comment="drop ssh brute forcers" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage3 action=add-src-to-address-list address-list=ssh_blacklist \
address-list-timeout=10d comment="" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage2 action=add-src-to-address-list address-list=ssh_stage3 \
address-list-timeout=1m comment="" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage1 \
action=add-src-to-address-list address-list=ssh_stage2 address-list-timeout=1m comment="" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new action=add-src-to-address-list \
address-list=ssh_stage1 address-list-timeout=1m comment="" disabled=no
How to Block Websites
This example will explain you “How to Block Web Sites” & “How to Stop Downloading”. I have use Web-Proxy test Package.
First, Configure Proxy.
/ip proxy
enabled: yes
src-address: 0.0.0.0
port: 8080
parent-proxy: 0.0.0.0:0
cache-drive: system
cache-administrator: "ASHISH PATEL"
max-disk-cache-size: none
max-ram-cache-size: none
cache-only-on-disk: no
maximal-client-connections: 1000
maximal-server-connections: 1000
max-object-size: 512KiB
max-fresh-time: 3d
Now, Make it Transparent
/ip firewall nat
chain=dstnat protocol=tcp dst-port=80 action=redirect to-ports=8080
Make sure that your proxy is NOT a Open Proxy
/ip firewall filter
chain=input in-interface=src-address=0.0.0.0/0 protocol=tcp dst-port=8080 action=drop
Now for Blocking Websites
/ip proxy access
dst-host=www.vansol27.com action=deny
It will block website http://www.vansol27.com/, We can always block the same for different networks by giving src-address. It will block for particular source address.
We can also stop downloading files like.mp3, .exe, .dat, .avi,…etc.
/ip proxy access
path=*.exe action=deny
path=*.mp3 action=deny
path=*.zip action=deny
path=*.rar action=deny.
Try with this also
/ip proxy access
dst-host=:mail action=deny
This will block all the websites contain word “mail” in url.
Example: It will block www.hotmail.com, mail.yahoo.com, www.rediffmail.com
Forwarding a port to an internal IP
This will go on a 2.9.x mikrotik where you want to forward a port (tcp 5900) to an internal IP. 69.69.69.69 is the example wan IP, 192.168.1.101 is the desired internal destination.
/ip firewall nat add chain=dstnat dst-address=69.69.69.69 protocol=tcp dst-port=5900 \
action=dst-nat to-addresses=192.168.1.101 to-ports=5900
Nth On Mikrotik
example: nth=Every,Counter,Packet nth=2,3,0. 2,3,1 2,3,2
divide all packets into groups of three (2+1). The packets will be numbered from 0 to 2. So, a sequence of packets the rule matches looks like: (0 1 2)(0 1 2)(0 1 2)(0 1 2)(0 1 2)...
the first rule will match the first packet in each group ("Packet"=0). The second rule will match the second packet in each group ("Packet"=1) and so on. Each successful match increments the counter. When a value of "Every" is reached, the counter is reset to 0. For this to work, the "Counter" should be the same for all rules (you can pick any value from 0 to 15, IIRC).
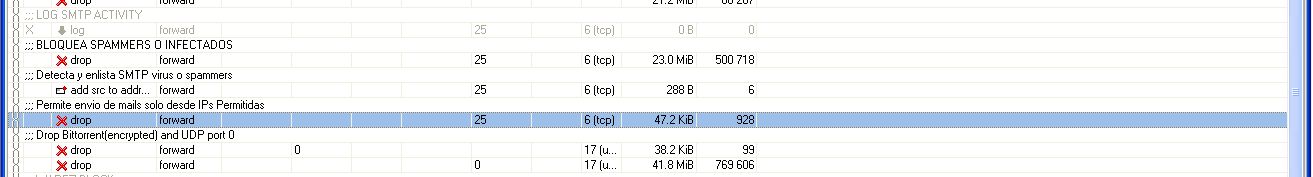
How to autodetect infected or spammer users and temporary block the SMTP output
Here can see in the solution which i invented and work excellent to autodetect and block SMTP viruses or spammers!
Only create these 2 rules in firewall forward:
/ip firewall filter
add chain=forward protocol=tcp dst-port=25 src-address-list=spammer
action=drop comment="BLOCK SPAMMERS OR INFECTED USERS"
add chain=forward protocol=tcp dst-port=25 connection-limit=30,32 limit=50,5 action=add-src-to-address-list
address-list=spammer address-list-timeout=1d comment="Detect and add-list SMTP virus or spammers"
When an infected user is autodetected with a virus worm or doing spam, the user is added to a spammer list and block the STMP outgoing by 1 day, all the values can be adjusted for different networks types or at your convenience
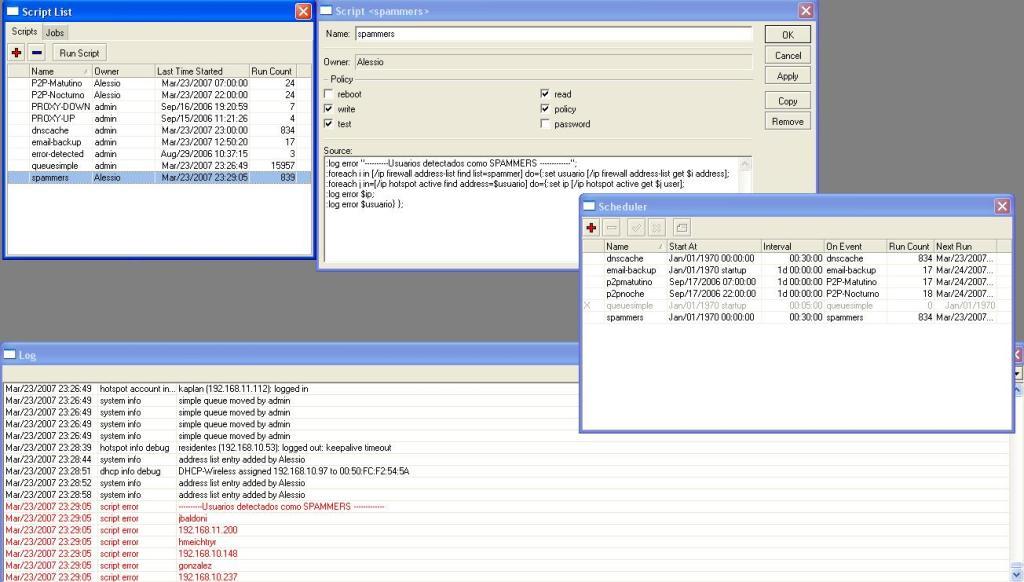
[edit] Logging detected users
Next, to display a red Log each 30 minutes listing the detected infected or spammers users using hotspot, add the next script:
/system script
add name="spammers" source=":log error \"----------Users detected like \
SPAMMERS -------------\";
\n:foreach i in \[/ip firewall address-list find \
list=spammer\] do={:set usser \[/ip firewall address-list get \$i \
address\];
\n:foreach j in=\[/ip hotspot active find address=\$usser\] \
do={:set ip \[/ip hotspot active get \$j user\];
\n:log error \$ip;
\n:log \
error \$usser} };" policy=ftp,read,write,policy,test,winbox
Dmitry on firewalling
Components of the filter
- protocol classifier
- invalid packet filter
- port-scan detector
- policy classifier
- application protocol filter
- TCP-specific filters
- application protocol specific filters
Introduction
There are two interfaces on our router: Local (for connecting internal network) and Public (connected to the Internet)
Protocol classifier
/ ip firewall mangle
add chain=prerouting protocol=tcp connection-state=new action=jump jump-target=tcp-services
add chain=prerouting protocol=udp connection-state=new action=jump jump-target=udp-services
add chain=prerouting connection-state=new action=jump jump-target=other-services
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=20-21 action=mark-connection new-connection-mark=ftp passthrough=no
add chain=tcp-services protocol=tcp src-port=513-65535 dst-port=22 action=mark-connection new-connection-mark=ssh passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=23 action=mark-connection new-connection-mark=telnet passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=25 action=mark-connection new-connection-mark=smtp passthrough=no
add chain=tcp-services protocol=tcp src-port=53 dst-port=53 action=mark-connection new-connection-mark=dns passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=53 action=mark-connection new-connection-mark=dns passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=80 action=mark-connection new-connection-mark=http passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=110 action=mark-connection new-connection-mark=pop3 passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=113 action=mark-connection new-connection-mark=auth passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=119 action=mark-connection new-connection-mark=nntp passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=143 action=mark-connection new-connection-mark=imap passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=161-162 action=mark-connection new-connection-mark=snmp passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=443 action=mark-connection new-connection-mark=https passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=465 action=mark-connection new-connection-mark=smtps passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=993 action=mark-connection new-connection-mark=imaps passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=995 action=mark-connection new-connection-mark=pop3s passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=1723 action=mark-connection new-connection-mark=pptp passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=2379 action=mark-connection new-connection-mark=kgs passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=3128 action=mark-connection new-connection-mark=proxy passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=3389 action=mark-connection new-connection-mark=win-ts passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=4242-4243 action=mark-connection new-connection-mark=emule passthrough=no
add chain=tcp-services protocol=tcp src-port=4661-4662 dst-port=1024-65535 action=mark-connection new-connection-mark=overnet passthrough=no
add chain=tcp-services protocol=tcp src-port=4711 dst-port=1024-65535 action=mark-connection new-connection-mark=emule passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=5900-5901 action=mark-connection new-connection-mark=vnc passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=6667-6669 action=mark-connection new-connection-mark=irc passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=6881-6889 action=mark-connection new-connection-mark=bittorrent passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=8080 action=mark-connection new-connection-mark=http passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=8291 action=mark-connection new-connection-mark=winbox passthrough=no
add chain=tcp-services protocol=tcp action=mark-connection new-connection-mark=other-tcp passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=53 action=mark-connection new-connection-mark=dns passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=123 action=mark-connection new-connection-mark=ntp passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=1701 action=mark-connection new-connection-mark=l2tp passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=4665 action=mark-connection new-connection-mark=emule passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=4672 action=mark-connection new-connection-mark=emule passthrough=no
add chain=udp-services protocol=udp src-port=4672 dst-port=1024-65535 action=mark-connection new-connection-mark=emule passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=12053 action=mark-connection new-connection-mark=overnet passthrough=no
add chain=udp-services protocol=udp src-port=12053 dst-port=1024-65535 action=mark-connection new-connection-mark=overnet passthrough=no
add chain=udp-services protocol=udp src-port=36725 dst-port=1024-65535 action=mark-connection new-connection-mark=skype passthrough=no
add chain=udp-services protocol=udp connection-state=new action=mark-connection new-connection-mark=other-udp passthrough=no
add chain=other-services protocol=icmp icmp-options=8:0-255 action=mark-connection new-connection-mark=ping passthrough=no
add chain=other-services protocol=gre action=mark-connection new-connection-mark=gre passthrough=no
add chain=other-services action=mark-connection new-connection-mark=other passthrough=no
Note that for TCP and UDP, we check both, source port (usually, 1024-65535) and destination port. Everything else is not a valid protocol.
Sanity-check
Most generic invalid packet and port-scan detection techniques
Place this before all other rules in mangle:
/ip firewall mangle
add chain=prerouting in-interface=Public dst-address-list=nat-addr action=mark-packet new-packet-mark=nat-traversal passthrough=no
Note that just like in the line above, some filter rules rely on address lists. here is a simple list, which you should extend further:
/ ip firewall address-list
add list=illegal-addr address=0.0.0.0/8 comment="illegal addresses"
add list=illegal-addr address=127.0.0.0/8
add list=illegal-addr address=224.0.0.0/3
add list=illegal-addr address=10.0.0.0/8
add list=illegal-addr address=172.16.0.0/12
add list=illegal-addr address=192.168.0.0/16
add list=local-addr address=172.31.255.0/29 comment="my local network"
add list=nat-addr address=172.31.255.0/29 comment="my local network"
So, there are three address lists:
- illegal-addr - the list, which could be extended to some few tens of addresses at least to include the bogon IPs, which are not registered with IANA and some more, this short list given in examples is just a short sample;
- local-addr - the list to include all addresses located in your network, behind this firewall
- nat-addr - should contain all the IP addresses you are source-natting on your router
In this example we exclude traffic between the local clients connected to different ports of the Local interface (which is a bridge between ethernet and wireless networks):
/ ip firewall filter
add chain=forward in-interface=Local out-interface=Local action=accept comment="Allow traffic between wired and wireless networks"
Then we are filtering everything else to the drop chain of the firewall. The separate chain is created to keep all logging and accounting in one place.
/ ip firewall filter
add chain=forward action=jump jump-target=sanity-check comment="Sanity Check"
add chain=sanity-check packet-mark=nat-traversal action=jump jump-target=drop comment="Deny illegal NAT traversal"
add chain=sanity-check protocol=tcp psd=20,3s,3,1 action=add-src-to-address-list address-list=blocked-addr address-list-timeout=1d comment="Block port scans"
add chain=sanity-check protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack action=add-src-to-address-list address-list=blocked-addr address-list-timeout=1d comment="Block TCP Null scan"
add chain=sanity-check protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list=blocked-addr address-list-timeout=1d comment="Block TCP Xmas scan"
add chain=sanity-check protocol=tcp src-address-list=blocked-addr action=jump jump-target=drop
add chain=sanity-check protocol=tcp tcp-flags=rst action=jump jump-target=drop comment="Drop TCP RST"
add chain=sanity-check protocol=tcp tcp-flags=fin,syn action=jump jump-target=drop comment="Drop TCP SYN+FIN"
add chain=sanity-check connection-state=invalid action=jump jump-target=drop comment="Dropping invalid connections at once"
add chain=sanity-check connection-state=established action=accept comment="Accepting already established connections"
add chain=sanity-check connection-state=related action=accept comment="Also accepting related connections"
add chain=sanity-check dst-address-type=broadcast,multicast action=jump jump-target=drop comment="Drop all traffic that goes to multicast or broadcast addresses"
add chain=sanity-check in-interface=Local dst-address-list=illegal-addr dst-address-type=!local action=jump jump-target=drop comment="Drop illegal destination addresses"
add chain=sanity-check in-interface=Local src-address-list=!local-addr action=jump jump-target=drop comment="Drop everything that goes from local interface but not from local address"
add chain=sanity-check in-interface=Public src-address-list=illegal-addr action=jump jump-target=drop comment="Drop illegal source addresses"
add chain=sanity-check in-interface=Public dst-address-list=!local-addr action=jump jump-target=drop comment="Drop everything that goes from public interface but not to local address"
add chain=sanity-check src-address-type=broadcast,multicast action=jump jump-target=drop comment="Drop all traffic that goes from multicast or broadcast addresses"
[edit] Application-specific filters
/ ip firewall filter
add chain=forward protocol=tcp action=jump jump-target=restrict-tcp
add chain=forward protocol=udp action=jump jump-target=restrict-udp
add chain=forward action=jump jump-target=restrict-ip
add chain=restrict-tcp connection-mark=auth action=reject
add chain=restrict-tcp connection-mark=smtp action=jump jump-target=smtp-first-drop comment="anti-spam policy"
add chain=smtp-first-drop src-address-list=first-smtp action=add-src-to-address-list address-list=approved-smtp
add chain=smtp-first-drop src-address-list=approved-smtp action=return
add chain=smtp-first-drop action=add-src-to-address-list address-list=first-smtp
add chain=smtp-first-drop action=reject reject-with=icmp-network-unreachable
Restricting services
/ ip firewall filter
add chain=restrict-tcp connection-mark=other-tcp action=jump jump-target=drop
add chain=restrict-udp connection-mark=other-udp action=jump jump-target=drop
add chain=restrict-ip connection-mark=other action=jump jump-target=drop
Protecting the router
/ ip firewall filter
add chain=input src-address-type=local dst-address-type=local action=accept comment="Allow local traffic \(between router applications\)"
add chain=input in-interface=Local protocol=udp src-port=68 dst-port=67 action=jump jump-target=dhcp comment="DHCP protocol would not pass sanity checking, so enabling it explicitly before other checks"
add chain=input action=jump jump-target=sanity-check comment="Sanity Check"
add chain=input dst-address-type=!local action=jump jump-target=drop comment="Dropping packets not destined to the router itself, including all broadcast traffic"
add chain=input connection-mark=ping limit=5,5 action=accept comment="Allow pings, but at a very limited rate \(5 per sec\)"
add chain=input in-interface=Local action=jump jump-target=local-services comment="Allowing some services to be accessible from the local network"
add chain=input in-interface=Public action=jump jump-target=public-services comment="Allowing some services to be accessible from the Internet"
add chain=input action=jump jump-target=drop
add chain=dhcp src-address=0.0.0.0 dst-address=255.255.255.255 action=accept
add chain=dhcp src-address=0.0.0.0 dst-address-type=local action=accept
add chain=dhcp src-address-list=local-addr dst-address-type=local action=accept
add chain=local-services connection-mark=ssh action=accept comment="SSH \(22/TCP\)"
add chain=local-services connection-mark=dns action=accept comment="DNS"
add chain=local-services connection-mark=proxy action=accept comment="HTTP Proxy \(3128/TCP\)"
add chain=local-services connection-mark=winbox comment="Winbox \(8291/TCP\)" disabled=no
add chain=local-services action=drop comment="Drop Other Local Services"
add chain=public-services connection-mark=ssh action=accept comment="SSH \(22/TCP\)"
add chain=public-services connection-mark=pptp action=accept comment="PPTP \(1723/TCP\)"
add chain=public-services connection-mark=gre action=accept comment="GRE for PPTP"
add chain=public-services action=drop comment="Drop Other Public Services"
- The "accept ping" rule needs to come before the "public" and "local" jump rules otherwise that rules will never be executed and ICMP will continue to be dropped.
Proxying everything
/ ip firewall nat
add chain=dstnat in-interface=Local connection-mark=dns action=redirect comment="proxy for DNS requests"
add chain=dstnat in-interface=Local connection-mark=http protocol=tcp action=redirect to-ports=3128 comment="proxy for HTTP requests"
add chain=dstnat in-interface=Local connection-mark=ntp action=redirect comment="proxy for NTP requests"
Enable Proxy servers
/ system ntp server
set enabled=yes broadcast=no multicast=no manycast=no
/ system ntp client
set enabled=yes mode=unicast primary-ntp=xxx.xxx.xxx.xxx secondary-ntp=0.0.0.0
/ ip proxy
set enabled=yes port=3128 parent-proxy=0.0.0.0:1 maximal-client-connections=1000 maximal-server-connections=1000
/ ip dns
set primary-dns=yyy.yyy.yyy.yyy secondary-dns=0.0.0.0 allow-remote-requests=yes cache-size=2048KiB cache-max-ttl=1w
Please change:
- xxx.xxx.xxx.xxx to the NTP server you choose
- yyy.yyy.yyy.yyy to your ISP's DNS server ip
Redirect mail traffic to a specified server
This is if you want to redirect all traffic through your router to your own specified mail server. This is usefull if you have many clients from different locations connecting to your network at different times. (Note that if you are using Hotspot you can do this in the Hotspot settings instead)
ip firewall nat add chain=dstnat protocol=tcp dst-port=25 action=dst-nat to-addresses=10.0.0.1 to-ports=25
This will redirect all smtp (port 25) traffic out the router to ip address 10.0.0.1
How to Block Customer
How to Block a Customer and Tell him to Pay the Bill
Sometimes you may need to cut off a customer and tell him to pay his bill. It's best done by redirecting his http requests to a page with information telling to pay in order to get reconnected. You can do it with a simple destination NAT rule that captures all http requests from a specific address and sends them to a server with webpage telling to pay the bill. However, it's quite easy to make this using the HotSpot feature of RouterOS. Please note that this don't work with PPPoE connections.
To make this setup, you should have Hotspot package enabled on the RouterOS. This example will cover how to block customer's computer. When he tries to open a webpage he would be redirected to the hotspot page which will contain info that he hasn't paid the bill for the Internet access. Your router should have already been configured and working (customer should have access to the Internet), you should have the DNS server specified in the router.
First you should edit the Hotspot login.html page with the text that contains information that will be shown to the customers who haven't paid their bills. It could be something like this: "Service not available, please pay the bill and contact us by phone to get reconnected
Next, add an ip-binding rule that will allow all customers to bypass the hotspot page. It is done using such a command:
/ip hotspot ip-binding add type=bypassed address=0.0.0.0/0 \
comment="bypass the hotspot for all the paying customers"
After that add the Hotspot server on the interface where your clients are connected. It can be done using such command:
/ip hotspot add interface=local disabled=no
Now you can add ip-binding rules for the customers that haven't paid their bill. You can match them by IP address or MAC address. Here is an example using MAC address:
/ip hotspot ip-binding add mac-address=00:0C:42:00:00:90 type=regular comment "Non paying client 1"
Now we have such configuration:
[admin@MikroTik] ip hotspot ip-binding> print
Flags: X - disabled, P - bypassed, B - blocked
# MAC-ADDRESS ADDRESS TO-ADDRESS SERVER
0 P ;;; bypass the hotspot for all the paying customers
0.0.0.0/0
1 ;;; Non paying client 1
00:0C:42:00:00:90
There is one more step to make it work, you should change the order of these rules, the first rule should be above the bypass rule so it could be processed. You can move it using move command:
[admin@MikroTik] ip hotspot ip-binding> move 1 0
Now the ip-binding configuration should look like this:
[admin@MikroTik] ip hotspot ip-binding> print
Flags: X - disabled, P - bypassed, B - blocked
# MAC-ADDRESS ADDRESS TO-ADDRESS SERVER
0 ;;; Non paying client 1
00:0C:42:00:00:90
1 P ;;; bypass the hotspot for all the paying customers
0.0.0.0/0
If the customers can pay their bill using internet you can modify the login.html by adding some links to clients bank web-page where they can pay their bill. After you add these links in the login page you should also add them in the hotspot configuration so the blocked customer could access that page. This can be done in the 'ip hotspot walled-garden ip' menu. Here is an example:
/ip hotspot walled-garden ip add dst-host=www.paypal.com
How to secure a network using ARP
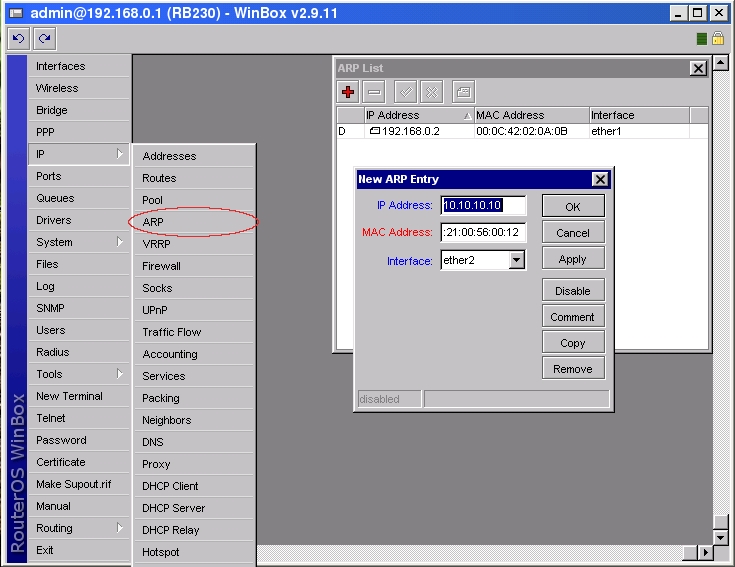
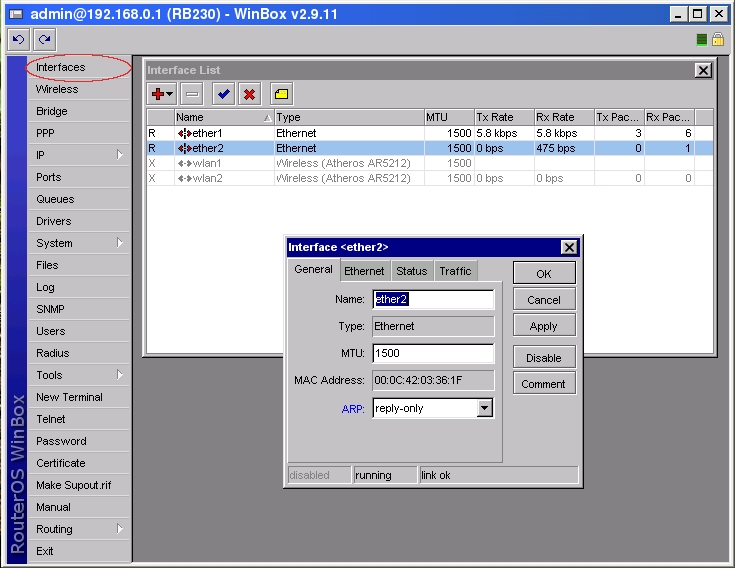
Although hosts in IP network are addressed using IP addresses, hardware addresses must be used to actually transport data from one host to another at Layer-2 (EG: Ethernet). Address Resolution Protocol (ARP) provides a mapping between the two different forms of addresses. A router has an ARP table that contains ARP entries. ARP entries consist of IP addresses and corresponding hardware addresses (such as a MAC address). Normally ARP provides a dynamic mapping from an IP address to corresponding hardware address by adding ARP entries automatically as they are discovered, but to increase network security static ARP entries can be created manually. By allowing a router to reply only to those static ARP entries found in the ARP table we restrict access to the router and to the network behind the router to only those IP/Hardware address combinations found in the ARP table. To make a router use only static ARP entries follow the steps listed below:
1. Add ARP entries of hosts you want to accept in WinBox
or in Console
[admin@RB230] ip arp> add address=10.10.10.10 interface=ether2 mac-address=06 \
\... 00:21:00:56:00:12
2. Make ether2 interface only reply to ARP requests using your specified ARP entries in WinBox
or in Console
[admin@RB230] > interface ethernet set ether2 arp=reply-only
Drop port scanners
To protect the Router from port scanners, we can record the IPs of hackers who try to scan your box. Using this address list we can drop connection from those IP
in /ip firewall filter
add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="Port scanners to list " disabled=no
Various combinations of TCP flags can also indicate port scanner activity.
add chain=input protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="NMAP FIN Stealth scan"
add chain=input protocol=tcp tcp-flags=fin,syn
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="SYN/FIN scan"
add chain=input protocol=tcp tcp-flags=syn,rst
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="SYN/RST scan"
add chain=input protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="FIN/PSH/URG scan"
add chain=input protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="ALL/ALL scan"
add chain=input protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="NMAP NULL scan"
Then you can drop those IPs:
add chain=input src-address-list="port scanners" action=drop comment="dropping port scanners" disabled=no
Similarly, you can drop these port scanners in the forward chain, but using the above rules with "chain=forward".
Protecting your customers
To protect the customer's network, we should check all traffic which goes through router and block unwanted. For icmp, tcp, udp traffic we will create chains, where all unwanted packets will be dropped. For the beginning, we can copy and paste the following commands into RouterOS terminal console:
/ip firewall filter
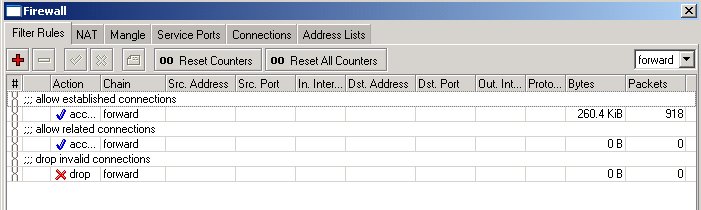
add chain=forward connection-state=established comment="allow established connections"
add chain=forward connection-state=related comment="allow related connections"
add chain=forward connection-state=invalid action=drop comment="drop invalid connections"
Here, the first two rules deal with packets of already opened or related connections. We assume that those are okay. We do not like invalid connection packets, therefore they are dropped.
Next, we should filter out and drop all unwanted packets that look like coming from virus infected hosts. Instead of adding those rules to the forward chain, we create a new chain for all unwanted netbios and similar traffic. We can give the chain a descriptive name, say, "virus" when adding the following rules to the ip firewall filter (you can copy and paste these rules into the terminal window, if you are in the /ip firewall filter menu):
add chain=virus protocol=tcp dst-port=135-139 action=drop comment="Drop Blaster Worm"
add chain=virus protocol=udp dst-port=135-139 action=drop comment="Drop Messenger Worm"
add chain=virus protocol=tcp dst-port=445 action=drop comment="Drop Blaster Worm"
add chain=virus protocol=udp dst-port=445 action=drop comment="Drop Blaster Worm"
add chain=virus protocol=tcp dst-port=593 action=drop comment="________"
add chain=virus protocol=tcp dst-port=1024-1030 action=drop comment="________"
add chain=virus protocol=tcp dst-port=1080 action=drop comment="Drop MyDoom"
add chain=virus protocol=tcp dst-port=1214 action=drop comment="________"
add chain=virus protocol=tcp dst-port=1363 action=drop comment="ndm requester"
add chain=virus protocol=tcp dst-port=1364 action=drop comment="ndm server"
add chain=virus protocol=tcp dst-port=1368 action=drop comment="screen cast"
add chain=virus protocol=tcp dst-port=1373 action=drop comment="hromgrafx"
add chain=virus protocol=tcp dst-port=1377 action=drop comment="cichlid"
add chain=virus protocol=tcp dst-port=1433-1434 action=drop comment="Worm"
add chain=virus protocol=tcp dst-port=2745 action=drop comment="Bagle Virus"
add chain=virus protocol=tcp dst-port=2283 action=drop comment="Drop Dumaru.Y"
add chain=virus protocol=tcp dst-port=2535 action=drop comment="Drop Beagle"
add chain=virus protocol=tcp dst-port=2745 action=drop comment="Drop Beagle.C-K"
add chain=virus protocol=tcp dst-port=3127-3128 action=drop comment="Drop MyDoom"
add chain=virus protocol=tcp dst-port=3410 action=drop comment="Drop Backdoor OptixPro"
add chain=virus protocol=tcp dst-port=4444 action=drop comment="Worm"
add chain=virus protocol=udp dst-port=4444 action=drop comment="Worm"
add chain=virus protocol=tcp dst-port=5554 action=drop comment="Drop Sasser"
add chain=virus protocol=tcp dst-port=8866 action=drop comment="Drop Beagle.B"
add chain=virus protocol=tcp dst-port=9898 action=drop comment="Drop Dabber.A-B"
add chain=virus protocol=tcp dst-port=10000 action=drop comment="Drop Dumaru.Y"
add chain=virus protocol=tcp dst-port=10080 action=drop comment="Drop MyDoom.B"
add chain=virus protocol=tcp dst-port=12345 action=drop comment="Drop NetBus"
add chain=virus protocol=tcp dst-port=17300 action=drop comment="Drop Kuang2"
add chain=virus protocol=tcp dst-port=27374 action=drop comment="Drop SubSeven"
add chain=virus protocol=tcp dst-port=65506 action=drop comment="Drop PhatBot, Agobot, Gaobot"
Here, we list all those well known "bad" protocols and ports, used by various trojans and viruses when they take over your computer. This list is incomplete; we should add more rules to it! We can jump to this list from the forward chain by using a rule with action=jump:
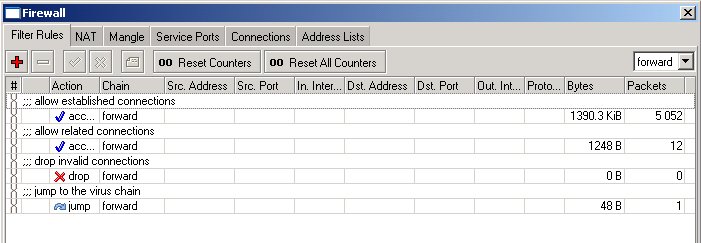
add chain=forward action=jump jump-target=virus comment="jump to the virus chain"
The forward chain looks now as follows:
If the packet does not match any of the rules in the virus chain, the processing is returned back to the forward chain. We can simply add rules allowing udp and ping, and then drop everything else (if there are no services on customer's network that need to be accessed from outside):
add chain=forward protocol=icmp comment="allow ping"
add chain=forward protocol=udp comment="allow udp"
add chain=forward action=drop comment="drop everything else"