Different limits for Local/Overseas traffic for 3 bandwitch rates using pcq and queue tree
Tuesday, November 27, 20071. Introdution
Let's consider the scenario, when you want to apply different limits for many users to Local and Oversea traffic and don`t want load cpu with a lot of simple queues and you want sell for customers 3 bandwitch rates.
1.12/6 Mbps Latvian Traffic 1Mbps/512Kbps Overseas traffic
2.6/3 Mbps Latvian Traffic 512kbps/256Kbps Overseas traffic
3.4/2 Mbps Latvian Traffic 256Kbps/128Kbps Overseas traffic
Queue trees will limit data rate for the Local country traffic and Oversea traffic In this scenario local country is Latvia. List of all Latvian subnets located at http://www.nic.lv/local.net
2. Configuration
/ ip firewall address-list
add list=12/6 address=192.168.0.2 comment="12/6mbps Local traffic 1mbps/512kbps oversea"
add list=6/3 address=192.168.0.3 comment="6/3mbps Local traffic 512kbps/256kbps oversea"
add list=4/2 address=192.168.0.4 comment="4/2mbps Local traffic 256kbps/128kbps oversea"
add list=Latvia address=159.148.0.0/16 comment="" disabled=no
add list=Latvia address=193.41.195.0/24 comment="" disabled=no
add list=Latvia address=193.41.33.0/24 comment="" disabled=no
add list=Latvia address=193.41.45.0/24 comment="" disabled=no
add list=Latvia address=193.68.64.0/19 comment="" disabled=no
add list=Latvia address=193.108.29.0/24 comment="" disabled=no
add list=Latvia address=193.108.144.0/22 comment="" disabled=no
add list=Latvia address=193.108.185.0/24 comment="" disabled=no
/ ip firewall mangle
add chain=forward action=mark-packet new-packet-mark=LV_DL_6M passthrough=yes \
in-interface=public src-address-list=latvia comment="Default mangle for \
Latvia Download" disabled=no
add chain=forward action=mark-packet new-packet-mark=LV_UL_3M passthrough=yes \
in-interface=local dst-address-list=latvia comment="Default mangle for \
Latvia Upload" disabled=no
add chain=forward action=mark-packet new-packet-mark=OS_DL_512k \
passthrough=yes in-interface=public src-address-list=!latvia \
comment="Default mangle for Oversea Download" disabled=no
add chain=forward action=mark-packet new-packet-mark=OS_UL_256k \
passthrough=yes in-interface=local dst-address-list=!latvia \
comment="Default mangle for Oversea Upload" disabled=no
add chain=forward action=mark-packet new-packet-mark=LV_DL_12M passthrough=no \
in-interface=public src-address-list=latvia dst-address-list=12/6 \
comment="Tarif 12/6 Latvia Download" disabled=no
add chain=forward action=mark-packet new-packet-mark=LV_UL_6M passthrough=no \
in-interface=local src-address-list=12/6 dst-address-list=latvia \
comment="Tarif 12/6 Latvia Upload" disabled=no
add chain=forward action=mark-packet new-packet-mark=OS_DL_1M passthrough=no \
in-interface=public src-address-list=!latvia dst-address-list=12/6 \
comment="Tarif 12/6 Oversea Download" disabled=no
add chain=forward action=mark-packet new-packet-mark=OS_UL_512k passthrough=no \
in-interface=local src-address-list=12/6 dst-address-list=!latvia \
comment="Tarif 12/6 Oversea Upload" disabled=no
add chain=forward action=mark-packet new-packet-mark=LV_DL_4M passthrough=no \
in-interface=public src-address-list=latvia dst-address-list=4/2 \
comment="Tarif 4/2 Latvia Download" disabled=no
add chain=forward action=mark-packet new-packet-mark=LV_UL_2M passthrough=no \
in-interface=local src-address-list=4/2 dst-address-list=latvia \
comment="Tarif 4/2 Latvia Upload" disabled=no
add chain=forward action=mark-packet new-packet-mark=OS_DL_256k passthrough=no \
in-interface=public src-address-list=!latvia dst-address-list=4/2 \
comment="Tarif 4/2 Oversea Download" disabled=no
add chain=forward action=mark-packet new-packet-mark=OS_UL_128k passthrough=no \
in-interface=local src-address-list=4/2 dst-address-list=!latvia \
comment="Tarif 4/2 Oversea Upload" disabled=no
/ queue type
add name="LV_DL_12M" kind=pcq pcq-rate=12000000 pcq-limit=50 \
pcq-classifier=dst-address pcq-total-limit=2000
add name="LV_DL_6M" kind=pcq pcq-rate=6000000 pcq-limit=50 \
pcq-classifier=dst-address pcq-total-limit=2000
add name="LV_DL_4M" kind=pcq pcq-rate=4000000 pcq-limit=50 \
pcq-classifier=dst-address pcq-total-limit=2000
add name="LV_UL_6M" kind=pcq pcq-rate=6000000 pcq-limit=50 \
pcq-classifier=src-address pcq-total-limit=2000
add name="LV_UL_3M" kind=pcq pcq-rate=3000000 pcq-limit=50 \
pcq-classifier=src-address pcq-total-limit=2000
add name="LV_UL_2M" kind=pcq pcq-rate=2000000 pcq-limit=50 \
pcq-classifier=src-address pcq-total-limit=2000
add name="OS_DL_1M" kind=pcq pcq-rate=1000000 pcq-limit=50 \
pcq-classifier=dst-address pcq-total-limit=2000
add name="OS_DL_512k" kind=pcq pcq-rate=512000 pcq-limit=50 \
pcq-classifier=dst-address pcq-total-limit=2000
add name="OS_DL_256k" kind=pcq pcq-rate=256000 pcq-limit=50 \
pcq-classifier=dst-address pcq-total-limit=2000
add name="OS_UL_512k" kind=pcq pcq-rate=512000 pcq-limit=50 \
pcq-classifier=src-address pcq-total-limit=2000
add name="OS_UL_256k" kind=pcq pcq-rate=256000 pcq-limit=50 \
pcq-classifier=src-address pcq-total-limit=2000
add name="OS_UL_128k" kind=pcq pcq-rate=128000 pcq-limit=50 \
pcq-classifier=src-address pcq-total-limit=2000
/ queue tree
add name="LV_DL_12M" parent=local packet-mark=LV_DL_12M limit-at=0 queue=LV_DL_12M priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="LV_DL_6M" parent=local packet-mark=LV_DL_6M limit-at=0 queue=LV_DL_6M priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="LV_UL_2M" parent=public packet-mark=LV_UL_2M limit-at=0 queue=LV_UL_2M priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="LV_DL_4M" parent=local packet-mark=LV_DL_4M limit-at=0 queue=LV_DL_4M priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="LV_UL_3M" parent=public packet-mark=LV_UL_3M limit-at=0 queue=LV_UL_3M priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="LV_UL_6M" parent=public packet-mark=LV_UL_6M limit-at=0 queue=LV_UL_6M priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="OS_DL_1M" parent=local packet-mark=OS_DL_1M limit-at=0 queue=OS_DL_1M priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="OS_DL_256k" parent=local packet-mark=OS_DL_256k limit-at=0 queue=OS_DL_256k priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="OS_DL_512k" parent=local packet-mark=OS_DL_512k limit-at=0 queue=OS_DL_512k priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="OS_UL_128k" parent=public packet-mark=OS_UL_128k limit-at=0 queue=OS_UL_128k priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="OS_UL_256k" parent=public packet-mark=OS_UL_256k limit-at=0 queue=OS_UL_256k priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
add name="OS_UL_512k" parent=public packet-mark=OS_UL_512k limit-at=0 queue=OS_UL_512k priority=8 max-limit=0 burst-limit=0 \
burst-threshold=0 burst-time=0s disabled=no
3. Explanation
In /ip firewall address-list we created 3 lists for bandwitch profiles and list with name Latvia with latvian subnets In /ip firewall mangle we created address list based packet marks for bandwitch profiles. All ips witch is not included in any address list will have second bandwitch profiles rates. In /queue types we created pcq types for bandwitch profiles. In /queue tree we created rules with Local/Overseas packet marks and queue types for bandwitch profiles.
Now customer with ip 192।168.0.2 have 1 profile rates, customer with ip 192.168.0.3 have 2 profile rates, client with ip 192.168.0.4 have 3 profile rates and all others have 2 bandwitch rates, so all traffic will be limited and your cpu power will be free for other tasks.
source = http://wiki.mikrotik.com
How to apply different limits for Local/Overseas traffic
Introduction
Let's consider the scenario, when you want to apply different limit to Local and Oversea traffic. Oversea traffic - traffic that doesn't belong to the Local country traffic.
To distinguish oversea traffic from Local country traffic, we will use 'mangle marks' and 'address-list' features. It will place appropriate marks to the packets to/from the Local country and Oversea networks. Local traffic is 'latvian traffic' in the particular example, list of network numbers belonging to ISPs in Latvia can be extracted from file: http://www.nic.lv/local.net
Note, 'address-list' entries should be replaced with respective addresses, if your router isn't located in Latvia. To find the actual list of network numbers belonging to your country, use Google or any other resources.
Simple queues will limit data rate for the Local country traffic and Oversea traffic.
Quick Start for Impatient
Configuration export from the router:
/ ip firewall address-list
add list=Latvia address=159.148.0.0/16 comment="" disabled=no
add list=Latvia address=193.41.195.0/24 comment="" disabled=no
add list=Latvia address=193.41.33.0/24 comment="" disabled=no
add list=Latvia address=193.41.45.0/24 comment="" disabled=no
add list=Latvia address=193.68.64.0/19 comment="" disabled=no
add list=Latvia address=193.108.29.0/24 comment="" disabled=no
add list=Latvia address=193.108.144.0/22 comment="" disabled=no
add list=Latvia address=193.108.185.0/24 comment="" disabled=no
add list=Latvia address=193.109.211.0/24 comment="" disabled=no
add list=Latvia address=193.109.85.0/24 comment="" disabled=no
add list=Latvia address=193.110.8.0/23 comment="" disabled=no
add list=Latvia address=193.110.164.0/23 comment="" disabled=no
...
add list=Latvia address=193.111.244.0/22 comment="" disabled=no
/ ip firewall mangle
add chain=prerouting src-address=192.168.100.0/24 action=mark-connection \
new-connection-mark="Con Entire Traffic" passthrough=yes \
comment="Mark-connection All Traffic" disabled=no
add chain=prerouting src-address=192.168.100.0/24 connection-mark="Con Entire \
Traffic" dst-address-list=!Latvia action=mark-connection \
new-connection-mark="Con Oversea" passthrough=yes comment="Mark-connection \
Oversea Traffic" disabled=no
add chain=prerouting connection-mark="Con Oversea" action=mark-packet \
new-packet-mark="Oversea traffic" passthrough=no comment="Mark-packet \
Oversea Traffic" disabled=no
add chain=prerouting action=mark-packet new-packet-mark="Local Country Traffic" \
passthrough=no comment="Mark-packet Local Country Traffic" disabled=no
/ queue simple
add name="Oversea" target-addresses=192.168.100.254/32 dst-address=0.0.0.0/0 \
interface=all parent=none packet-marks="Oversea traffic" direction=both \
priority=8 queue=default-small/default-small limit-at=0/0 \
max-limit=256000/256000 total-queue=default-small disabled=no
add name="Local Country" target-addresses=192.168.100.254/32 dst-address=0.0.0.0/0 \
interface=all parent=none packet-marks="Local Country Traffic" direction=both \
priority=8 queue=default-small/default-small limit-at=0/0 \
max-limit=1024000/1024000 total-queue=default-small disabled=no
Explanation
Address-list
First we create Local country address-list, where are placed list of network numbers belonging to ISPs in Latvia (any other country network addresses can be used instead). Full address-list configuration is not included (too many address-list entries), but address-list idea is clear. Networks added to the list 'Latvia':
/ ip firewall address-list
add list=Latvia address=159.148.0.0/16 comment="" disabled=no
add list=Latvia address=193.41.195.0/24 comment="" disabled=no
add list=Latvia address=193.41.33.0/24 comment="" disabled=no
add list=Latvia address=193.41.45.0/24 comment="" disabled=no
add list=Latvia address=193.68.64.0/19 comment="" disabled=no
add list=Latvia address=193.108.29.0/24 comment="" disabled=no
add list=Latvia address=193.108.144.0/22 comment="" disabled=no
add list=Latvia address=193.108.185.0/24 comment="" disabled=no
add list=Latvia address=193.109.211.0/24 comment="" disabled=no
add list=Latvia address=193.109.85.0/24 comment="" disabled=no
add list=Latvia address=193.110.8.0/23 comment="" disabled=no
add list=Latvia address=193.110.164.0/23 comment="" disabled=no
...
add list=Latvia address=193.111.244.0/22 comment="" disabled=no
Note, it's much easier to create/edit such list with Excel or any other similar program.
Mangle
First we add rule to mark connections that belong to local router's subnet (192.168.100.0/24). Second rule marks connections between local subnet and overseas networks. Third rule marks oversea packets and exclude them from mangle table (passtrough=no). Finally, the last rule places packet mark on all packets that belong to Local country traffic.
/ ip firewall mangle
add chain=prerouting src-address=192.168.100.0/24 action=mark-connection \
new-connection-mark="Con Entire Traffic" passthrough=yes \
comment="Mark-connection All Traffic" disabled=no
add chain=prerouting src-address=192.168.100.0/24 connection-mark="Con Entire \
Traffic" dst-address-list=!Latvia action=mark-connection \
new-connection-mark="Con Oversea" passthrough=yes comment="Mark-connection \
Oversea Traffic" disabled=no
add chain=prerouting connection-mark="Con Oversea" action=mark-packet \
new-packet-mark="Oversea traffic" passthrough=no comment="Mark-packet \
Oversea Traffic" disabled=no
add chain=prerouting action=mark-packet new-packet-mark="Local Country Traffic" \
passthrough=no comment="Mark-packet Local Country Traffic" disabled=no
Simple Queue
Queue configuration is quite simple in the particular case. 192.168.100.254 is the local network host. First rule sets limit 256k/256k to Oversea traffic for the particular host. Respectively second simple queue set limit 1M/1M for Local country traffic.
/ queue simple
add name="Oversea" target-addresses=192.168.100.254/32 dst-address=0.0.0.0/0 \
interface=all parent=none packet-marks="Oversea traffic" direction=both \
priority=8 queue=default-small/default-small limit-at=0/0 \
max-limit=256000/256000 total-queue=default-small disabled=no
add name="Local Country" target-addresses=192.168.100.254/32 dst-address=0.0.0.0/0 \
interface=all parent=none packet-marks="Local Country Traffic" direction=both \
priority=8 queue=default-small/default-small limit-at=0/0 \
max-limit=1024000/1024000 total-queue=default-small disabled=no
Per-Traffic Load Balancing
Introduction
Bandwidth management is an essential part of everyday operation for typcial ISPs, businesses, and even everday home users. There are many different types of management tools available to RouterOS users, QOS, rate-limiting, packet-limiting, to name a few.
I personally operate a wireless ISP, in an area that has no other type of convential high-speed internet (ie. cable, fibre, or DSL). Not having access to fibre myself, I am in a situation where the single fastest backbone connection I can get does not provide enough bandwidth for me to have only one connection. As a result of this limitation load-balancing multiple internet backbone connections is very important.
In the past I have used ECMP, persistent per connection styled load-balancing (see http://wiki.mikrotik.com/wiki/Load_Balancing), as well as various other methods. However, I found all of them lacking in various different areas (not load-balancing correctly, broken large HTTP downloads, IM problems, to name a few issues). I then investigated a way to give me more control over my bandwidth while minimizing the potential problems. The end result was a per-traffic type of load-balancing. This tutorial is designed address that one specific area in depth, at a later date, I may expand/add additional info on fail-over, QOS, and other topics.
Functions of RouterOS Used
Main functions of RouterOS used in this tutorial
- Firewall mangle rules
- Firewall address-lists
- Routing
Step 1 - How to break up to traffic
Before you even log onto your RouterOS box, you should have an idea of how you want to divide your traffic, and have an understanding of what traffic can and what traffic can't be broken up.
Here is an example of what you may want to attempt to seperate (in no particular order):
- HTTP traffic (port 80)
- SSL traffic (port 443)
- POP3 traffic (port 110)
- SMTP traffic (port 25)
- P2P traffic (various ports)
- Unknown traffic (various ports)
After making a list of the traffic type, and the ports they operate on, you need to look at the list and decide if it is at all even capable of being forced out a certain internet connection.
Using the above list as an example here is what I came up with:
- HTTP traffic (no problems found yet)
- SSL traffic (some issues, for normal SSL websites and 90% of all software it is not a problem, I'll explain why issues can arise later)
- POP3 traffic (no problems found yet)
- SMTP traffic (no problems found yet)
- P2P traffic (must go out same internet connection as Unknown traffic, I'll explain why this is later)
- Unknown traffic (must go out same internet connection as P2P traffic, I'll explain why this is later)
Now for a quick explanation of why there can be some issues depending on the traffic type. Some website/programs do not play friendly with multiple requests from different IP addresses, this is the reason why ECMP has so many problems. I will provide a simple solution to the rare conditions where load-balancing can't be completed.
Again using the above as an example lets explain where and why issues can arise. SSL - The beauty of a website is that there are seperate requests for different data, ie. loading pictures from 3 different sources would be a request to each respective server. The result is if a we have a website that uses both SSL and HTTP traffic, we know that in most cases the website will just answer the request without care of the originating IP address. However, and this is a special case, if the website/program developer checks where the requests are originating and they find that the IPs are different they may not successfully answer those requests (this can be by design or by accident). I have had 2 cases of this, in both casees it was secured medical websites that were using it as a method of protecting their data.
P2P and Unknown - I am addressing these together because the issue is one and the same. RouterOS doesn't identify P2P based on any single condition, but instead analyzes the packets, this means RouterOS needs time to watch the data before it realizes that is in fact P2P traffic. As a result RouterOS doesn't know the data is P2P until AFTER the connection is made. This is important becuase the only way to send data out a specific internet connection you must know what that traffic is BEFORE the connection is made. So as with P2P traffic, unknown traffic is just that, it is unknown. By marking the unknown traffic though you can control what internet connection is used for both P2P and the left over unknown traffic (very useful).
Step 2 - Setting up the network
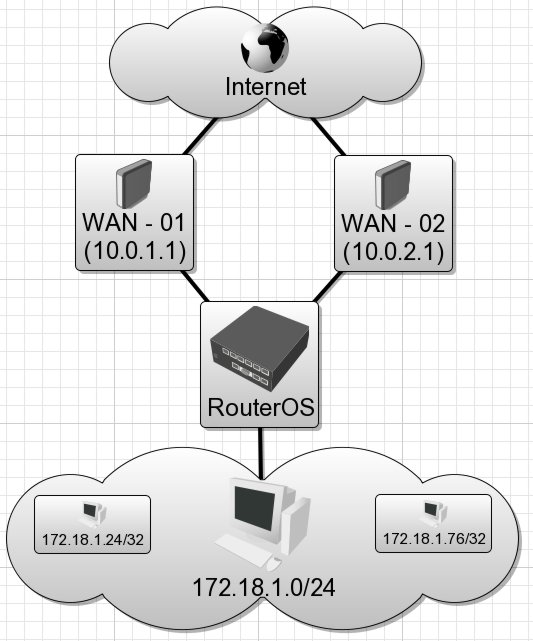
Before we get to the real point of this tutorial we need a fictious network we can use as an example.
- Client Computers (172.18.1.0/24)
- Internet Gateways (10.0.1.1/24, 10 0.2.1/24)
- RouterOS IPs (10.0.1.2/24, 10.0.2.2/24)
Assuming that the IPs, default routes, and DNS settings are already in place the following allows users to get internet access.
Create Address-List for permitted use of internet
/ ip firewall address-list
add list="Allowed - Internet" address=172.18.1.0/24 comment="" disabled=no
Create Address-List to bypass load-balancing
/ ip firewall address-list
add list="WAN - 01" address=172.18.1.24/32 comment="" disabled=no
add list="WAN - 02" address=172.18.1.76/32 comment="" disabled=no
Apply 'Masquerading' to the traffic leaving the WAN interfaces
/ ip firewall nat
add chain=srcnat action=masquerade out-interface="WAN - 01" src-address-list="Allowed - Internet" comment="Gateway 10.0.1.1/24" disabled=no
add chain=srcnat action=masquerade out-interface="WAN - 02" src-address-list="Allowed - Internet" comment="Gateway 10.0.2.1/24" disabled=no
Clients should be able to browse the internet, however only one internet connection would be used (the current default route in RouterOS)
Step 3 - Using RouterOS's Mangle tool to mark specific traffic
This following is the necessary RouterOS commands to mark particular traffic for a certain route, we are using the same example for traffic types as in the beginning, HTTP, SSL, POP3, SMTP, P2P, and Uknown
/ ip firewall mangle
add chain=prerouting action=mark-routing new-routing-mark="WAN - 01" src-address-list="WAN - 01" passthrough=no comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="WAN - 02" src-address-list="WAN - 02" passthrough=no comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="HTTP Traffic" passthrough=no dst-port=80 protocol=tcp comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="SSL Traffic" passthrough=no dst-port=443 protocol=tcp comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="POP3 Traffic" passthrough=no dst-port=110 protocol=tcp comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="SMTP Traffic" passthrough=no dst-port=25 protocol=tcp comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="P2P Traffic" passthrough=no p2p=all-p2p comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="Unknown Traffic" passthrough=no comment="" disabled=no
The first two lines provide a method of marking particular clients to bypass the load-balancing and use only a certain internet connection for all of their traffic. The following lines with mark traffic based on the the dst-port, notice how we are not passing though, also notice that we are marking all traffic, even if its not known, this always for a different internet connection to be specified for the Unknown and P2P instead of using the router's defult route. I also mark P2P seperately even though it must go out the same internet connection as Unknown traffic, I do this for a couple reasons, one is that I could easily stop all P2P traffic by disabling a route, and the other is in my RouterOS configuration I use alot of QOS, it it very easy to remember how everything is configured if the QOS mirrors the load-balancing.
So now we are marking traffic for their respective routes, next is to add those actual routes.
[edit] Step 4 - Using the Routing fuctions of RouterOS to force traffic out certain internet connections
This following is the necessary RouterOS commands to provide routes for the marked HTTP, SSL, POP3, SMTP, P2P, and Uknown Traffic
/ ip route
add dst-address=0.0.0.0/0 gateway=10.0.1.1 scope=255 target-scope=10 routing-mark="WAN - 01" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.2.1 scope=255 target-scope=10 routing-mark="WAN - 02" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.2.1 scope=255 target-scope=10 routing-mark="HTTP Traffic" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.2.1 scope=255 target-scope=10 routing-mark="SSL Traffic" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.2.1 scope=255 target-scope=10 routing-mark="POP3 Traffic" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.1.1 scope=255 target-scope=10 routing-mark="SMTP Traffic" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.1.1 scope=255 target-scope=10 routing-mark="P2P Traffic" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.1.1 scope=255 target-scope=10 routing-mark="Unknown Traffic" comment="" disabled=no
The first two line provide the routes necessary to give the clients that are not being load-balanced via traffic type the correct gateway to the internet. The remaining lines are the routes necessary to provide the appropiate gateway based on traffic type.
Step 5 - Review what you've created
What did you do:
- You intelligently broke up your internet traffic into different types
- You marked that traffic using the Mangle tool of RouterOS
- You created a bypass list to allow certain IP to bypass the Per-Traffic Load Balancing
- You assigned particular routes based on the traffic you marked with Mangle
[edit] Conclusion
What you have have done is very powerful and this tutorial provides just the tip of the iceberg so to say. The traffic types I have listed here are only a small amount of the total and you may want to add others (eg. DNS, terminal services, ICMP, etc). This can be used is a great deal of different ways be it in a small office enviroment (seperating your email usage from your browsing) or a large wireless ISP (for load-balancing). Some tips and final thoughts:
- Think though what you want to achieve before you start
- Pay attention to the type of traffic on each line (is it incoming intensive or outgoing intensive)
- Finally experiment, nothing better then finding better, faster and more intelligent ways to improve your services with little capital costs
Per-Traffic Load Balancing
Introduction
Bandwidth management is an essential part of everyday operation for typcial ISPs, businesses, and even everday home users. There are many different types of management tools available to RouterOS users, QOS, rate-limiting, packet-limiting, to name a few.
I personally operate a wireless ISP, in an area that has no other type of convential high-speed internet (ie. cable, fibre, or DSL). Not having access to fibre myself, I am in a situation where the single fastest backbone connection I can get does not provide enough bandwidth for me to have only one connection. As a result of this limitation load-balancing multiple internet backbone connections is very important.
In the past I have used ECMP, persistent per connection styled load-balancing (see http://wiki.mikrotik.com/wiki/Load_Balancing), as well as various other methods. However, I found all of them lacking in various different areas (not load-balancing correctly, broken large HTTP downloads, IM problems, to name a few issues). I then investigated a way to give me more control over my bandwidth while minimizing the potential problems. The end result was a per-traffic type of load-balancing. This tutorial is designed address that one specific area in depth, at a later date, I may expand/add additional info on fail-over, QOS, and other topics.
Functions of RouterOS Used
Main functions of RouterOS used in this tutorial
- Firewall mangle rules
- Firewall address-lists
- Routing
Step 1 - How to break up to traffic
Before you even log onto your RouterOS box, you should have an idea of how you want to divide your traffic, and have an understanding of what traffic can and what traffic can't be broken up.
Here is an example of what you may want to attempt to seperate (in no particular order):
- HTTP traffic (port 80)
- SSL traffic (port 443)
- POP3 traffic (port 110)
- SMTP traffic (port 25)
- P2P traffic (various ports)
- Unknown traffic (various ports)
After making a list of the traffic type, and the ports they operate on, you need to look at the list and decide if it is at all even capable of being forced out a certain internet connection.
Using the above list as an example here is what I came up with:
- HTTP traffic (no problems found yet)
- SSL traffic (some issues, for normal SSL websites and 90% of all software it is not a problem, I'll explain why issues can arise later)
- POP3 traffic (no problems found yet)
- SMTP traffic (no problems found yet)
- P2P traffic (must go out same internet connection as Unknown traffic, I'll explain why this is later)
- Unknown traffic (must go out same internet connection as P2P traffic, I'll explain why this is later)
Now for a quick explanation of why there can be some issues depending on the traffic type. Some website/programs do not play friendly with multiple requests from different IP addresses, this is the reason why ECMP has so many problems. I will provide a simple solution to the rare conditions where load-balancing can't be completed.
Again using the above as an example lets explain where and why issues can arise. SSL - The beauty of a website is that there are seperate requests for different data, ie. loading pictures from 3 different sources would be a request to each respective server. The result is if a we have a website that uses both SSL and HTTP traffic, we know that in most cases the website will just answer the request without care of the originating IP address. However, and this is a special case, if the website/program developer checks where the requests are originating and they find that the IPs are different they may not successfully answer those requests (this can be by design or by accident). I have had 2 cases of this, in both casees it was secured medical websites that were using it as a method of protecting their data.
P2P and Unknown - I am addressing these together because the issue is one and the same. RouterOS doesn't identify P2P based on any single condition, but instead analyzes the packets, this means RouterOS needs time to watch the data before it realizes that is in fact P2P traffic. As a result RouterOS doesn't know the data is P2P until AFTER the connection is made. This is important becuase the only way to send data out a specific internet connection you must know what that traffic is BEFORE the connection is made. So as with P2P traffic, unknown traffic is just that, it is unknown. By marking the unknown traffic though you can control what internet connection is used for both P2P and the left over unknown traffic (very useful).
Step 2 - Setting up the network
Before we get to the real point of this tutorial we need a fictious network we can use as an example.
- Client Computers (172.18.1.0/24)
- Internet Gateways (10.0.1.1/24, 10 0.2.1/24)
- RouterOS IPs (10.0.1.2/24, 10.0.2.2/24)
Assuming that the IPs, default routes, and DNS settings are already in place the following allows users to get internet access.
Create Address-List for permitted use of internet
/ ip firewall address-list
add list="Allowed - Internet" address=172.18.1.0/24 comment="" disabled=no
Create Address-List to bypass load-balancing
/ ip firewall address-list
add list="WAN - 01" address=172.18.1.24/32 comment="" disabled=no
add list="WAN - 02" address=172.18.1.76/32 comment="" disabled=no
Apply 'Masquerading' to the traffic leaving the WAN interfaces
/ ip firewall nat
add chain=srcnat action=masquerade out-interface="WAN - 01" src-address-list="Allowed - Internet" comment="Gateway 10.0.1.1/24" disabled=no
add chain=srcnat action=masquerade out-interface="WAN - 02" src-address-list="Allowed - Internet" comment="Gateway 10.0.2.1/24" disabled=no
Clients should be able to browse the internet, however only one internet connection would be used (the current default route in RouterOS)
Step 3 - Using RouterOS's Mangle tool to mark specific traffic
This following is the necessary RouterOS commands to mark particular traffic for a certain route, we are using the same example for traffic types as in the beginning, HTTP, SSL, POP3, SMTP, P2P, and Uknown
/ ip firewall mangle
add chain=prerouting action=mark-routing new-routing-mark="WAN - 01" src-address-list="WAN - 01" passthrough=no comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="WAN - 02" src-address-list="WAN - 02" passthrough=no comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="HTTP Traffic" passthrough=no dst-port=80 protocol=tcp comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="SSL Traffic" passthrough=no dst-port=443 protocol=tcp comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="POP3 Traffic" passthrough=no dst-port=110 protocol=tcp comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="SMTP Traffic" passthrough=no dst-port=25 protocol=tcp comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="P2P Traffic" passthrough=no p2p=all-p2p comment="" disabled=no
add chain=prerouting action=mark-routing new-routing-mark="Unknown Traffic" passthrough=no comment="" disabled=no
The first two lines provide a method of marking particular clients to bypass the load-balancing and use only a certain internet connection for all of their traffic. The following lines with mark traffic based on the the dst-port, notice how we are not passing though, also notice that we are marking all traffic, even if its not known, this always for a different internet connection to be specified for the Unknown and P2P instead of using the router's defult route. I also mark P2P seperately even though it must go out the same internet connection as Unknown traffic, I do this for a couple reasons, one is that I could easily stop all P2P traffic by disabling a route, and the other is in my RouterOS configuration I use alot of QOS, it it very easy to remember how everything is configured if the QOS mirrors the load-balancing.
So now we are marking traffic for their respective routes, next is to add those actual routes.
Step 4 - Using the Routing fuctions of RouterOS to force traffic out certain internet connections
This following is the necessary RouterOS commands to provide routes for the marked HTTP, SSL, POP3, SMTP, P2P, and Uknown Traffic
/ ip route
add dst-address=0.0.0.0/0 gateway=10.0.1.1 scope=255 target-scope=10 routing-mark="WAN - 01" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.2.1 scope=255 target-scope=10 routing-mark="WAN - 02" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.2.1 scope=255 target-scope=10 routing-mark="HTTP Traffic" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.2.1 scope=255 target-scope=10 routing-mark="SSL Traffic" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.2.1 scope=255 target-scope=10 routing-mark="POP3 Traffic" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.1.1 scope=255 target-scope=10 routing-mark="SMTP Traffic" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.1.1 scope=255 target-scope=10 routing-mark="P2P Traffic" comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.0.1.1 scope=255 target-scope=10 routing-mark="Unknown Traffic" comment="" disabled=no
The first two line provide the routes necessary to give the clients that are not being load-balanced via traffic type the correct gateway to the internet. The remaining lines are the routes necessary to provide the appropiate gateway based on traffic type.
Step 5 - Review what you've created
What did you do:
- You intelligently broke up your internet traffic into different types
- You marked that traffic using the Mangle tool of RouterOS
- You created a bypass list to allow certain IP to bypass the Per-Traffic Load Balancing
- You assigned particular routes based on the traffic you marked with Mangle
Conclusion
What you have have done is very powerful and this tutorial provides just the tip of the iceberg so to say. The traffic types I have listed here are only a small amount of the total and you may want to add others (eg. DNS, terminal services, ICMP, etc). This can be used is a great deal of different ways be it in a small office enviroment (seperating your email usage from your browsing) or a large wireless ISP (for load-balancing). Some tips and final thoughts:
- Think though what you want to achieve before you start
- Pay attention to the type of traffic on each line (is it incoming intensive or outgoing intensive)
- Finally experiment, nothing better then finding better, faster and more intelligent ways to improve your services with little capital costs
Load Balancing
With NAT and policy routing, with working HTTPS, IM and large downloads
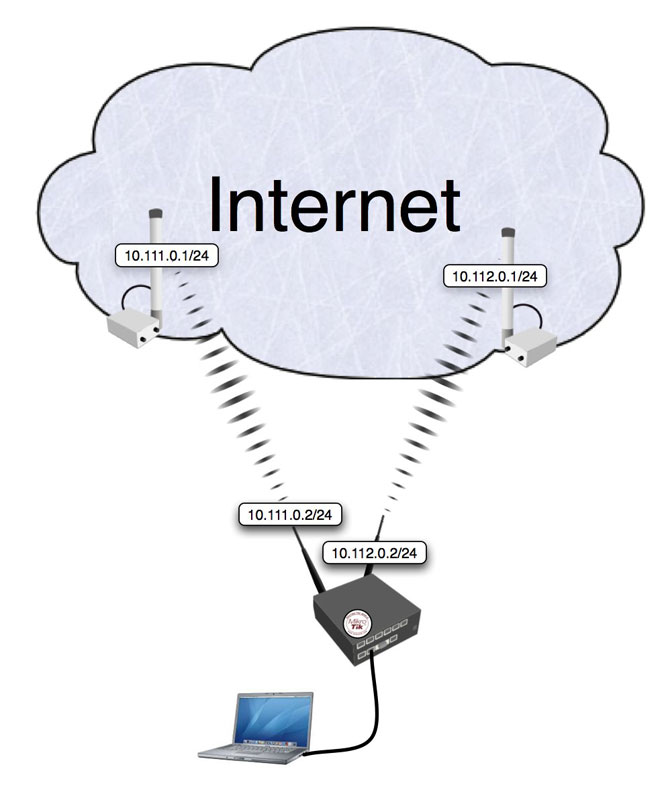
Consider the following network layout:
Quick Start for Impatient
Configuration export from the gateway router:
/ ip address
add address=192.168.0.1/24 network=192.168.0.0 broadcast=192.168.0.255 interface=Local comment="" \
disabled=no
add address=10.111.0.2/24 network=10.111.0.0 broadcast=10.111.0.255 interface=wlan2 \
comment="" disabled=no
add address=10.112.0.2/24 network=10.112.0.0 broadcast=10.112.0.255 interface=wlan1 \
comment="" disabled=no
/ ip firewall mangle
add chain=prerouting in-interface=Local connection-state=new nth=1,1,0 \
action=mark-connection new-connection-mark=odd passthrough=yes comment="" \
disabled=no
add chain=prerouting in-interface=Local connection-mark=odd action=mark-routing \
new-routing-mark=odd passthrough=no comment="" disabled=no
add chain=prerouting in-interface=Local connection-state=new nth=1,1,1 \
action=mark-connection new-connection-mark=even passthrough=yes comment="" \
disabled=no
add chain=prerouting in-interface=Local connection-mark=even action=mark-routing \
new-routing-mark=even passthrough=no comment="" disabled=no
/ ip firewall nat
add chain=srcnat connection-mark=odd action=src-nat to-addresses=10.111.0.2 \
to-ports=0-65535 comment="" disabled=no
add chain=srcnat connection-mark=even action=src-nat to-addresses=10.112.0.2 \
to-ports=0-65535 comment="" disabled=no
/ ip route
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=odd \
comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=even \
comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 comment="" \
disabled=no
Explanation
First we give a code snippet and then explain what it actually does.
Mangle
/ ip address
add address=192.168.0.1/24 network=192.168.0.0 broadcast=192.168.0.255 interface=Local comment="" \
disabled=no
add address=10.111.0.2/24 network=10.111.0.0 broadcast=10.111.0.255 interface=wlan2 \
comment="" disabled=no
add address=10.112.0.2/24 network=10.112.0.0 broadcast=10.112.0.255 interface=wlan1 \
comment="" disabled=no
The router has two upstream (WAN) interfaces with the addresses of 10.111.0.2/24 and 10.112.0.2/24. The LAN interface has the name "Local" and IP address of 192.168.0.1/24.
/ ip firewall mangle
add chain=prerouting in-interface=Local connection-state=new nth=1,1,0 \
action=mark-connection new-connection-mark=odd passthrough=yes comment="" \
disabled=no
First we take every second packet that establishes new session (note connection-state=new), and mark it with connection mark "odd". Consequently all successive packets belonging to the same session will carry the connection mark "odd". Note that we are passing these packets to the second rule (passthrough=yes) to place a routing mark on these packets in addition to the connection mark.
add chain=prerouting in-interface=Local connection-mark=odd action=mark-routing \
new-routing-mark=odd passthrough=no comment="" disabled=no
The rule above places the routing mark "odd" on all packets that belong to the "odd" connection and stops processing all other mangle in prerouting chain rules for these packets.
add chain=prerouting in-interface=Local connection-state=new nth=1,1,1 \
action=mark-connection new-connection-mark=even passthrough=yes comment="" \
disabled=no
add chain=prerouting in-interface=Local connection-mark=even action=mark-routing \
new-routing-mark=even passthrough=no comment="" disabled=no
These rules do the same for the remaining half of the traffic as the first two rules for the first half of the traffic.
The code above effectively means that each new connection initiated through the router from the local network will be marked as either "odd" or "even" with both routing and connection marks.
NAT
/ ip firewall nat
add chain=srcnat connection-mark=odd action=src-nat to-addresses=10.111.0.2 \
to-ports=0-65535 comment="" disabled=no
add chain=srcnat connection-mark=even action=src-nat to-addresses=10.112.0.2 \
to-ports=0-65535 comment="" disabled=no
All traffic marked "odd" is being NATted to source IP address of 10.111.0.2, while traffic marked "even" gets "10.112.0.2" source IP address.
Routing
/ ip route
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=odd \
comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=even \
comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 comment="" \
disabled=no comment="gateway for the router itself"
For all traffic marked "odd" (consequently having 10।111.0.2 translated source address) we use 10.111.0.1 gateway. In the same manner all traffic marked "even" is routed through the 10.112.0.1 gateway. Finally, we have one additional entry specifying that traffic from the router itself (the traffic without any routing marks) should go to 10.112.0.1 gateway.
सोर्स = ह्त्त्प://विकी.मिक्रोतिक.कॉम
PCQ Examples
Per Connection Queue (PCQ) is a queuing discipline that can be used to dynamically equalize or shape traffic for multiple users, using little administration.
Equal Bandwidth for a Number of Users
Use PCQ type queue when you need to equalize the bandwidth [and set max limit] for a number of users. We will set the 64kbps download and 32kbps upload limits.
There are two ways how to make this: using mangle and queue trees, or, using simple queues.
1. Mark all packets with packet-mark all:
/ip firewall mangle add chain=prerouting action=mark-packet new-packet-mark=all passthrough=no
2. Setup two PCQ queue types - one for download and one for upload. dst-address is classifier for user's download traffic, src-address for upload traffic:
/queue type add name="PCQ_download" kind=pcq pcq-rate=64000 pcq-classifier=dst-address
/queue type add name="PCQ_upload" kind=pcq pcq-rate=32000 pcq-classifier=src-address
3. Finally, two queue rules are required, one for download and one for upload:
/queue tree add parent=global-in queue=PCQ_download packet-mark=all
/queue tree add parent=global-out queue=PCQ_upload packet-mark=all
If you don't like using mangle and queue trees, you can skip step 1, do step 2, and step 3 would be to create one simple queue as shown here:
/queue simple add queue=PCQ_upload/PCQ_download target-addresses=192.168.0.0/२४
सोर्स = ह्त्त्प://विकी.मिक्रोतिक.कॉम
TransparentTrafficShaper
This example shows how to configure a transparent traffic shaper. The transparent traffic shaper is essentially a bridge that is able to differentiate and prioritize traffic that passes through it.
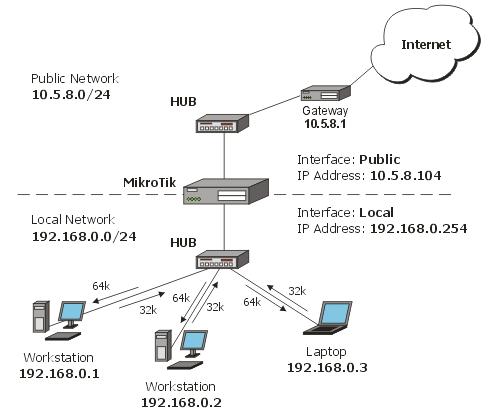
Consider the following network layout:
We will configure one queue limiting the total throughput to the client and three sub-queues that limit HTTP, P2P and all other traffic separately.
Configuration snippet from the MikroTik router:
/ interface bridge
add name="bridge1"
/ interface bridge port
add interface=ether2 bridge=bridge1
add interface=ether3 bridge=bridge1
/ ip firewall mangle
add chain=prerouting protocol=tcp dst-port=80 action=mark-connection \
new-connection-mark=http_conn passthrough=yes
add chain=prerouting connection-mark=http_conn action=mark-packet \
new-packet-mark=http passthrough=no
add chain=prerouting p2p=all-p2p action=mark-connection \
new-connection-mark=p2p_conn passthrough=yes
add chain=prerouting connection-mark=p2p_conn action=mark-packet \
new-packet-mark=p2p passthrough=no
add chain=prerouting action=mark-connection new-connection-mark=other_conn \
passthrough=yes
add chain=prerouting connection-mark=other_conn action=mark-packet \
new-packet-mark=other passthrough=no
/ queue simple
add name="main" target-addresses=10.0.0.12/32 max-limit=256000/512000
add name="http" parent=main packet-marks=http max-limit=240000/500000
add name="p2p" parent=main packet-marks=p2p max-limit=64000/64000
add name="other" parent=main packet-marks=other max-limit=128000/128000
Each piece of code is followed by the explanation of what it actually does.
/ interface bridge
add name="bridge1"
/ interface bridge port
add interface=ether2 bridge=bridge1
add interface=ether3 bridge=bridge1
We create a new bridge interface and assign two ethernet interfaces to it. Thus the prospective traffic shaper will be completely transparent to the client.
/ ip firewall mangle
add chain=prerouting protocol=tcp dst-port=80 action=mark-connection \
new-connection-mark=http_conn passthrough=yes
add chain=prerouting connection-mark=http_conn action=mark-packet \
new-packet-mark=http passthrough=no
All traffic destined to TCP port 80 is likely to be HTTP traffic and therefore is being marked with the packet mark http. Note, that the first rule has passthrough=yes while the second one has passthrough=no. (You can obtain additional information about mangle at http://www.mikrotik.com/docs/ros/2.9/ip/mangle)
/ ip firewall mangle
add chain=prerouting p2p=all-p2p action=mark-connection \
new-connection-mark=p2p_conn passthrough=yes
add chain=prerouting connection-mark=p2p_conn action=mark-packet \
new-packet-mark=p2p passthrough=no
add chain=prerouting action=mark-connection new-connection-mark=other_conn \
passthrough=yes
add chain=prerouting connection-mark=other_conn action=mark-packet \
new-packet-mark=other passthrough=no
Same as above, P2P traffic is marked with the packet mark p2p and all other traffic is marked with the packet mark other.
/ queue simple
add name="main" target-addresses=10.0.0.12/32 max-limit=256000/512000
We create a queue that limits all the traffic going to/from the client (specified by the target-address) to 256k/512k.
/ queue simple
add name="http" parent=main packet-marks=http max-limit=240000/500000
add name="p2p" parent=main packet-marks=p2p max-limit=64000/64000
add name="other" parent=main packet-marks=other max-limit=128000/128000
All sub-queues have the main queue as the parent, thus the aggregate data rate could not exceed limits specified in the main queue. Note, that http queue has higher priority than other queues, meaning that HTTP downloads are prioritized।
सोर्स=ह्त्त्प://विकी.मिक्रोतिकी.com
14 Step Configuration of mikrotik using ADSL speedy internet
This articel i explain how to configuration mikrotik using pc for router।
1. Configuration position of ADSL connection
modem —Mikrotik—-Switch —– Client
Client
a. Modem IP –>> 192.168.1.1
b. Mikrotik Using 2 Interface - Ether1 —->> 192.168.1.2
- Ether1 —->> 192.168.0.254
c. Switch — Client ip 192.168.0.1-253
2. Configuration step router pc mikrotik
a. add ip address to interface 1
/ip address add interface=ether1 address = 192.168.1.1 netmask= 255.255.255.0
b. add ip address to interface2
/ip address add interface=ether2 address = 192.168.0.1 netmask= 255.255.255.0
c. to see input of interface
/interface print
d. Set Value name off interface
/inteface set 0 name=”Public” –>> For Modem
/inteface set 1 name=”Lan” –>> For Lan
e. set routing for net ( modem )
/ip route add gateway=192.168.0.1
f. set dns server ISP
/ip dns set primary-dns=203.130.193.74 secondary-dns=202.134.0.155
/ip dns set allow-remote-requests=yes
g. set of nat the router pc to sharing bw to lan
/ip firewall nat add chain=srcnat out-inteface=Public action=masquerade
Services
Thursday, July 12, 2007Service Support
Domain Registration
Web Hosting
Graphic Designs
Networking
Security
IT Consulting
Domain Name
Kami melayani pembelian domain .com, .net, .org, .info, .biz, .us, .tv dan .name. Tersedia juga domain co.id, net.id, or.id. Untuk masing-masing pembelian tahun, 2 tahun, 3 tahun, 4 tahun, 5 tahun, 6 tahun, 7 tahun, 8 tahun, 9 tahun ndan 10 tahun. denagn harga yang bersaing. Bebas fee. Anda juga mendapatkan email dengan format nama-anda@nama-anda.com.
Untuk pembelian domain 5 tahun smpai 10 tahun gratis webhosting yang mendukung cgi, SSH, php, ASP untuk satu tahun. Unlimited forwarding email, pop3, smtp dan nanti spam. Untuk informasi lebih lanjut silahkan hubungi Harry Chan Putra Networks Inc. keatas
Hosting Services
Hosting adalah server tempat anda meletakkan halaman web anda, database web ananda, file data web anda. Pilihannya anda bisa menggunakan dedicated server atau co-location server.
Web Hosting
Selain bisa memilih jenis server, anda juga bisa memilih Operating System server ananda, seperti :IIS(Internet Information Service), Apache web server, Linux web server(RedHat,FreeBSD). Dengan fee yang ringan anda sudah memiliki server handal untuk website anda. Yang akan menunjang bisnis anda. Untuk upload anda dapat memilih menggunakan Program FTP atau Web Upload. Data anda akan dijaga oleh admin-admin kami yng telah berpengalaman dalam keamanan data dan keamanan server. .
WebMail Hosting
Untuk mendukung promosi perusahaan anda dengan account e-mail karyawan pada website anda, kami menyediakan webmail server yang handal, mendukung unlimited account, kapasitas besar, access cepat, forwarding, pop3, smtp, antivirus dan spam. Dengan tampilan yang dapat di kustomisasi dan bebas iklan. Menjadikan perusahaan anda lebih percaya diri dan bonafit.
Shell Hosting
Butuh shell account yang handal dan stabil? Kami menyediakan jawabannya. Dengan dukungan server High End dual prosesor Xeon, anda akan mendapatkan shell account yang super cepat, dapat diakses darimana saja, kapan saja dan tanpa server down.
Virtual Host
Ingin membuat bot yang online 24 jam, meletakan psyBNS, eggBNC, PortScanner dll. Anda membutuhkan virtual host yang handal dan cepat. Kami melayani virtual host dengan harga yang bersaing dan performa yang tinggi. Terdiri dari virtual host Linux dan Windows. Anda dapat mencoba 7 day trial version dan rasakan virtual host yang handal dan stabil.keatas
Networking
Sharing file dan data sangat dibutuhkan sekarang ini. Dalam perusahaan misalnya, suatu ruangan tak perlu lagi datang ke bagian lain hanya untuk mengambil data/file atau sekedar melihat data file. Bahkan bagi yang berbeda lantai atau berbeda tempat dapat dibayangkan waktu yg habis hanya untuk melihat/mengambil data/file. Maka Jaringan yang terkoneksi satu sama lain sangat diperlukan.
LAN
Untuk solusi sharing data/file/internet/intrane/printer dapat diterapkan Lokal Area Network(LAN). Layanan kami mulai dari perencanaan, pensetingan dan pemeliharaan. Kami juga menyediakan Hardware dan Software untuk jaringan seperti : LAN Card, HUB, Kabel, Konektor dan aksesoris lain. Layanan LAN mulai dari 2 komputer sampai ratusan komputer. Teknisi-teknisi profesional kami akan mengurusnya untuk anda
WAN
WAN adalah solusi bagi suatu perusahaan/kantor yang berdomisili di daerah yang sama tapi dipisahkan jarak yang jauh. Seperti kantor cabang, gedung yang berbeda. Untuk itu kami telah menyediakan solusi Wide Area Network(WAN). Anda dapat mempercayakan solusi bisnis ini denagn tenaga-tenaga ahli kami yang telah berpengalaman dalam bidangnya.
WINDOWS and LINUX
Sekarang ini terdapat pilihan Operating System yang akan digunaka. Anda dapat menggunakan Jaringan berbasis Windows yang sudah familiar dengan anda. Atau dapat menggunakan Operating System berbasis Linux yang menawarkan Keamanan jaringannya yang stabil. Semua terserah anda, mau mekakai Linux atau Windows. Atau bahkan menggunakan keduanya.keatas
Security
Security sangat dibutuhkan saat ini, baik keamanan data maupun keamanan jaringan, mengingat semakin banyaknya hacker, cracker dan carder di internet. Serta bebasnya informasi-informasi bug bug terbaru, exploit, scanner dll.
Data Security
Anda pasti tak ingin kehilangan data penting anda baik oleh virus, kegagalan hardware, masalah software dan hacker. Untuk itu kami memberikan layanan data security. Kami menyediakan tenaga-tenaga handal dan software-software backup dan data recovery.
Networks Security
Bila jaringan anda tidak aman maka resiko kehilangan data tau kerugian lain akan semakin besar. Lindungi jaringan anda dari orang-orang yang tak berhak dan serangan dari luar. Salah satu caranya adalah dengan membuat keamanan berlapis. Dengan memakai proxy server dan firewall. Kami menyediakan harware dan software untuk keamanan jaringan. Kami juga menyediakan layanan maintenance jaringan dan perbaikan jaringan.
Web Security
Perkembangan TI (Teknologi Informasi) kian hari semakin pesat. Semua orang dapat mengakses informasi dari internet baik yang baik maupun yang destruktif. Untuk itu amankan website anda dari hacker, cracker dan carder yang mencoba masuk, mencuri data anda atau sekedar melihat data disitus anda. Kami menyediakan team Hacker yang akan terus memonitoring website anda, mempatch sistem anda, memberitahu anda kelemahan sistem anda dan jasa konsultasi.
Hacking, Cracking, Phreaking, Carding
Anda pasti tak mau website anda, website perusahaan anda dimasuki atau di serang hacker dan cracker. Atau data kartu kredit customer anda di curi carder. Bayangkan kerugian yang akan anda alami bila mengabaikan keamanan vulnerable suatu sistem. Maka dari itu kami menyediakan jasa keamanan penuh untuk jaringan anda, webs_te anda dan data anda.keatas
IT Consulting
Anda akan membeli komputer, memperbaharui komputer di kantor anda, perusahaan anda, atau berencana akan membuat jaringan di rumah anda, kantor anda atau peruhaan anda? Bingung apa yang harus dilakukan.. hubungi kami!.
Hardware & Software
Kami telah melakukan benchmarking software-software di pasaran. Juga melakukan tes perbandingan hardware terbaru. Bagi anda yang pusing memilih yang mana yang terbaik dan sesuai dengan keinginan dan dana anda, kami menerima konsultasi tentang hardware dan software. Baik software OS, Aplikasi, Game, dll.
Networks
Kami menerima konsultasi tentang jaringan, kebutuhan, biaya, hardware dan software, keamanan, maintenance dll. Silahkan serahkan semuanya pada team kami yang telah ahli dibidang networking, dan telah berpengalaman dalam jaringan baik jaringan kecil maupun yang berskala besar.
Internet
Anda memerlukan konsultasi tentang internet, pengenalan, fasilitas di internet, search engine, e-mail, situs, ftp, download dll. Silahkan anda hubungi Harry Chan Putra Networks Inc. Perusahaan yang telah berpengalaman di internet sejak 2002. Kami juga menyediakan tenaga ahli yang siap memberikan jasa pengenalan dan pelatihan di kantor anda, perusahaan anda atau instansi tempat anda bekerja. Security (Hacking, Cracking, Phreaking, Carding)
Kami menyediakan elatihan hacking, cracking dan teknik carding. Untuk mengalahkan musuh kita harus tau cara kerjanya, jadi pengetahuan ini hanyalah pengenalan cara kerja mereka. Sehingga kita dapat menanggulanginya. Kami akan melatih anda menjadi administrator yang ahli dalam keamanan jaringan dan internet. keatas
Project
1. Moving Galang.Net Using DVB To SDSL astinet Telkom 2 MB. At 2 Mei 2007
2. Re-Setup Router BGP system Adira Finance At 20 Mei 2007
3. Setup Hotspot Bank BNI 46 Proklamasi Padang At 1 Juni 2007
4. Setup HotSpot Bank BNI 46 Wilayah Padang Baru At 1 Juni 2007
5. Trafic Network Analizing BANK BPD Payakumbuh At 6 Juli 2007
6. DSLAM ADSL how to project.
7. Configuration Router juniper siemens for jardiknas ( indonesian education network ) from indonesian education department. 32 location on west sumatera. december 2007 - december 2008. cluster 1- cluster 3
8. Noding PLN With Telabs Mini Node. For 4 MB Backhole.
Portofolio
a. Web Site :
1. PIMNAS 2005 http://www.pimnas2005.com/
2. Alumni Kedoteran Unand http://www.alumnifdok.org/
b. Desain Grapis :
a. Majalah Dinamika Faperta Unand
b. Creative Design PIMNAS 2005 Unand
c. Software
1. System Informasi Geografis dan System Analisa Tanaman Kentang Sumbar Using Visual Basic & Crystal Report.
2. GIS Analisa Dampak Lingkungan Sumatera Barat 2006.
3. GIS Gerakan Rehabilitas Hutan 2005.
4. GIS Proyeksi Gempa Bumi Sumatera Barat 50 Tahun.
c
e. Linux/BSD Router
1. Setup Router Proxy Server ( FreeBSD 4.4 ) Pagarnet Pagaruyung Internet Cafe Jl. Sudirman , Agustus 2000.
2. Setup Router Proxy Server ( Linux Distro Centos ) Warnet Yusa Karya Abadi Jl. Terandam, 5 July 2005
3. Setup Warnet Game Dan Router With Mikrotik FIL@NET Jl. Kampung Nias Dalam Padang, 1 Agustus 2005
4. Setup Mikrotik DJ-Net for net games Jl. Niaga Padang, 23 Agustus 2005
5. Setup Router Mikrotik Dan Proxy Server Warnet Primadona Jl. Kampus Unand Pasar baru, 1 Oktober 2006.
6. Setup Router Proxy Server ( Linux Distro Centos ) Warnet Kashiko.net Pasar Baru Kampus Unand, 1 Oktober 2006.
7. Setup Router Proxy Server ( Linux Distro Centos ) Warnet Palimo.Net Pasar Baru Kampus Unand, 5 Oktober 2006.
8. Setup Router Proxy Server ( Linux Distro Centos ) Warnet CyberZone Jl. Veteran, 1 Novermber 2006
9. Setup Router Mikrotik Dan Proxy Server Fakultas Kedokteran Universitas Andalas, 23 November 2006.
10. Setup Router Mikrotik Dan Proxy Server Warnet Debes.net Jl. Adinegoro Padang, 23 November 2006
11. Setup Router Mikrotik Dan Proxy Bravo Tour And Travel Jl. Hayam Wuruk. Inna Muara Hotel, 25 November 2006
12. Setup Router Mikrotik Dan Proxy Server Pantara Tour And Travel Jl. M Yamin. 27 November 2006
13. Setup Proxy Server E_WEB.Com Jl. M hatta. ( Simpang Anduring ). 3 Desember 2006
14. Proxy Server Oasis.net Jl. Andalas ( Simpang Azizi ), 4 Desember 2006
15. Setup HOTSPOT Wireles Bapak Teddy Hidayat Jln. Komplek Resident Mangunsakoro, 5 Desember 2006
16. Setup Linux Proxy Server surya.Net Jln. Dr Sutomo, 27 Desmber 2006
17. Mindahin Galang.Net Ke astinet Telkom 2 MB, 29 Februari 2007
18. Setup Ulang Router BGP system Adira Finance, 1 Maret 2007
19. Setup Hotspot Bank BNI 46 Proklamasi Padang, 23 Maret 2007
20. Setup HotSpot Bank BNI 46 Wilayah Padang Baru, 28 Maret 2007
21. Router Mikrotik Games Center X.Net Jln. Nipah Padang, 1 April 2007
22. Analisis Network Warnet Primadata.Net, Speed.Net Jalan Paus dan Planet dan Vega.Net Jalan S.Parman. Dari Attacking Local And Public akibat worm dan virus serta aktivitas hacker, 26 April 2007
23. Setup Loadbalancing machine on Central.Net, using Prolink load balancing machine with 2 line speedy internet, and mikrotik for the bandwith limited. 21 July 2007
24. Setup LoadBalancing using Mikrotik on Phonix.Net Games. 3 Agustus 2007
25. Re-setup Tsunami Watch Radio At RRI padang using Speedy Internet and 2wcom radio.
26. Re Setup Cisco Router VPN ip PT. Columbia
27. Reconfigure PC router Fantasy.Net Jl. Moh. Hatta, Install with Muhammad Riza.
28. Configuration Router juniper siemens for jardiknas ( indonesian education network ) from indonesian education department. 32 location on west sumatera. december 2007 - december 2008. cluster 1- cluster 3
29. Setup Loadbalancing machine on DD.Net on Adinegoro street, using Prolink load balancing machine with 3 line speedy internet, and mikrotik for the bandwith limited. and linux proxy server. december 2007 and runing whell at januari 2008
30. Configuration Cisco Router for Chief west sumatera Indonesia Police Video Confrence with indonesia president. februari 2008.
31. Configuration Junpier Route AJB ( Asuransi Jiwa Bersama ) Bumiputera Padang. at februari 2008
32. Make Mikrotik Load Balancing For 3 ADSL Line to Flamboyan.net. Prof. Hamka Street. and using freebsd web proxy on maret 2008
33. Make Mikrotik Load Balancing For 2 ADSL Line to 99.net. Panggilun Mountain Street. and using freebsd web proxy. on maret 2008
34. Help to configuration Governece Co-Location Server. http://www.sumbarprov.go.id at april 2008
35. Help Configuration SISKOHAT Cisco Router. at mei 2008
36.Help Configuration migration bandwith at west sumatera Governece. fail over from Indosat to Telkom. using 1 mbps. mei 2008
37. Setup HOTSPOT Wireles BANK BNI 1946 Jln. A. Yani, Padang, Mei 2008
38. Config Online ProNews FM Radio, http://pronewsfm.listen2myradio.com/. mei 2008
E-Book
A. Telkom Flexi
Akses Data Via Packet Data Network
Akses Data Via Telkomnet Instan
B. Telkomsel
Using USB / Datacard
Setting Modem Huawei e620_datacard
Setting Novatel Wireless Datacard
Setting Sierra Wireless Aircard
Using Headset 3G/HSDPA
C. FreeBSD
D. Settingan Antivirus
CV
CV
My information
- Full Name: Harry Chan Putra, SP. MTCNA
- Date of Birth: 31 Agutus 1981
- Nationality: Indonesian
- Phone : +62-751-7825678
- Mobile : +62-81363696000
- Email: harrychanputra.sp@gmail.com
- YM : harrychanputra
Profile
Interest with web design ,web programming, System Intergrator, Network Admin Using Linux, BSD, and Windows, GIS and CAD experience more than 2 years in the field of web, multimedia, print design, System Intergrator, Network Admin Using Linux, BSD, and Windows. Works well as individually, or part of a team.
Skill
Software
- Experience with HTML Editor such as Frontpage, Dreamweaver, PHPEdit, EditPlus, Macromedia Home Site
- Experience with Design’s software such as Corel Draw, Adobe Photoshop, Macromedia Fireworks
- Experience with CAD software such as AutoCad, QuciCad.
- Experience with GIS software such as AutoCadMap, MapInfo, ArcView.
- Experience with Linux ( Rethat, Centos, Ipcop, Smottwall, Mikrotik, Slackware ) BSD ( FreeBSD, Open BSD).
- Experience with Network Adminsitrator Using Security ( Iptables ), Qos ( HTB), Proxy ( Squid, Winproxy, Winroute ).
- Experience with System Intergrator Setup For Wireles And Wired Lan, VSAT (DVB ).
- Good at Googling For Search Solution Some Problem
- Able Otodidak (learn self)
Language
- Able to hand code Javascript, HTML 4, XHTML 1.1, CSS and Visaul Basic 6.0
- Experience with Server-side Scripting Language such as PHP
- Experience with Database such as Microsoft Access, MySQL
Job History
- Technical Support PT. Telkom Telkom Speedy And Telkom SDSL Netwok On Padang. Oktober 2006 - Until Now
Main network Linux Router and BSD router, with proxy, firewall and HTB for clint access.
- Web Designer /Web Developer And Network Administrator
PT. IGASAR ( Semen Padang Group ) http://igasar.net.tf/
Januari 2005 - 20 Oktober 2006
Designing the template, Converting Design to Mambo or Joomla Template, Build Wirelles Lan and Wire lan, setup router using mikrotik and linux. Support SQL Database for Iventory and maintence using Zahir Accounting 5.1
- Technical Support Cv. Yusa Karya Abadi
July 2005 - Until Now
Design and development network infrastructure using Wired Lan, manage using linux router and mikrotik router.
- Technical Support PT. Andalas Media
July 2004 - September 2004
Main network using cisco catalyst 2600, Linux Router and BSD router, with proxy, firewall and HTB.
- Instructor
Mei 2002 - Mei 2003
Instructor of Web Design/Web Programming and Linux Networing at LP3I Cab. Padang.
- Contributor Portal Lintau.com ( July 2003 s/d sekarang)
- Dinamika – University Pers At Agriculture Faculty,
June 2001 – 2002
Design and layout dinamika magazine using Adobe Pagemaker 6.5. and Adobe Photoshop.
- Web Designer /Web Developer And Network Administrator Pagaruyung Ineternet Cafe
August 2000 Until now
Design and development network infrastructure using Wired Lan, manage using linux router and mikrotik router. Main language for Web Desingner / Web Developer using HTML 4.0, PHP, CSS 1.0 and Javascript. Create some Web Portal of Pagaruyung Internet Cafe such as http://alumnifkua.org/, http://pimnas2005.com/
- Pemerhati Keamanan Jaringan Internet ( Minangcrew Network Security Team )
( August 1998 - Until Now ) .
Reporting about bug and problem with network and network application such as web programming and wirelles security.
Project History
a. Web Site :
1. PIMNAS 2005 http://www.pimnas2005.com/
2. Alumni Kedoteran Unand http://www.alumnifdok.org/
b. Desain Grapis :
1. Majalah Dinamika Faperta Unand
2. Creative Design PIMNAS 2005 Unand
c. Software
1. System Informasi Geografis dan System Analisa Tanaman Kentang Sumbar Using Visual Basic & Crystal Report.
2. GIS Analisa Dampak Lingkungan Sumatera Barat 2006.
3. GIS Gerakan Rehabilitas Hutan 2005.
4. GIS Proyeksi Gempa Bumi Sumatera Barat 50 Tahun.
d. Public Speaker
1. Linux Seminar "Apa Itu Linux ?" Politeknik Universitas Andalas, 2002
2. Network Security And Open Source, "Amankan Jaringan Anda !!", Aula Fakultas Ekonomi Universitas Andalas, 2003
3. Web Desain And Programming Workshop Universitas Negeri Padang, 2004
4. Web Desain And Programming Workshop Universitas Putra Indonesia, 2007
5. Seminar Security One Day "Hacking Attacking", 2007
6. Seminar ADSL Technology With PT.Telkom, 2008
7. Seminar Hacker Attack, Politeknik Universitas Andalas, 2008
e. Linux/BSD Router
1. Setup Router Proxy Server ( FreeBSD 4.4 ) Pagarnet Pagaruyung Internet Cafe Jl. Sudirman , Agustus 2000.
2. Setup Router Proxy Server ( Linux Distro Centos ) Warnet Yusa Karya Abadi Jl. Terandam, 5 July 2005
3. Setup Warnet Game Dan Router With Mikrotik FIL@NET Jl. Kampung Nias Dalam Padang, 1 Agustus 2005
4. Setup Mikrotik DJ-Net for net games Jl. Niaga Padang, 23 Agustus 2005
5. Setup Router Mikrotik Dan Proxy Server Warnet Primadona Jl. Kampus Unand Pasar baru, 1 Oktober 2006.
6. Setup Router Proxy Server ( Linux Distro Centos ) Warnet Kashiko.net Pasar Baru Kampus Unand, 1 Oktober 2006.
7. Setup Router Proxy Server ( Linux Distro Centos ) Warnet Palimo.Net Pasar Baru Kampus Unand, 5 Oktober 2006.
8. Setup Router Proxy Server ( Linux Distro Centos ) Warnet CyberZone Jl. Veteran, 1 Novermber 2006
9. Setup Router Mikrotik Dan Proxy Server Fakultas Kedokteran Universitas Andalas, 23 November 2006.
10. Setup Router Mikrotik Dan Proxy Server Warnet Debes.net Jl. Adinegoro Padang, 23 November 2006
11. Setup Router Mikrotik Dan Proxy Bravo Tour And Travel Jl. Hayam Wuruk. Inna Muara Hotel, 25 November 2006
12. Setup Router Mikrotik Dan Proxy Server Pantara Tour And Travel Jl. M Yamin. 27 November 2006
13. Setup Proxy Server E_WEB.Com Jl. M hatta. ( Simpang Anduring ). 3 Desember 2006
14. Proxy Server Oasis.net Jl. Andalas ( Simpang Azizi ), 4 Desember 2006
15. Setup HOTSPOT Wireles Bapak Teddy Hidayat Jln. Komplek Resident Mangunsakoro, 5 Desember 2006
16. Setup Linux Proxy Server surya.Net Jln. Dr Sutomo, 27 Desmber 2006
17. Mindahin Galang.Net Ke astinet Telkom 2 MB, 29 Februari 2007
18. Setup Ulang Router BGP system Adira Finance, 1 Maret 2007
19. Setup Hotspot Bank BNI 46 Proklamasi Padang, 23 Maret 2007
20. Setup HotSpot Bank BNI 46 Wilayah Padang Baru, 28 Maret 2007
21. Router Mikrotik Games Center X.Net Jln. Nipah Padang, 1 April 2007
22. Analisis Network Warnet Primadata.Net, Speed.Net Jalan Paus dan Planet dan Vega.Net Jalan S.Parman. Dari Attacking Local And Public akibat worm dan virus serta aktivitas hacker, 26 April 2007
23. Setup Loadbalancing machine on Central.Net, using Prolink load balancing machine with 2 line speedy internet, and mikrotik for the bandwith limited. 21 July 2007
24. Setup LoadBalancing using Mikrotik on Phonix.Net Games. 3 Agustus 2007
25. Re-setup Tsunami Watch Radio At RRI padang using Speedy Internet and 2wcom radio.
26. Re Setup Cisco Router VPN ip PT. Columbia
27. Reconfigure PC router Fantasy.Net Jl. Moh. Hatta, Install with Muhammad Riza.
28. Configuration Router juniper siemens for jardiknas ( indonesian education network ) from indonesian education department. 32 location on west sumatera. december 2007 - december 2008. cluster 1- cluster 3
29. Setup Loadbalancing machine on DD.Net on Adinegoro street, using Prolink load balancing machine with 3 line speedy internet, and mikrotik for the bandwith limited. and linux proxy server. december 2007 and runing whell at januari 2008
30. Configuration Cisco Router for Chief west sumatera Indonesia Police Video Confrence with indonesia president. februari 2008.
31. Configuration Junpier Route AJB ( Asuransi Jiwa Bersama ) Bumiputera Padang. at februari 2008
32. Make Mikrotik Load Balancing For 3 ADSL Line to Flamboyan.net. Prof. Hamka Street. and using freebsd web proxy on maret 2008
33. Make Mikrotik Load Balancing For 2 ADSL Line to 99.net. Panggilun Mountain Street. and using freebsd web proxy. on maret 2008
34. Help to configuration Governece Co-Location Server. http://www.sumbarprov.go.id at april 2008
35. Help Configuration SISKOHAT Cisco Router. at mei 2008
36.Help Configuration migration bandwith at west sumatera Governece. fail over from Indosat to Telkom. using 1 mbps. mei 2008
37. Setup HOTSPOT Wireles BANK BNI 1946 Jln. A. Yani, Padang, Mei 2008
38. Config Online ProNews FM Radio, http://pronewsfm.listen2myradio.com/. mei 2008