SNMP PHP
Tuesday, November 27, 2007This small example is a PHP script, that uses SNMP to read signal strength values from wireless registration table and publish on web page. This example can be quickly transformed to read other values available for SNMP. To use scripts you need Mikrotik RouterOS, tested for version 2.9.xx (not yet for 3.0), PHP version 4 or 5, Web server (Apache, IIS). Configure Apache, and PHP only thing that needs attention is enabled snmp extension for PHP. In Windows in php.ini section Windows Extensions uncomment line
extension=php_snmp.dll .
Enable snmp on Mikrotik, and if needed, unblock UDP port 161. Copy scripts to WEB folder. Open index.php find line
$ip="hostname"; //Change IP to your host names, address
$mask_mac=false; //Use to mask MAC adress (true / false );
Replace hostname with IP address of Mikrotik, if you don’t want to see complete MAC address change false to true and now open the page in browser. You now see MAC address and signal strength. Page is auto refreshed every 10 seconds and reads values from SNMP.
The PHP code, to be saved as a .php file:
| MAC | Signal strenght(dBm) |
|---|---|
| Please check SNMP settings and IP address | |
NTH in RouterOS 3.x
In v3.0 it is a little different implementation of NTH. It has only two parameters 'every' and 'packet'.
How it works in v3.0
Every rule has its own counter. When rule receives packet counter for current rule is increased by one. If counter matches value of 'every' packet will be matched and counter will be set to zero.
If passthrough is not set then packets will be marked as follows:
- first rule nth=2,1 rule will match every first packet of 2, hence, 50% of all the traffic that is matched by the rules
- second rule if passthrough=no will match ONLY 25% of traffic because in 3.0 you need only one rule to catch traffic not like 2.9
Example
how it is possible to match 50% of all traffic only with one rule:
/ip firewall mangle
add action=mark-packet chain=prerouting new-packet-mark=AAA nth=2,1;
If more than one rule is needed, then there are two ways to match packets:
- first rule sees all packets and matches 1/3 of all, second rule sees 2/3 of packets and matches 1/2, third rule sees and matches all packets that passed through first two rules ( 1/3 of all packets ).
/ip firewall mangle
add action=mark-packet chain=prerouting new-packet-mark=AAA nth=3,1 passthrough=no;
add action=mark-packet chain=prerouting new-packet-mark=BBB nth=2,1 passthrough=no;
add action=mark-packet chain=prerouting new-packet-mark=CCC ;
- all rules can see all packets and each rule matches every 3-rd packet.
/ip firewall mangle
add action=mark-packet chain=prerouting new-packet-mark=AAA nth=3,1 passthrough=yes;
add action=mark-packet chain=prerouting new-packet-mark=BBB nth=3,2 passthrough=yes;
add action=mark-packet chain=prerouting new-packet-mark=CCC nth=3,3 passthrough=yes;
L7 security
layer7-protocol is a method of looking for patterns in connections.
First, add Regexp strings to the protocols menu, to define strings you will be looking for.
/ip firewall layer7-protocol add=
Then, use the defined protocols in firewall:
/ip firewall filter add layer7-protocol=
RouterOS will look for these strings in all connections passing the firewall rule where you use this. As this is resource intensive, make sure to filter out all good traffic before it hits this rule.
You can download a script with a list of common programs here (only for RouterOS v3 RC6). Pattern libraries can be found on the layer7 project page and on the protocol wiki.
Calea Mikrotik
CALEA features included in RouterOS
Multiple subject/multiple destination packet interception and streaming in following formats:
- Call Content Connection (CCC) Interface according to PKT-SP-ES-DCI-I01-060914 (PacketCable 2.0 PacketCable Electronic Surveillance Delivery Function to Collection Function Interface Specification)
- Call Content Connection (CCC) Interface according to ANSI/SCTE 24-13 2006 (IPCalblecom Electronic Surveillance Standard) that is approved method for Communication Content delivery to LEA according to ATIS-1000013.2007 (Lawfully Authorized Electronic Surveillance For Internet Access and Services)
- TZSP format - for reception with 'Ethereal', tcpdump, trafr (sniffer stream reader for linux) - http://www.mikrotik.com/download.html
CALEA-server package
- accepts multiple CCC streams (identified by destination port/source address/case id)
- stores communication content according to "IP Network Access Intercept Requirements and Method"(FBI-WISPA draft) specified "full content" intercept requirements (without out-of-band events)
- stores communication content of multiple subjects/cases
- stores communication content in libpcap format
- new libpcap file based on different conditions (interval/size/packet count)
- generates hash for each pcap file (md5/sha1/sha256)
Calea user
Calea provided options are available only for specific RouterOS user, as Calea server configuration as "tap" configuration. Specific user should have 'sniff' policy enabled at RouterOS user configuration,
/ user group set 0 policy=sniff
sniff policy is enabled by default for "full" and "write" user groups.
Intercepting Packet Flow
The IP Firewall and Interface Bridge now have one additional section,
- firewall section to intercept packets that are going trough firewall
/ ip firewall calea
- bridge section to intercept packets that are going trough bridge
/ interface bridge calea
Firewall and Bridge Calea menus contain same actions and matchers as "ip firewall filter" and "interface bridge filter", new avalailble actions:
- sniff - generates a tzsp stream that can be directed to any Wireshark (Ethereal) server
- sniff-pc - generates a Packet Cable stream that can be directed to a MikroTik RouterOS system with the calea package installed
By selecting either action, the following options will be available:
- sniff-id (Packet Cable protocol only) - packet stream case ID, that can be used to differentiate between separate traffic sets (e.g., between different users; or between client traffic and server traffic)
- sniff-target - IP address of the data retention server
- sniff-target-port - UDP port that the data retention server is listening on
Data Retention Server
The calea package provides an additional tool menu - /tool calea, that allows to save certain incoming data streams to a file. The server will create separate files for each packet stream (one data file and one hash file, if configured). The files will not grow indefinitely, but rather util a certain limit, after which a new set of files will be created for that stream. The limit is specified in size and extent of time, whichever is reached first.
Add a rule with the following properties:
- case-id - case ID set by the intercepting router
- case-name - case name is set on server to specify the folder, where intercepted data is stored
- intercept-ip - IP address of the intercepting router (IP address to receive the stream from)
- intercept-port - UDP port to listen on (port to receive the stream on)
- action - storage format (only pcap for now)
- pcap-file-stop-interval - maximal interval between creating new fileset, if size limit is not reached earlier
- pcap-file-stop-size - maximal filesize, in KiB
- pcap-file-stop-count - maximal packet count
- pcap-file-hash-method - hashing algorithm (md5, sha1 or sha256) for the data file (saved once the data file is completed and closed); no file is created if set to none
Calea Server/Client Configuration Example
let's assume the particular network configuration, we need to intercept data from 192.168.0.10 Wireless Client and send it to the Calea Server located on Local Network: 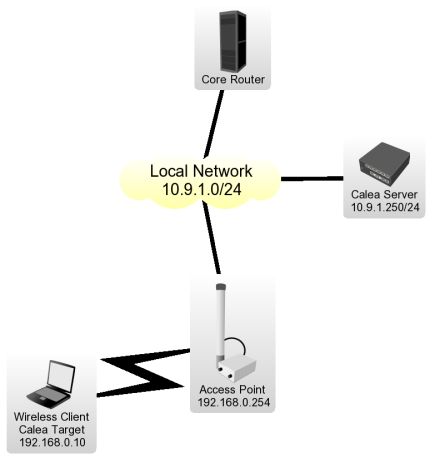
[edit] Client Configuration for the Intercept
Wireless Client is connected to Access Point, data interception has to be performed on Access Point for the particular network design.
- We have requirement to capture all data from the user Wireless Client with IP address of 192.168.0.10 We have to add two rules to make the interception,
/ ip firewall calea add action=sniff-pc chain=forward sniff-id=100 sniff-target=10.9.1.250 sniff-target-port=5555 src-address=192.168.0.10
/ ip firewall calea add action=sniff-pc chain=forward sniff-id=100 sniff-target=10.9.1.250 sniff-target-port=5555 dst-address=192.168.0.10
All traffic going trough the router for specified src/dst addresses is intercepted and sent to Calea Server (sniff-target) with sniff-id=100
- Calea package is not required for intercepting host.
Calea Server Configuration
- Calea package is required for server.
- One rule is required to accept the data from the Access Point to receive all intercepted traffic from the Access Point,
/ tool calea add action=pcap intercept-port=5555 case-id=100 intercept-ip=192.168.0.254
Intercept-port and case-id should be equal on server and client side, intercept-ip is IP address of the intercepting router (Access Point).
- Calea server received information is available under 'file' menu.
Bruteforce login prevention
These are 2 basic scripts I use frequently that are from the forum (written by other users)
Allows only 10 FTP login incorrect answers per minute
in /ip firewall filter
add chain=input protocol=tcp dst-port=21 src-address-list=ftp_blacklist action=drop
add chain=output action=accept protocol=tcp content="530 Login incorrect" dst-limit=1/1m,9,dst-address/1m
add chain=output action=add-dst-to-address-list protocol=tcp content="530 Login incorrect" \
address-list=ftp_blacklist address-list-timeout=3h
This will prevent a SSH brute forcer to be banned for 10 days after repetitive attempts. Change the timeouts as necessary.
in /ip firewall filter
add chain=input protocol=tcp dst-port=22 src-address-list=ssh_blacklist action=drop \
comment="drop ssh brute forcers" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage3 action=add-src-to-address-list address-list=ssh_blacklist \
address-list-timeout=10d comment="" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new \
src-address-list=ssh_stage2 action=add-src-to-address-list address-list=ssh_stage3 \
address-list-timeout=1m comment="" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage1 \
action=add-src-to-address-list address-list=ssh_stage2 address-list-timeout=1m comment="" disabled=no
add chain=input protocol=tcp dst-port=22 connection-state=new action=add-src-to-address-list \
address-list=ssh_stage1 address-list-timeout=1m comment="" disabled=no
How to Block Websites
This example will explain you “How to Block Web Sites” & “How to Stop Downloading”. I have use Web-Proxy test Package.
First, Configure Proxy.
/ip proxy
enabled: yes
src-address: 0.0.0.0
port: 8080
parent-proxy: 0.0.0.0:0
cache-drive: system
cache-administrator: "ASHISH PATEL"
max-disk-cache-size: none
max-ram-cache-size: none
cache-only-on-disk: no
maximal-client-connections: 1000
maximal-server-connections: 1000
max-object-size: 512KiB
max-fresh-time: 3d
Now, Make it Transparent
/ip firewall nat
chain=dstnat protocol=tcp dst-port=80 action=redirect to-ports=8080
Make sure that your proxy is NOT a Open Proxy
/ip firewall filter
chain=input in-interface=src-address=0.0.0.0/0 protocol=tcp dst-port=8080 action=drop
Now for Blocking Websites
/ip proxy access
dst-host=www.vansol27.com action=deny
It will block website http://www.vansol27.com/, We can always block the same for different networks by giving src-address. It will block for particular source address.
We can also stop downloading files like.mp3, .exe, .dat, .avi,…etc.
/ip proxy access
path=*.exe action=deny
path=*.mp3 action=deny
path=*.zip action=deny
path=*.rar action=deny.
Try with this also
/ip proxy access
dst-host=:mail action=deny
This will block all the websites contain word “mail” in url.
Example: It will block www.hotmail.com, mail.yahoo.com, www.rediffmail.com
Forwarding a port to an internal IP
This will go on a 2.9.x mikrotik where you want to forward a port (tcp 5900) to an internal IP. 69.69.69.69 is the example wan IP, 192.168.1.101 is the desired internal destination.
/ip firewall nat add chain=dstnat dst-address=69.69.69.69 protocol=tcp dst-port=5900 \
action=dst-nat to-addresses=192.168.1.101 to-ports=5900
Nth On Mikrotik
example: nth=Every,Counter,Packet nth=2,3,0. 2,3,1 2,3,2
divide all packets into groups of three (2+1). The packets will be numbered from 0 to 2. So, a sequence of packets the rule matches looks like: (0 1 2)(0 1 2)(0 1 2)(0 1 2)(0 1 2)...
the first rule will match the first packet in each group ("Packet"=0). The second rule will match the second packet in each group ("Packet"=1) and so on. Each successful match increments the counter. When a value of "Every" is reached, the counter is reset to 0. For this to work, the "Counter" should be the same for all rules (you can pick any value from 0 to 15, IIRC).
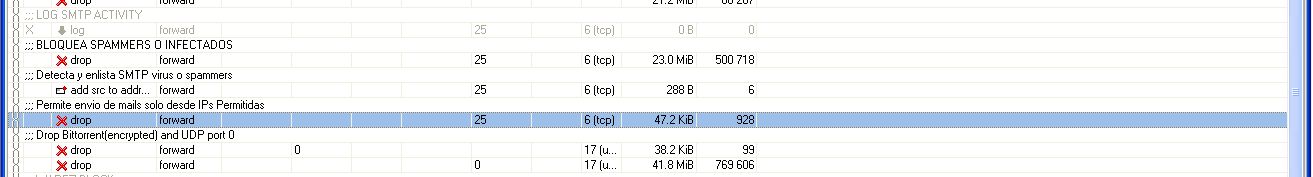
How to autodetect infected or spammer users and temporary block the SMTP output
Here can see in the solution which i invented and work excellent to autodetect and block SMTP viruses or spammers!
Only create these 2 rules in firewall forward:
/ip firewall filter
add chain=forward protocol=tcp dst-port=25 src-address-list=spammer
action=drop comment="BLOCK SPAMMERS OR INFECTED USERS"
add chain=forward protocol=tcp dst-port=25 connection-limit=30,32 limit=50,5 action=add-src-to-address-list
address-list=spammer address-list-timeout=1d comment="Detect and add-list SMTP virus or spammers"
When an infected user is autodetected with a virus worm or doing spam, the user is added to a spammer list and block the STMP outgoing by 1 day, all the values can be adjusted for different networks types or at your convenience
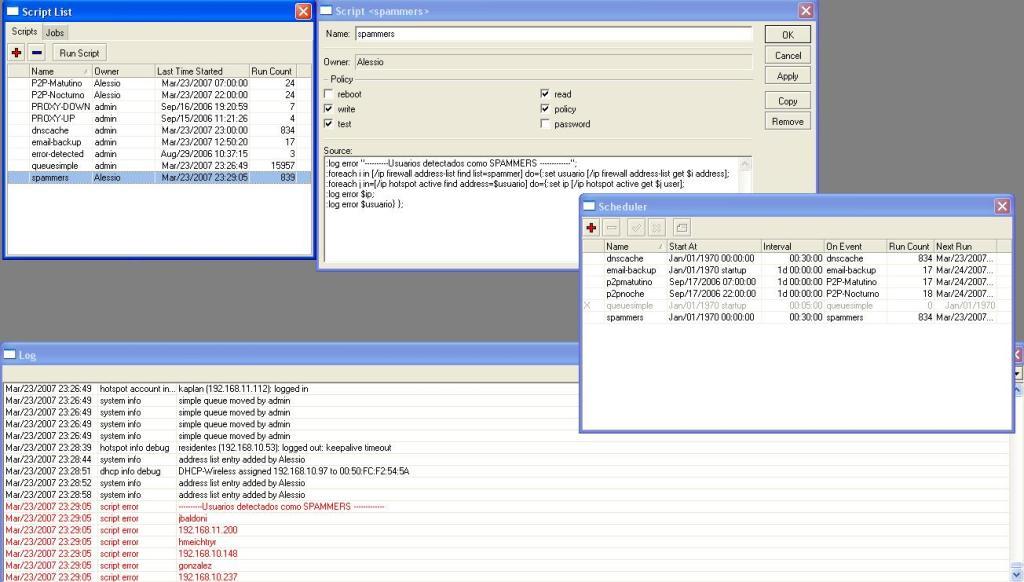
[edit] Logging detected users
Next, to display a red Log each 30 minutes listing the detected infected or spammers users using hotspot, add the next script:
/system script
add name="spammers" source=":log error \"----------Users detected like \
SPAMMERS -------------\";
\n:foreach i in \[/ip firewall address-list find \
list=spammer\] do={:set usser \[/ip firewall address-list get \$i \
address\];
\n:foreach j in=\[/ip hotspot active find address=\$usser\] \
do={:set ip \[/ip hotspot active get \$j user\];
\n:log error \$ip;
\n:log \
error \$usser} };" policy=ftp,read,write,policy,test,winbox
Dmitry on firewalling
Components of the filter
- protocol classifier
- invalid packet filter
- port-scan detector
- policy classifier
- application protocol filter
- TCP-specific filters
- application protocol specific filters
Introduction
There are two interfaces on our router: Local (for connecting internal network) and Public (connected to the Internet)
Protocol classifier
/ ip firewall mangle
add chain=prerouting protocol=tcp connection-state=new action=jump jump-target=tcp-services
add chain=prerouting protocol=udp connection-state=new action=jump jump-target=udp-services
add chain=prerouting connection-state=new action=jump jump-target=other-services
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=20-21 action=mark-connection new-connection-mark=ftp passthrough=no
add chain=tcp-services protocol=tcp src-port=513-65535 dst-port=22 action=mark-connection new-connection-mark=ssh passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=23 action=mark-connection new-connection-mark=telnet passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=25 action=mark-connection new-connection-mark=smtp passthrough=no
add chain=tcp-services protocol=tcp src-port=53 dst-port=53 action=mark-connection new-connection-mark=dns passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=53 action=mark-connection new-connection-mark=dns passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=80 action=mark-connection new-connection-mark=http passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=110 action=mark-connection new-connection-mark=pop3 passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=113 action=mark-connection new-connection-mark=auth passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=119 action=mark-connection new-connection-mark=nntp passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=143 action=mark-connection new-connection-mark=imap passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=161-162 action=mark-connection new-connection-mark=snmp passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=443 action=mark-connection new-connection-mark=https passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=465 action=mark-connection new-connection-mark=smtps passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=993 action=mark-connection new-connection-mark=imaps passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=995 action=mark-connection new-connection-mark=pop3s passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=1723 action=mark-connection new-connection-mark=pptp passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=2379 action=mark-connection new-connection-mark=kgs passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=3128 action=mark-connection new-connection-mark=proxy passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=3389 action=mark-connection new-connection-mark=win-ts passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=4242-4243 action=mark-connection new-connection-mark=emule passthrough=no
add chain=tcp-services protocol=tcp src-port=4661-4662 dst-port=1024-65535 action=mark-connection new-connection-mark=overnet passthrough=no
add chain=tcp-services protocol=tcp src-port=4711 dst-port=1024-65535 action=mark-connection new-connection-mark=emule passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=5900-5901 action=mark-connection new-connection-mark=vnc passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=6667-6669 action=mark-connection new-connection-mark=irc passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=6881-6889 action=mark-connection new-connection-mark=bittorrent passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=8080 action=mark-connection new-connection-mark=http passthrough=no
add chain=tcp-services protocol=tcp src-port=1024-65535 dst-port=8291 action=mark-connection new-connection-mark=winbox passthrough=no
add chain=tcp-services protocol=tcp action=mark-connection new-connection-mark=other-tcp passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=53 action=mark-connection new-connection-mark=dns passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=123 action=mark-connection new-connection-mark=ntp passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=1701 action=mark-connection new-connection-mark=l2tp passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=4665 action=mark-connection new-connection-mark=emule passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=4672 action=mark-connection new-connection-mark=emule passthrough=no
add chain=udp-services protocol=udp src-port=4672 dst-port=1024-65535 action=mark-connection new-connection-mark=emule passthrough=no
add chain=udp-services protocol=udp src-port=1024-65535 dst-port=12053 action=mark-connection new-connection-mark=overnet passthrough=no
add chain=udp-services protocol=udp src-port=12053 dst-port=1024-65535 action=mark-connection new-connection-mark=overnet passthrough=no
add chain=udp-services protocol=udp src-port=36725 dst-port=1024-65535 action=mark-connection new-connection-mark=skype passthrough=no
add chain=udp-services protocol=udp connection-state=new action=mark-connection new-connection-mark=other-udp passthrough=no
add chain=other-services protocol=icmp icmp-options=8:0-255 action=mark-connection new-connection-mark=ping passthrough=no
add chain=other-services protocol=gre action=mark-connection new-connection-mark=gre passthrough=no
add chain=other-services action=mark-connection new-connection-mark=other passthrough=no
Note that for TCP and UDP, we check both, source port (usually, 1024-65535) and destination port. Everything else is not a valid protocol.
Sanity-check
Most generic invalid packet and port-scan detection techniques
Place this before all other rules in mangle:
/ip firewall mangle
add chain=prerouting in-interface=Public dst-address-list=nat-addr action=mark-packet new-packet-mark=nat-traversal passthrough=no
Note that just like in the line above, some filter rules rely on address lists. here is a simple list, which you should extend further:
/ ip firewall address-list
add list=illegal-addr address=0.0.0.0/8 comment="illegal addresses"
add list=illegal-addr address=127.0.0.0/8
add list=illegal-addr address=224.0.0.0/3
add list=illegal-addr address=10.0.0.0/8
add list=illegal-addr address=172.16.0.0/12
add list=illegal-addr address=192.168.0.0/16
add list=local-addr address=172.31.255.0/29 comment="my local network"
add list=nat-addr address=172.31.255.0/29 comment="my local network"
So, there are three address lists:
- illegal-addr - the list, which could be extended to some few tens of addresses at least to include the bogon IPs, which are not registered with IANA and some more, this short list given in examples is just a short sample;
- local-addr - the list to include all addresses located in your network, behind this firewall
- nat-addr - should contain all the IP addresses you are source-natting on your router
In this example we exclude traffic between the local clients connected to different ports of the Local interface (which is a bridge between ethernet and wireless networks):
/ ip firewall filter
add chain=forward in-interface=Local out-interface=Local action=accept comment="Allow traffic between wired and wireless networks"
Then we are filtering everything else to the drop chain of the firewall. The separate chain is created to keep all logging and accounting in one place.
/ ip firewall filter
add chain=forward action=jump jump-target=sanity-check comment="Sanity Check"
add chain=sanity-check packet-mark=nat-traversal action=jump jump-target=drop comment="Deny illegal NAT traversal"
add chain=sanity-check protocol=tcp psd=20,3s,3,1 action=add-src-to-address-list address-list=blocked-addr address-list-timeout=1d comment="Block port scans"
add chain=sanity-check protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack action=add-src-to-address-list address-list=blocked-addr address-list-timeout=1d comment="Block TCP Null scan"
add chain=sanity-check protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list=blocked-addr address-list-timeout=1d comment="Block TCP Xmas scan"
add chain=sanity-check protocol=tcp src-address-list=blocked-addr action=jump jump-target=drop
add chain=sanity-check protocol=tcp tcp-flags=rst action=jump jump-target=drop comment="Drop TCP RST"
add chain=sanity-check protocol=tcp tcp-flags=fin,syn action=jump jump-target=drop comment="Drop TCP SYN+FIN"
add chain=sanity-check connection-state=invalid action=jump jump-target=drop comment="Dropping invalid connections at once"
add chain=sanity-check connection-state=established action=accept comment="Accepting already established connections"
add chain=sanity-check connection-state=related action=accept comment="Also accepting related connections"
add chain=sanity-check dst-address-type=broadcast,multicast action=jump jump-target=drop comment="Drop all traffic that goes to multicast or broadcast addresses"
add chain=sanity-check in-interface=Local dst-address-list=illegal-addr dst-address-type=!local action=jump jump-target=drop comment="Drop illegal destination addresses"
add chain=sanity-check in-interface=Local src-address-list=!local-addr action=jump jump-target=drop comment="Drop everything that goes from local interface but not from local address"
add chain=sanity-check in-interface=Public src-address-list=illegal-addr action=jump jump-target=drop comment="Drop illegal source addresses"
add chain=sanity-check in-interface=Public dst-address-list=!local-addr action=jump jump-target=drop comment="Drop everything that goes from public interface but not to local address"
add chain=sanity-check src-address-type=broadcast,multicast action=jump jump-target=drop comment="Drop all traffic that goes from multicast or broadcast addresses"
[edit] Application-specific filters
/ ip firewall filter
add chain=forward protocol=tcp action=jump jump-target=restrict-tcp
add chain=forward protocol=udp action=jump jump-target=restrict-udp
add chain=forward action=jump jump-target=restrict-ip
add chain=restrict-tcp connection-mark=auth action=reject
add chain=restrict-tcp connection-mark=smtp action=jump jump-target=smtp-first-drop comment="anti-spam policy"
add chain=smtp-first-drop src-address-list=first-smtp action=add-src-to-address-list address-list=approved-smtp
add chain=smtp-first-drop src-address-list=approved-smtp action=return
add chain=smtp-first-drop action=add-src-to-address-list address-list=first-smtp
add chain=smtp-first-drop action=reject reject-with=icmp-network-unreachable
Restricting services
/ ip firewall filter
add chain=restrict-tcp connection-mark=other-tcp action=jump jump-target=drop
add chain=restrict-udp connection-mark=other-udp action=jump jump-target=drop
add chain=restrict-ip connection-mark=other action=jump jump-target=drop
Protecting the router
/ ip firewall filter
add chain=input src-address-type=local dst-address-type=local action=accept comment="Allow local traffic \(between router applications\)"
add chain=input in-interface=Local protocol=udp src-port=68 dst-port=67 action=jump jump-target=dhcp comment="DHCP protocol would not pass sanity checking, so enabling it explicitly before other checks"
add chain=input action=jump jump-target=sanity-check comment="Sanity Check"
add chain=input dst-address-type=!local action=jump jump-target=drop comment="Dropping packets not destined to the router itself, including all broadcast traffic"
add chain=input connection-mark=ping limit=5,5 action=accept comment="Allow pings, but at a very limited rate \(5 per sec\)"
add chain=input in-interface=Local action=jump jump-target=local-services comment="Allowing some services to be accessible from the local network"
add chain=input in-interface=Public action=jump jump-target=public-services comment="Allowing some services to be accessible from the Internet"
add chain=input action=jump jump-target=drop
add chain=dhcp src-address=0.0.0.0 dst-address=255.255.255.255 action=accept
add chain=dhcp src-address=0.0.0.0 dst-address-type=local action=accept
add chain=dhcp src-address-list=local-addr dst-address-type=local action=accept
add chain=local-services connection-mark=ssh action=accept comment="SSH \(22/TCP\)"
add chain=local-services connection-mark=dns action=accept comment="DNS"
add chain=local-services connection-mark=proxy action=accept comment="HTTP Proxy \(3128/TCP\)"
add chain=local-services connection-mark=winbox comment="Winbox \(8291/TCP\)" disabled=no
add chain=local-services action=drop comment="Drop Other Local Services"
add chain=public-services connection-mark=ssh action=accept comment="SSH \(22/TCP\)"
add chain=public-services connection-mark=pptp action=accept comment="PPTP \(1723/TCP\)"
add chain=public-services connection-mark=gre action=accept comment="GRE for PPTP"
add chain=public-services action=drop comment="Drop Other Public Services"
- The "accept ping" rule needs to come before the "public" and "local" jump rules otherwise that rules will never be executed and ICMP will continue to be dropped.
Proxying everything
/ ip firewall nat
add chain=dstnat in-interface=Local connection-mark=dns action=redirect comment="proxy for DNS requests"
add chain=dstnat in-interface=Local connection-mark=http protocol=tcp action=redirect to-ports=3128 comment="proxy for HTTP requests"
add chain=dstnat in-interface=Local connection-mark=ntp action=redirect comment="proxy for NTP requests"
Enable Proxy servers
/ system ntp server
set enabled=yes broadcast=no multicast=no manycast=no
/ system ntp client
set enabled=yes mode=unicast primary-ntp=xxx.xxx.xxx.xxx secondary-ntp=0.0.0.0
/ ip proxy
set enabled=yes port=3128 parent-proxy=0.0.0.0:1 maximal-client-connections=1000 maximal-server-connections=1000
/ ip dns
set primary-dns=yyy.yyy.yyy.yyy secondary-dns=0.0.0.0 allow-remote-requests=yes cache-size=2048KiB cache-max-ttl=1w
Please change:
- xxx.xxx.xxx.xxx to the NTP server you choose
- yyy.yyy.yyy.yyy to your ISP's DNS server ip
Redirect mail traffic to a specified server
This is if you want to redirect all traffic through your router to your own specified mail server. This is usefull if you have many clients from different locations connecting to your network at different times. (Note that if you are using Hotspot you can do this in the Hotspot settings instead)
ip firewall nat add chain=dstnat protocol=tcp dst-port=25 action=dst-nat to-addresses=10.0.0.1 to-ports=25
This will redirect all smtp (port 25) traffic out the router to ip address 10.0.0.1
How to Block Customer
How to Block a Customer and Tell him to Pay the Bill
Sometimes you may need to cut off a customer and tell him to pay his bill. It's best done by redirecting his http requests to a page with information telling to pay in order to get reconnected. You can do it with a simple destination NAT rule that captures all http requests from a specific address and sends them to a server with webpage telling to pay the bill. However, it's quite easy to make this using the HotSpot feature of RouterOS. Please note that this don't work with PPPoE connections.
To make this setup, you should have Hotspot package enabled on the RouterOS. This example will cover how to block customer's computer. When he tries to open a webpage he would be redirected to the hotspot page which will contain info that he hasn't paid the bill for the Internet access. Your router should have already been configured and working (customer should have access to the Internet), you should have the DNS server specified in the router.
First you should edit the Hotspot login.html page with the text that contains information that will be shown to the customers who haven't paid their bills. It could be something like this: "Service not available, please pay the bill and contact us by phone to get reconnected
Next, add an ip-binding rule that will allow all customers to bypass the hotspot page. It is done using such a command:
/ip hotspot ip-binding add type=bypassed address=0.0.0.0/0 \
comment="bypass the hotspot for all the paying customers"
After that add the Hotspot server on the interface where your clients are connected. It can be done using such command:
/ip hotspot add interface=local disabled=no
Now you can add ip-binding rules for the customers that haven't paid their bill. You can match them by IP address or MAC address. Here is an example using MAC address:
/ip hotspot ip-binding add mac-address=00:0C:42:00:00:90 type=regular comment "Non paying client 1"
Now we have such configuration:
[admin@MikroTik] ip hotspot ip-binding> print
Flags: X - disabled, P - bypassed, B - blocked
# MAC-ADDRESS ADDRESS TO-ADDRESS SERVER
0 P ;;; bypass the hotspot for all the paying customers
0.0.0.0/0
1 ;;; Non paying client 1
00:0C:42:00:00:90
There is one more step to make it work, you should change the order of these rules, the first rule should be above the bypass rule so it could be processed. You can move it using move command:
[admin@MikroTik] ip hotspot ip-binding> move 1 0
Now the ip-binding configuration should look like this:
[admin@MikroTik] ip hotspot ip-binding> print
Flags: X - disabled, P - bypassed, B - blocked
# MAC-ADDRESS ADDRESS TO-ADDRESS SERVER
0 ;;; Non paying client 1
00:0C:42:00:00:90
1 P ;;; bypass the hotspot for all the paying customers
0.0.0.0/0
If the customers can pay their bill using internet you can modify the login.html by adding some links to clients bank web-page where they can pay their bill. After you add these links in the login page you should also add them in the hotspot configuration so the blocked customer could access that page. This can be done in the 'ip hotspot walled-garden ip' menu. Here is an example:
/ip hotspot walled-garden ip add dst-host=www.paypal.com
How to secure a network using ARP
Although hosts in IP network are addressed using IP addresses, hardware addresses must be used to actually transport data from one host to another at Layer-2 (EG: Ethernet). Address Resolution Protocol (ARP) provides a mapping between the two different forms of addresses. A router has an ARP table that contains ARP entries. ARP entries consist of IP addresses and corresponding hardware addresses (such as a MAC address). Normally ARP provides a dynamic mapping from an IP address to corresponding hardware address by adding ARP entries automatically as they are discovered, but to increase network security static ARP entries can be created manually. By allowing a router to reply only to those static ARP entries found in the ARP table we restrict access to the router and to the network behind the router to only those IP/Hardware address combinations found in the ARP table. To make a router use only static ARP entries follow the steps listed below:
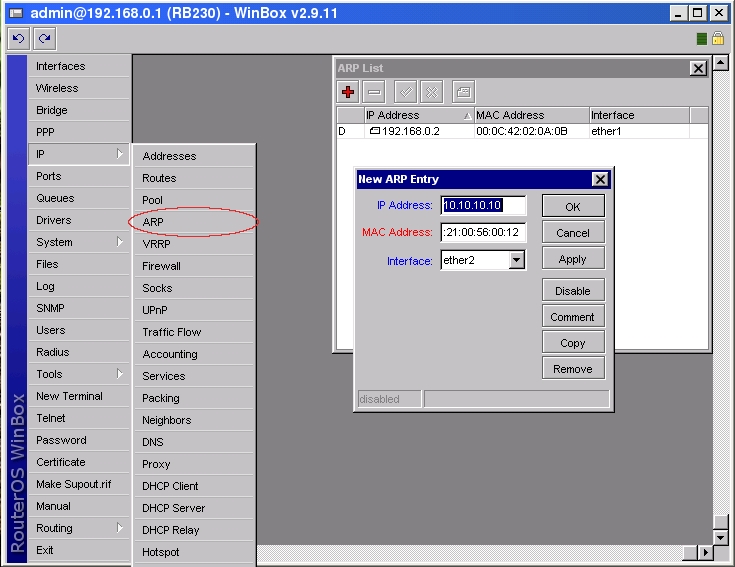
1. Add ARP entries of hosts you want to accept in WinBox
or in Console
[admin@RB230] ip arp> add address=10.10.10.10 interface=ether2 mac-address=06 \
\... 00:21:00:56:00:12
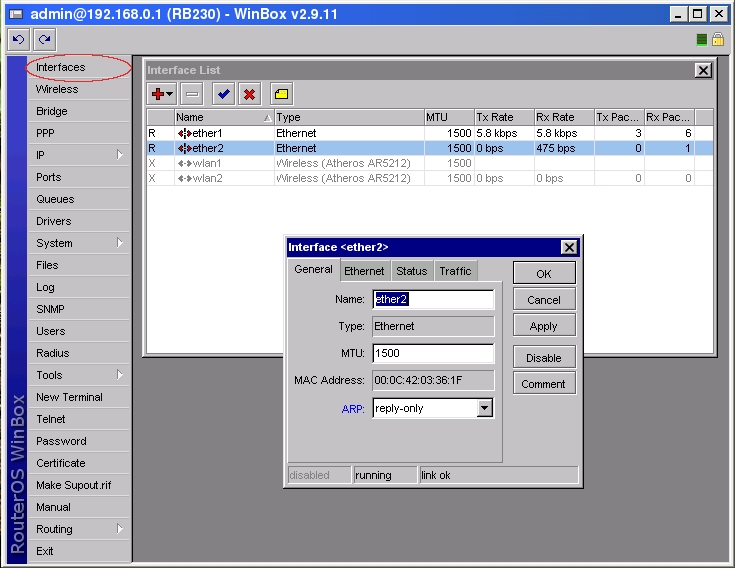
2. Make ether2 interface only reply to ARP requests using your specified ARP entries in WinBox
or in Console
[admin@RB230] > interface ethernet set ether2 arp=reply-only
Drop port scanners
To protect the Router from port scanners, we can record the IPs of hackers who try to scan your box. Using this address list we can drop connection from those IP
in /ip firewall filter
add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="Port scanners to list " disabled=no
Various combinations of TCP flags can also indicate port scanner activity.
add chain=input protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="NMAP FIN Stealth scan"
add chain=input protocol=tcp tcp-flags=fin,syn
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="SYN/FIN scan"
add chain=input protocol=tcp tcp-flags=syn,rst
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="SYN/RST scan"
add chain=input protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="FIN/PSH/URG scan"
add chain=input protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="ALL/ALL scan"
add chain=input protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="NMAP NULL scan"
Then you can drop those IPs:
add chain=input src-address-list="port scanners" action=drop comment="dropping port scanners" disabled=no
Similarly, you can drop these port scanners in the forward chain, but using the above rules with "chain=forward".
Protecting your customers
To protect the customer's network, we should check all traffic which goes through router and block unwanted. For icmp, tcp, udp traffic we will create chains, where all unwanted packets will be dropped. For the beginning, we can copy and paste the following commands into RouterOS terminal console:
/ip firewall filter
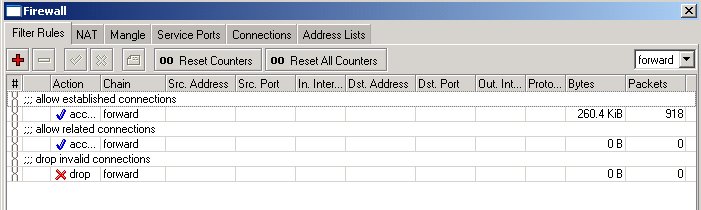
add chain=forward connection-state=established comment="allow established connections"
add chain=forward connection-state=related comment="allow related connections"
add chain=forward connection-state=invalid action=drop comment="drop invalid connections"
Here, the first two rules deal with packets of already opened or related connections. We assume that those are okay. We do not like invalid connection packets, therefore they are dropped.
Next, we should filter out and drop all unwanted packets that look like coming from virus infected hosts. Instead of adding those rules to the forward chain, we create a new chain for all unwanted netbios and similar traffic. We can give the chain a descriptive name, say, "virus" when adding the following rules to the ip firewall filter (you can copy and paste these rules into the terminal window, if you are in the /ip firewall filter menu):
add chain=virus protocol=tcp dst-port=135-139 action=drop comment="Drop Blaster Worm"
add chain=virus protocol=udp dst-port=135-139 action=drop comment="Drop Messenger Worm"
add chain=virus protocol=tcp dst-port=445 action=drop comment="Drop Blaster Worm"
add chain=virus protocol=udp dst-port=445 action=drop comment="Drop Blaster Worm"
add chain=virus protocol=tcp dst-port=593 action=drop comment="________"
add chain=virus protocol=tcp dst-port=1024-1030 action=drop comment="________"
add chain=virus protocol=tcp dst-port=1080 action=drop comment="Drop MyDoom"
add chain=virus protocol=tcp dst-port=1214 action=drop comment="________"
add chain=virus protocol=tcp dst-port=1363 action=drop comment="ndm requester"
add chain=virus protocol=tcp dst-port=1364 action=drop comment="ndm server"
add chain=virus protocol=tcp dst-port=1368 action=drop comment="screen cast"
add chain=virus protocol=tcp dst-port=1373 action=drop comment="hromgrafx"
add chain=virus protocol=tcp dst-port=1377 action=drop comment="cichlid"
add chain=virus protocol=tcp dst-port=1433-1434 action=drop comment="Worm"
add chain=virus protocol=tcp dst-port=2745 action=drop comment="Bagle Virus"
add chain=virus protocol=tcp dst-port=2283 action=drop comment="Drop Dumaru.Y"
add chain=virus protocol=tcp dst-port=2535 action=drop comment="Drop Beagle"
add chain=virus protocol=tcp dst-port=2745 action=drop comment="Drop Beagle.C-K"
add chain=virus protocol=tcp dst-port=3127-3128 action=drop comment="Drop MyDoom"
add chain=virus protocol=tcp dst-port=3410 action=drop comment="Drop Backdoor OptixPro"
add chain=virus protocol=tcp dst-port=4444 action=drop comment="Worm"
add chain=virus protocol=udp dst-port=4444 action=drop comment="Worm"
add chain=virus protocol=tcp dst-port=5554 action=drop comment="Drop Sasser"
add chain=virus protocol=tcp dst-port=8866 action=drop comment="Drop Beagle.B"
add chain=virus protocol=tcp dst-port=9898 action=drop comment="Drop Dabber.A-B"
add chain=virus protocol=tcp dst-port=10000 action=drop comment="Drop Dumaru.Y"
add chain=virus protocol=tcp dst-port=10080 action=drop comment="Drop MyDoom.B"
add chain=virus protocol=tcp dst-port=12345 action=drop comment="Drop NetBus"
add chain=virus protocol=tcp dst-port=17300 action=drop comment="Drop Kuang2"
add chain=virus protocol=tcp dst-port=27374 action=drop comment="Drop SubSeven"
add chain=virus protocol=tcp dst-port=65506 action=drop comment="Drop PhatBot, Agobot, Gaobot"
Here, we list all those well known "bad" protocols and ports, used by various trojans and viruses when they take over your computer. This list is incomplete; we should add more rules to it! We can jump to this list from the forward chain by using a rule with action=jump:
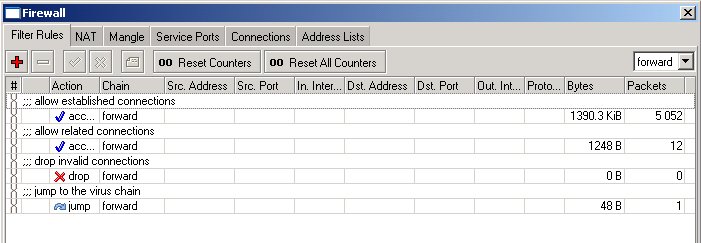
add chain=forward action=jump jump-target=virus comment="jump to the virus chain"
The forward chain looks now as follows:
If the packet does not match any of the rules in the virus chain, the processing is returned back to the forward chain. We can simply add rules allowing udp and ping, and then drop everything else (if there are no services on customer's network that need to be accessed from outside):
add chain=forward protocol=icmp comment="allow ping"
add chain=forward protocol=udp comment="allow udp"
add chain=forward action=drop comment="drop everything else"
Securing New RouterOs Router
Securing A Fresh v2.9 RouterOs Device
This document is designed for RouterOs devices that have been cleanly loaded and don’t have any configuration, the configuration outlined in this guide may work for routers already configured but caution must be taken that this configuration does not affect the device.
Please read and understand the entire document before applying this to a device, failure to do so may result in you being unable to access the device
The purpose of this document is to take users though the steps needed to secure access to a RouterOs device while maintaining the ability for other devices to communicate and use certain services. This document works on the idea of 'just-enough' access, that is services or people who need to access the router have 'just-enough' privileges on the router to do their job - and no more. There is no reason for another router that only access's BGP on the device to have full access and likewise a user that log's in to monitor wireless connections should have any write access or the ability to reboot/shutdown etc etc. With this in mind you should look at other areas of your network and asses how they are setup/configured - they may need attention in order to fully secure your network as a whole.
The user's going to pick dancing pigs over security every time. — Bruce Schneier
This is VERY true, the end user and even some sys admin’s I know will choose no security if it means they don’t have to think, some of the things we will put in place on the device will require people using or connecting to the router to do some thing differently, on top of this if a router connecting to the device wants to use a new service on the router you may have enable access.
This can be a pain and sometimes it can go too far, it’s your job to figure out where the balance of security vs. usability is, make it too difficult to do anything and your users won’t will give up, make it too easy to do something and you will be compromised. This may be starting to sound a bit much or too difficult but that’s because we aren’t talking about securing RouterOs now, we are talking about whole network security – security that neither starts nor stops with securing a router.
Having said that lets get into the nuts & bolts of securing RouterOs
Configuring Packages & Hardening Services
Some of you may have started this guide having just loaded RouterOs onto the device which is fine but my personal taste when it comes to packages on RouterOs is to use the roueros-x86/rb500.npk file, why? Because I find it easier to upgrade the router with a single file and its easier when it comes to enabling new services if the router’s role is expanded. There is nothing worse than needing to add a service (I.e. DHCP-Server) to a router running an old RouterOs version and finding you don’t have dhcp-2.9.xx.npk, this is more a problem now that Mikrotik don’t allow you to download old versions from their website anymore.
Installing a new router with routeros-xxx.npk is best done via net-install, if you need to install via CD then your only option is to install from an old version, only install the system package and then upload routeros-xxx.npk via mac-winbox. It’s messy but it’s the only way I have found to do a clean load via CD with the single npk. Once again this is comes down to personal preference and is not required in this document
I always install a router with the following packages enable as a minimum:
- Advanced-Tools
- Ntp
- Security
- System
This installs a basic system where you are able to keep the clock in sync with a external source, a suite of tools enabling advanced monitoring and reporting and allows you to talk to the router securely.
You need to think about the exact role the router will have before you start enabling more packages on the router, if it’s a simple wireless relay station then why would it need DHCP enabled? If the router is to be a Ethernet based firewall then why does it need the wireless enabled. Only enable packages the router need to do its job, remember its all about ‘just-enough’ security
Once you have your router loaded up with only the packages it need’s its time to look at the services that are running by default.
By default you can access the router by:
- Telnet
- SSH
- HTTP
- Winbox
- FTP
- Mac-Telnet
Later in the document we will be adding a firewall to control access to the above services but right now you may choose that some services you just wont use ever, on my routers I choose disable all services but Mac-Telnet, Winbox and SSH. All other services I have no need for and disable them. Disabling a service is easy
/ip services print
Will return this on a default load of routeros
Flags: X - disabled, I - invalid
# NAME PORT ADDRESS CERTIFICATE
0 telnet 23 0.0.0.0/0
1 ftp 21 0.0.0.0/0
2 www 80 0.0.0.0/0
3 ssh 22 0.0.0.0/0
4 X www-ssl 443 0.0.0.0/0 none
To disable a service is simple
/ip service disable
Once you have configured the services to your liking it's time to look at other ways to interface with the router, first up is SNMP which is used by a lot of programs to monitor devices (I.e. The Dude)
SNMP is disabled by default and if you have other means of monitoring devices it is safe to leave disabled. I prefer to use The Dude to monitor my network so I will go ahead and enable access and set some helpful fields
/snmp set enabled=yes location=”The Matrix” contact=neo@zion.org
SNMP in RouterOs 2.9 is read only, so the only danger from enabling access to it is that without firewalling to stop access anyone on your network or the rest of the world if the router has a public IP address will be able to look at Wireless signal levels etc.
Now that your router has some basic hardening its time to look at user’s who access the router and the privileges that they have
Users & Passwords
By default your router has 1 user, admin, which has no password set. With RouterOs if you set password for the admin user, add no other users with write/password privileges and forget the password there is ‘’’’’NO’’’’’ way to log in or recover the password, you must do a reinstall.
Before going any further you should check to see if the company you are working has a policy on user’s and passwords.
If your company does have a policy on this you must check to see if this document conflicts with it
If it does seek approval before implementing this document any further
The first thing we will do is give the default admin a password. In my network all user passwords are 32 characters long, I use a password generator here which will create 10 passwords at a time, if you need more just hit refresh and it generate more passwords
/user set admin password=putpasshere
Once you do this its best to exit and reconnect Winbox.
Next up is adding a fail-safe user, this is a user with admin rights and a simple password that is ‘’’’’only’’’’’ allowed to connect from the local terminal. The purpose of this is to prevent you from have to reinstall the router in the event you lose the admin password. I use a simple password such as my driver license number of IRD number as the password, it’s critical that the password is not something you will forget or lose. In my country your drivers license and IRD number are set for life and make for perfect backup user passwords.
In reality I don’t use my driver license or IRD number, I use another document that is just as easy to remember, don’t use something that is easy to get a hold of. If you lose your wallet the last you want to be doing is changing all your router’s passwords.
So lets add this user
/user add name=badmin password=putpasshere group=full address=127.0.0.1/32
At this point your router is password protected and has a fail-safe in case you lose the big password. You may need to add more users for monitoring etc, don’t hand out the admin password to everyone. If someone needs access to the router determine what privileges they need and create a user for them. The rest of this document is useless to you if you don’t keep the usernames and password secure
‘’Amateurs hack systems, professionals hack people.’’ — ‘’’Bruce Schneier’’’
[edit] Port Knocking
In the firewall we will load onto the router in the next section we divide up access into 2 sections
- An address list of devices that have full access to the router
- All other devices that have limited access to the router
One thing that all other devices are limited to is they have no Winbox/SSH/telnet access to the router, which sometimes will mean you can't get into it. One way to temporarily allow full access to a router is port knocking.
Port knocking with RouterOs is a way of adding a dynamic IP address into an address list for a specified amount of time. The way it works is like this
- Client sends packet to router on port 1337
- Router adds client’s IP address to address list “temp” with a timeout of 15 seconds
- Client sends packer to router on port 7331
- Router checks to see if the client’s IP address is on address list “temp”
- If it is then router adds IP address to address list “safe” with a timeout of 15 minutes
- Client has full access to router for 15 minutes
This feature is completely customisable with you able to define how many ports the client has to ‘knock’ before its given access, you can define what port numbers and what protocols you must knock and the timeout values.
A windows knocking client is available here and is used like so
Knock.exeport:protocol port:protocol port:protocol…
So to gain access to the router in the example above we would run
Knock.exe 192.168.0.2 1337:tcp 7331:tcp
While this feature is useful it is another weak point in security, in the firewall rules I show which rules are used to create a port knock, if you leave these rules out there will be no port knocking on the router
Loading A Firewall
Next up is loading up a firewall, right now you router is secure from access by passwords, but passwords are one layer of security – not the only layer. This script is based on the firewall used on the MT demo router but has a few changes to it, it only protects the router and contains no ‘forward’ firewall rules
/ ip firewall filter
add chain=input protocol=tcp dst-port=1337 action=add-src-to-address-list address-list=knock \
address-list-timeout=15s comment="" disabled=no
add chain=input protocol=tcp dst-port=7331 src-address-list=knock action= add-src-to-address-list \
address-list=safe address-list-timeout=15m comment="" disabled=no
These rules setup port knocking, it set’s up the example we used above and will add the IP address to the ‘safe’ address-list, this is the address-list used in this firewall to permit full unrestricted access to the router
add chain=input connection-state=established action=accept comment="accept established connection packets" disabled=no
add chain=input connection-state=related action=accept comment="accept related connection packets" disabled=no
add chain=input connection-state=invalid action=drop comment="drop invalid packets" disabled=no
These rules make sure only valid connections are going to the router and will drop any that are invalid.
add chain=input src-address-listddress-list=safe action=accept comment="Allow access to router from known network" disabled=no
This rule is the rule that allows full access to the router for certain IP addresses, This list contains static entries for IP’s you want to always have access and also contains the dynamic IP’s of those added by port knocking if used
add chain=input protocol=tcp psd=21,3s,3,1 action=drop comment="detect and drop port scan connections" disabled=no
add chain=input protocol=tcp connection-limit=3,32 src-address-list=black_list action=tarpit \
comment="suppress DoS attack" disabled=no
add chain=input protocol=tcp connection-limit=10,32 action= add-src-to-address-list \
address-list=black_list address-list-timeout=1d comment="detect DoS attack" disabled=no
These rule’s are a little reactive to DoS and port scanning attempts, port scanning is dropped but a DoS attack is ‘tarpitted’ in that all connection’s are slowed down to increase the resource usage on the attackers device
add chain=input protocol=icmp action=jump jump-target=ICMP comment="jump to chain ICMP" disabled=no
add chain=input action=jump jump-target=services comment="jump to chain services" disabled=no
These 2 rules jump to chains we are about to create, jumping is handy because it allows you to reuse the same rule in different chains (I.e. Input and Forward can jump to the same chain and run the same rules)
add chain=input dst- address-type=broadcast action=accept comment="Allow Broadcast Traffic" disabled=no
Allow Broadcast traffic to the router, this is needed sometimes by things like NTP
add chain=input action=log log-prefix="Filter:" comment="" disabled=no
add chain=input action=drop comment="drop everything else" disabled=no
And this is the rule that deny’s all access to the router, if traffic hasn’t been accepted by once of the rules above then it will be dropped
add chain=ICMP protocol=icmp icmp-options=0:0-255 limit=5,5 action=accept comment="0:0 and limit for 5pac/s" disabled=no
add chain=ICMP protocol=icmp icmp-options=3:3 limit=5,5 action=accept comment="3:3 and limit for 5pac/s" disabled=no
add chain=ICMP protocol=icmp icmp-options=3:4 limit=5,5 action=accept comment="3:4 and limit for 5pac/s" disabled=no
add chain=ICMP protocol=icmp icmp-options=8:0-255 limit=5,5 action=accept comment="8:0 and limit for 5pac/s" disabled=no
add chain=ICMP protocol=icmp icmp-options=11:0-255 limit=5,5 action=accept comment="11:0 and limit for 5pac/s" disabled=no
add chain=ICMP protocol=icmp action=drop comment="Drop everything else" disabled=no
These rules form the ‘ICMP’ chain which we jumped to from input, it limited various ICMP packet to stop people ping flooding you
add chain=services src-address-listddress=127.0.0.1 dst- address=127.0.0.1 action=accept comment="accept localhost" disabled=no
add chain=services protocol=udp dst-port=20561 action=accept comment="allow MACwinbox " disabled=no
add chain=services protocol=tcp dst-port=2000 action=accept comment="Bandwidth server" disabled=no
add chain=services protocol=udp dst-port=5678 action=accept comment=" MT Discovery Protocol" disabled=no
add chain=services protocol=tcp dst-port=161 action=accept comment="allow SNMP" disabled=yes
add chain=services protocol=tcp dst-port=179 action=accept comment="Allow BGP" disabled=yes
add chain=services protocol=udp dst-port=5000-5100 action=accept comment="allow BGP" disabled=yes
add chain=services protocol=udp dst-port=123 action=accept comment="Allow NTP" disabled=yes
add chain=services protocol=tcp dst-port=1723 action=accept comment="Allow PPTP" disabled=yes
add chain=services protocol=gre action=accept comment="allow PPTP and EoIP" disabled=yes
add chain=services protocol=tcp dst-port=53 action=accept comment="allow DNS request" disabled=yes
add chain=services protocol=udp dst-port=53 action=accept comment="Allow DNS request" disabled=yes
add chain=services protocol=udp dst-port=1900 action=accept comment="UPnP" disabled=yes
add chain=services protocol=tcp dst-port=2828 action=accept comment="UPnP" disabled=yes
add chain=services protocol=udp dst-port=67-68 action=accept comment="allow DHCP" disabled=yes
add chain=services protocol=tcp dst-port=8080 action=accept comment="allow Web Proxy" disabled=yes
add chain=services protocol=ipencap action=accept comment="allow IPIP" disabled=yes
add chain=services protocol=tcp dst-port=443 action=accept comment="allow https for Hotspot" disabled=yes
add chain=services protocol=tcp dst-port=1080 action=accept comment="allow Socks for Hotspot" disabled=yes
add chain=services protocol=udp dst-port=500 action=accept comment="allow IPSec connections" disabled=yes
add chain=services protocol=ipsec-esp action=accept comment="allow IPSec" disabled=yes
add chain=services protocol=ipsec-ah action=accept comment="allow IPSec" disabled=yes
add chain=services protocol=udp dst-port=520-521 action=accept comment="allow RIP" disabled=yes
add chain=services protocol=ospf action=accept comment="allow OSPF" disabled=yes
add chain=services action=return comment="" disabled=no
These are the services that we allow ANYone to access, as you can see I’ve disabled most of them by default. The only ones enabled are services I personally feel should always be accessible
- Mac-Telnet
- Bandwidth Test Server
- MT Discovery
All other services should only be enabled if they need to be, running this script on a production router already configured will cause it to drop IPSec, BGP, EOIP and a bunch of other services so I must repeat myself again
Don’t apply this firewall on a production router unmodified – it will break some services
Logging & Syslog
So you’ve got long passwords and a firewall that limit’s access to your router. Everything’s great, you see the “Drop Everything Else” counter rising and you check the logs on the router to make sure nobody’s got in. Trouble is you’re now assuming that the data on your router is accurate and hasn’t been fiddled with, someone could have gotten in somehow, is altering your network and you don’t have a clue because they altered the logs or their access has gone beyond the 100 line storage default of RouterOs logging.
Got you worried yet? I should have, when someone compromises any device on your network you can no longer assume the data it holds is clean. You must assume that everything on that device has been altered or removed. On RouterOs it’s actually very difficult to remove entries in the log without erasing the entire log by default but its not impossible, nothing ever is. We are about to go through RouterOs and change what’s logged and where its logged to, in order to be able to accurately tell what’s going on in your router you need to log some information about changes and login attempts to an outside device
By default RouterOs has the following logging setup
/system logging print
Flags: X - disabled, I - invalid
# TOPICS ACTION PREFIX
0 info memory
1 error memory
2 warning memory
3 critical echo
Which is really bad because if your router suffers a power outage or random reboot you lose all log’s. So the first thing we are going to do is log some things to disk.
Erase all the current logging rules
/system logging print
/system logging remove 0
/system logging remove 1
/system logging remove 2
/system logging remove 3
Setup logging to log some things to disk
/system logging add topics=critical action=disk
/system logging add topics=critical action=echo
/system logging add topics=error action=disk
/system logging add topics=warning action=disk
/system logging add topics=info action=memory
Now the next trouble is that by default RouterOs will only store that last 100 lines in memory or on disk. Depending on the amount of ram and free disk space you should up this, personally I set this to 300 lines in memory and disk for RouterBoards and 1000 for PC routers. You can do this by the following command
/system logging action print
/system logging action set 0 disk-lines=XXX
/system logging action set 1 disk-lines=XXX
Now the router will log something’s to disk, others to memory and you will be able to look back further in the logs on the router
If you look back to the firewall script we put in place you will notice that we set it up to log all the dropped input packets, right now you will see them in memory as they are logged under ‘info’ what we will do now is create another file on the disk to store the firewall hits and alter the logging rules so they get logged to disk but don’t clog up the memory
First we setup the new target
/system logging action add target=disk disk-lines=XXX name=FirewallHits
Then we alter the logging actions to stop the firewall clogging up the log
/system logging print
/system logging set 0 topics=info,!firewall
And now we set it so all the firewall hits get sent to the new target
/system logging add topics=firewall action=FirewallHits
And done, now all the hits your firewall get will be logged to the disk and will no longer clog up your main log files, the last thing left to do with logging is log everything to a remote source, for this you will need a remote server running either windows or *NIX with a Syslog daemon running. I wont go through setting up a Syslog daemon as this is extremely platform specific however it is simple to setup a catchall Syslog daemon.
RouterOs has a built in logging action called ‘remote’ all that you need to do is specify the destination IP address where Syslog is running, we can do this by issuing the following commands
/system logging action print
/system logging action set 3 remote=192.168.0.3:514
Remember to add ‘:514’ to the end of the IP address as this specifies which port to use. Once we have set the IP we can go ahead and add a rule to log everything to the daemon
/system logging add action=remote topics=info,warning,critical,firewall,error prefix="RouterId"
Change the prefix to something that identifies your router and your all done.
With this logging setup in place you are in a better position to know what’s going on in your network and to know that the information you are reading is correct, remember when in doubt check the remote Syslog.
Another thing to remember is that all of this logging setup is useless if you never look at it, get into a routine of looking at the log files everyday. Setting up some advanced traps on your remote Syslog to filter some of the rubbish may make this easier
Under *nix-like OS you should do that (FreeBSD, for example):
1. vi /etc/rc.conf and typed lines below.
syslogd_enable="YES" # Run syslog daemon (or NO).
syslogd_program="/usr/sbin/syslogd" # path to syslogd, if you want a different o
syslogd_flags="" # Flags to syslogd (if enabled).
By default into "syslogd_flags" set "-s" option. Don't forget remove it. The "-a" options are ignored if the "-s" option is also specified. See man syslogd.
2. vi /etc/syslog.conf and typed next:
+@
# syslog settings of current system
+*
#
+
*.* /var/log/mikrotik.log
+*
3. /etc/rc.d/syslogd restart.
It's all.
NTP Sync & Misc.
Time, it’s a funny thing. You may not be aware that your device is running on the wrong time, this can be a real pain when you’re faced with an intrusion and reading the logs you discover they are all out by a few hours. It makes it difficult when your cross checking firewall hits against another device and you have to keep adjusting all the results by a few hours. Also if you place firewall rules or simple queues in place that work only at specific times you will find they will work at strange times
One way of correct this is by use of an external time source via NTP. You can find a list of NTP servers in your region here. Because the RouterOs NTP client works on IP’s directly rather than doing a DNS lookup each time you must enter the NTP server’s in as IP addresses
Before setting up the NTP client you need to make sure your time zone is correct
/system clock set time-zone=+12
Once that’s done you can setup your NTP client
/system ntp client set enabled=yes primary-ntp=192.168.0.2 secondary-ntp=192.168.0.3 mode=unicast
It’s as simple as that! Now you router should always be telling the correct time
Throughout this document I have pushed you to think about security of the entire network even tho this document is for securing a single router. My reasons for this are simple, security is like a chain, we have just secured 1 link in that chain but this is pointless if the link before or after is weak or insecure. You need to look at how you keep your network secure, some questions you might want to ask yourself
- Who has access to our passwords?
- Who has physical access to our hardware?
- Do I know what every device on our network is?
- How can I tell if a new device pops up on our network?
- How long would it take me to notice if a router’s password changed?
There are a lot more questions you should be asking but these should get your thinking. Finally security is not a product nor is it a set of firewall rules and it’s not a 1 time thing either. Good security is an on-going area of managing your network that is often overlooked or neglected, until you are compromised and then you’re under the microscope
Last Words
इ hope you find this useful and not a waste of your time, I like feedback about what I write so feel free to leave some on the talk page Talk:Securing_New_RouterOs_Router These guides aren’t perfect so if you see a flaw or error please feel free to update it and let me know via the talk page
Securing your router
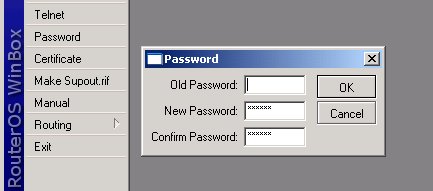
Change admin's password
Just select the Password menu within the winbox GUI, for example:
Or, type the following command in the CLI:
[admin@MikroTik] > / password
old password:
new password: ******
retype new password: ******
This will change your current admin's password to what you have entered twice. Make sure you remember the password! If you forget it, there is no recovery. You need to reinstall the router!
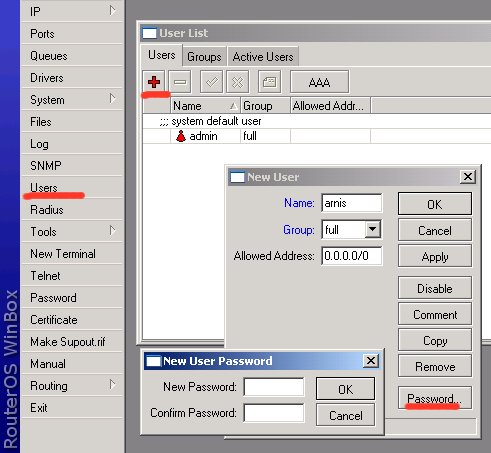
Add users to the system
You should add each user that is going to log on to the router as a separate user and specify group of privileges. Add yourself as user of group full (same as for admin), for example:
You may create new groups for users with specific tasks.
Set up packet filtering
All packets with destination to the router are processed against the ip firewall filter's input chain. Note, that the input chain does not affect packets which are being transferred through the router!
You can add following rules to the input chain under /ip firewall filter (just 'copy and paste' to the router using Terminal Console or configure the relevant arguments in WinBox):
/ ip firewall filter
add chain=input connection-state=established comment="Accept established connections"
add chain=input connection-state=related comment="Accept related connections"
add chain=input connection-state=invalid action=drop comment="Drop invalid connections"
add chain=input protocol=udp action=accept comment="UDP" disabled=no
add chain=input protocol=icmp limit=50/5s,2 comment="Allow limited pings"
add chain=input protocol=icmp action=drop comment="Drop excess pings"
add chain=input protocol=tcp dst-port=22 comment="SSH for secure shell"
add chain=input protocol=tcp dst-port=8291 comment="winbox"
# Edit these rules to reflect your actual IP addresses! #
add chain=input src-address=159.148.172.192/28 comment="From Mikrotikls network"
add chain=input src-address=10.0.0.0/8 comment="From our private LAN"
# End of Edit #
add chain=input action=log log-prefix="DROP INPUT" comment="Log everything else"
add chain=input action=drop comment="Drop everything else"
Use /ip firewall filter print input stats command to see how many packets have been processed against these rules. Use reset-counters-all command to reset the counters. Examine the system log file /log print to see the packets which have been dropped.
You may need to include additional rules to allow access from certain hosts, etc. Remember that firewall rules are processed in the order they appear on the list! After a rule matches the packet, no more rules are processed for it. After adding new rules, move them up using the move command.
Note, if you mis-configured the firewall and have locked yourselves out from the router, you may use MAC telnet from another router or workstation on the same LAN to connect to your router and correct the problem.
Limit Different Bandwidth In Day and Night
Limit Different Bandwidth In Day and Night.
There are lot many ways to limit bandwidth for day and Night, but personally I found this is the easiest way, Here it is.
I have used Simple Queue, Script and Scheduler.
Suppose we have one network 192.168.1.0/24 and want to limit Bandwidth for day and Night Time.
Network 192.168.1.0/24
Bandwidth = 06:00am – 18:00pm – 1Mbps.
Bandwidth = 18:00pm – 06:00am – 2Mbps.
Create two simple queues for the same network with different Bandwidth Limit.
/queue simple
#name=”Day” target-addresses=192.168.1.0/24 dst-address=0.0.0.0/0
interface=parent=none direction=both priority=8
queue=default-small/default-small limit-at=512k/512k
max-limit=1M/1M total-queue=default-small
#name=”Night” target-addresses=192.168.1.0/24 dst-address=0.0.0.0/0
interface=parent=none direction=both priority=8
queue=default-small/default-small limit-at=1M/1M
max-limit=2M/2M total-queue=default-small
Now, write scripts
/system script
#name=”Day” source=/queue simple enable Day; /queue simple disable Night
#name=”Night” source=/queue simple enable Night; /queue simple disable Day
Finally, Schedule it
/system scheduler
#name=”Day” on-event=Day start-date=oct/13/2007 start-time=06:00:00 interval=1d
#name=”Night” on-event=Night start-date=oct/13/2007 start-time=18:00:00 interval=1d
Queue Tree with more than two interfaces
Basic Setup
This page will tak about how to make QUEUE TREE in RouterOS that with Masquerading for more than two interfaces. It's for sharing internet connection among users on each interfacess. In manual this possibility isn't writted.
First, let's set the basic setting first. I'm using a machine with 3 or more network interfaces:
[admin@instaler] > in pr
# NAME TYPE RX-RATE TX-RATE MTU
0 R public ether 0 0 1500
1 R wifi1 wlan 0 0 1500
2 R wifi2 wlan 0 0 1500
3 R wifi3 wlan 0 0 1500
And this is the IP Addresses for each interface:
[admin@instaler] > ip ad pr
Flags: X - disabled, I - invalid, D - dynamic
# ADDRESS NETWORK BROADCAST INTERFACE
0 10.20.1.0/24 10.20.1.0 10.20.1.255 public
1 10.10.2.0/24 10.10.2.0 10.10.2.255 wifi1
2 10.10.3.0/24 10.10.3.0 10.10.3.255 wifi2
3 10.10.4.0/24 10.10.4.0 10.10.4.255 wifi3
On the public you can add NAT or proxy if you want.
Mangle Setup
And now is the most important part in this case.
We need to mark our users. One connection for upload and second for download. In this example I add mangle for one user. At the end I add mangle for local transmission because I don't QoS local trafic emong users. But for user I need to separate upload and download.
[admin@instaler] ip firewall mangle> print
Flags: X - disabled, I - invalid, D - dynamic
disabled=no
0 chain=forward src-address=10.10.2.36 action=mark-connection \
new-connection-mark=users-userU passthrough=yes comment="" disabled=no
1 chain=forward dst-address=10.10.2.36 action=mark-connection \
new-connection-mark=users-userD passthrough=yes comment="" disabled=no
2 chain=forward connection-mark=users-userU action=mark-packet \
new-packet-mark=userU passthrough=yes comment="" disabled=no
3 chain=forward connection-mark=users-userD action=mark-packet \
new-packet-mark=userD passthrough=yes comment="" disabled=no
98 chain=forward src-address=10.10.0.0/16 dst-address=10.10.0.0/16
action=mark-connection new-connection-mark=users-lokal passthrough=yes
99 chain=forward connection-mark=users-lokal action=mark-packet
new-packet-mark=lokalTrafic passthrough=yes
Queue Tree Setup
And now, the queue tree setting. We need one rule for downlink and one rule for uplink. Be careful when choosing the parent. for downlink traffic, we use parent "global-out", because we have two or more downloading interfaces. And for uplink, we are using parent "public", we want QoS uplink traffic. (I'm using pcq-up and download from manual) This example is for 2Mb/1Mb
[admin@instaler] > queue tree pr
Flags: X - disabled, I - invalid
0 name="Download" parent=global-out packet-mark="" limit-at=0
queue=pcq-download priority=1 max-limit=2000000 burst-limit=0
burst-threshold=0 burst-time=0s
1 name="Upload" parent=WGW packet-mark="" limit-at=0 queue=pcq-upload
priority=1 max-limit=1000000 burst-limit=0 burst-threshold=0
burst-time=0s
Now we add our user:
2 name="user10D" parent=Download packet-mark=userD limit-at=0
queue=pcq-download priority=5 max-limit=0 burst-limit=0
burst-threshold=0 burst-time=0s
3 name="user10U" parent=Upload packet-mark=userU limit-at=0
queue=pcq-upload priority=5 max-limit=0 burst-limit=0 burst-threshold=0
burst-time=०स्
source = http://wiki.mikrotik.com
Queue with Masquerading and Internal Web-Proxy
Introduction
This page will tak about how to make QUEUE TREE in RouterOS that also running Web-Proxy and Masquerading. Several topics in forum say it's impossible to do.
In version 2.9.x, we can not know which traffic is HIT and which traffic is MISS from web-proxy. Several people want to make a configuration, to let cache data in proxy (HIT traffic) deliver in maximum possible speed. In other word, if we already have the requested data, those process will not queued.
In ver 3.0 we can do this, using TOS header modification in web-proxy feature. We can set any TOS value for the HIT traffic, and make it as parameter in mangle.
Basic Setup
First, let's set the basic setting first. I'm using a machine with 2 network interface:
admin@instaler] > in pr
# NAME TYPE RX-RATE TX-RATE MTU
0 R public ether 0 0 1500
1 R lan wlan 0 0 1500
And this is the IP Address for each interface:
[admin@instaler] > ip ad pr
Flags: X - disabled, I - invalid, D - dynamic
# ADDRESS NETWORK BROADCAST INTERFACE
0 192.168.0.217/24 192.168.0.0 192.168.0.255 public
1 172.21.1.1/24 172.21.1.0 172.21.1.255 lan
Don't forget to set the transparant web-proxy. We set cache-hit-dscp: 4.
[admin@instaler] > ip proxy pr
enabled: yes
src-address: 0.0.0.0
port: 3128
parent-proxy: 0.0.0.0
parent-proxy-port: 0
cache-drive: system
cache-administrator: "webmaster"
max-cache-size: none
cache-on-disk: yes
maximal-client-connections: 600
maximal-server-connections: 600
max-fresh-time: 3d
serialize-connections: yes
cache-hit-dscp: 4
Firewall NAT
Make 2 NAT rules, 1 for Masquerading, and the other for redirecting transparant proxy.
[admin@instaler] ip firewall nat> pr
Flags: X - disabled, I - invalid, D - dynamic
0 chain=srcnat out-interface=public
src-address=172.21.1.0/24 action=masquerade
1 chain=dstnat in-interface=lan src-address=172.21.1.0/24
protocol=tcp dst-port=80 action=redirect to-ports=3128
Mangle Setup
And now is the most important part in this case.
If we want to make HIT traffic from web proxy not queued, we have to make a mangle to handle this traffic. Put this rule on the beginning of the mangle, as it will check first.
[admin@instaler] > ip firewall mangle print
Flags: X - disabled, I - invalid, D - dynamic
0 ;;; HIT TRAFFIC FROM PROXY
chain=output out-interface=lan
dscp=4 action=mark-packet
new-packet-mark=proxy-hit passthrough=no
As we will make Queue for uplink and downlink traffic, we need 2 packet-mark. In this example, we use "test-up" for uplink traffic, and "test-down" for downlink traffic.
For uplink traffic, it's quite simple. We need only one rule, using SRC-ADDRESS and IN-INTERFACE parameters, and using PREROUTING chain. Rule number #1.
But for downlink, we have to make sevaral rules. As we use masquerading, we need Connection Mark, named as "test-conn". Rule no #2.
Then we have to make 2 more rules. First rule is for non-HTTP connection / direct connection. We use chain forward, as the data traveling through the router. Rule no #3.
The second rule is for data coming from web-proxy to the client (MISS traffic). We use OUTPUT chain, as the data coming from internal process in the router itself. Rule no #4.
For both rules (no #3 and #4) we named it "test-down".
Please be aware, we use passthrough only for connection mark (rule no #2).
[admin@instaler] > ip firewall mangle print
Flags: X - disabled, I - invalid, D - dynamic
1 ;;; UP TRAFFIC
chain=prerouting in-interface=lan
src-address=172.21.1.0/24 action=mark-packet
new-packet-mark=test-up passthrough=no
2 ;;; CONN-MARK
chain=forward src-address=172.21.1.0/24
action=mark-connection
new-connection-mark=test-conn passthrough=yes
3 ;;; DOWN-DIRECT CONNECTION
chain=forward in-interface=public
connection-mark=test-conn action=mark-packet
new-packet-mark=test-down passthrough=no
4 ;;; DOWN-VIA PROXY
chain=output out-interface=lan
dst-address=172.21.1.0/24 action=mark-packet
new-packet-mark=test-down passthrough=no
Queue Tree Setup
And now, the queue tree setting. We need one rule for downlink and one rule for uplink. Be careful when choosing the parent. for downlink traffic, we use parent "lan", the interface name for local network. And for uplink, we are using parent "global-in".
[admin@instaler] > queue tree pr
Flags: X - disabled, I - invalid
0 name="downstream" parent=lan packet-mark=test-down
limit-at=32000 queue=default priority=8
max-limit=32000 burst-limit=0
burst-threshold=0 burst-time=0s
1 name="upstream" parent=global-in
packet-mark=test-up limit-at=32000
queue=default priority=8
max-limit=32000 burst-limit=0
burst-threshold=0 burst-time=0s
You can use those mangle also with PCQ।
source = http://wiki.mikrotik.com